A Virtual Private Network is a technology solution used to provide privacy and security for inter-network connections. The most well-known case consists of people connecting to a remote server with traffic going through a public or insecure network (such as the Internet).
Picture the following scenarios:
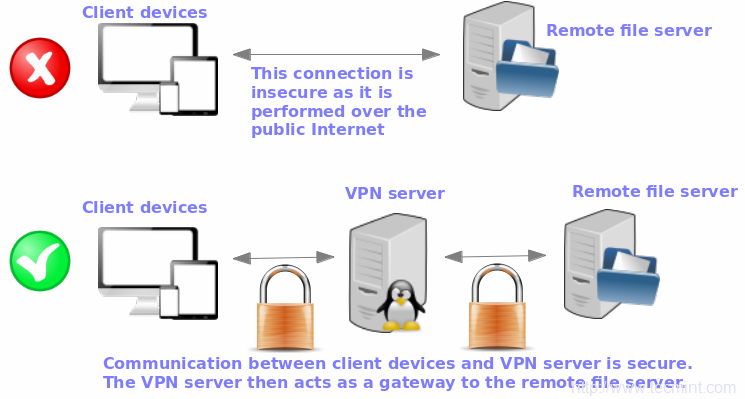
In this article, we will explain how to set up a VPN server in an RHEL/CentOS 8/7 box using OpenVPN, a robust and highly flexible tunneling application that uses encryption, authentication, and certification features of the OpenSSL library. For simplicity, we will only consider a case where the OpenVPN server acts as a secure Internet gateway for a client.
For this setup, we’ve used three machines, the first one acts as an OpenVPN server, and the other two (Linux and Windows) act as a client to connect to remote OpenVPN Server.
On this page
Note: The same instructions also work on RHEL 8/7 and Fedora systems.
Installing OpenVPN Server in CentOS 8
1. To install OpenVPN in an RHEL/CentOS 8/7 server, you will first have to enable the EPEL repository and then install the package. This comes with all the dependencies needed to install the OpenVPN package.
# yum update # yum install epel-release
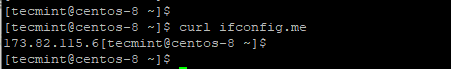
2. Next, we will download OpenVPN’s installation script and set up the VPN. Before downloading and running the script, it’s important that you find your server’s Public IP address as this will come in handy when setting up the OpenVPN server.
An easy way to do that is to use the curl command as shown:
$ curl ifconfig.me
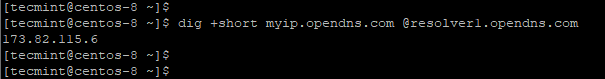
Alternatively, you can invoke the dig command as follows:
$ dig +short myip.opendns.com @resolver1.opendns.com
If you get into an error “dig: command not found” install the dig utility by running the command:
$ sudo yum install bind-utils
This should resolve the problem.
A Note About Public IP Addresses
Cloud servers will usually have 2 types of IP addresses:
- A single Public IP address: If you have a VPS on Cloud platforms such as Linode, Cloudcone, or Digital Ocean, you will usually find a single Public IP address attached to it.
- A private IP address behind NAT with a public IP: This is the case with an EC2 instance on AWS or a compute instance on Google Cloud.
Whichever the IP addressing scheme, the OpenVPN script will automatically detect your VPS network setup and all you have to do is to provide the associated Public or Private IP address.
3. Now let’s proceed and download the OpenVPN installation script, run the command shown.
$ wget https://raw.githubusercontent.com/Angristan/openvpn-install/master/openvpn-install.sh
4. When the download is complete, assign execute permissions and run the shell script as shown.
$ sudo chmod +x openvpn-install.sh $ sudo ./openvpn-install.sh
The installer takes you through a series of prompts:
5. First, you will be prompted to provide your server’s public IP address. Thereafter, it’s recommended to go with the default options such as default port number (1194) and protocol to use (UDP).
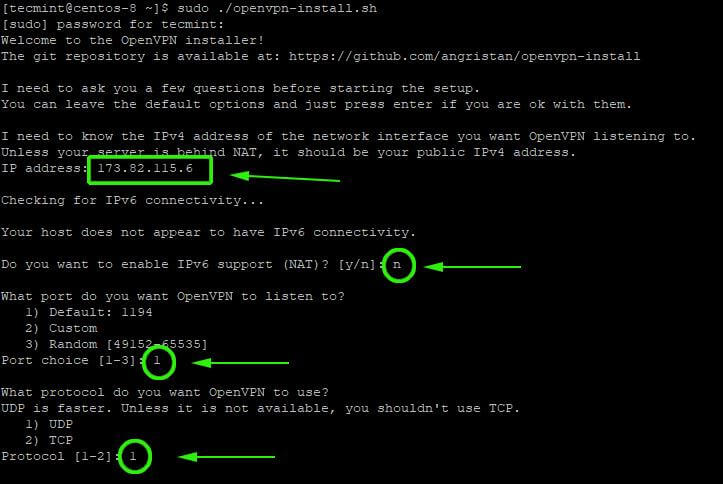
6. Next, select the default DNS resolvers and select the No option ( n ) for both compression and encryption settings.
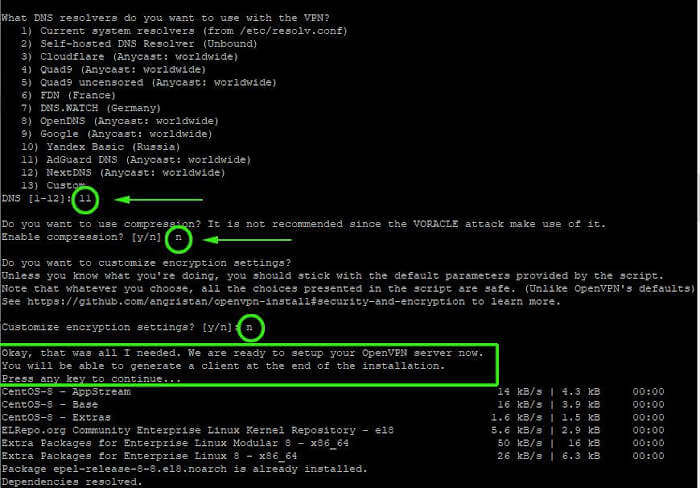
7. Once done, the script will initialize the setup of the OpenVPN server along with the installation of the other software packages and dependencies.
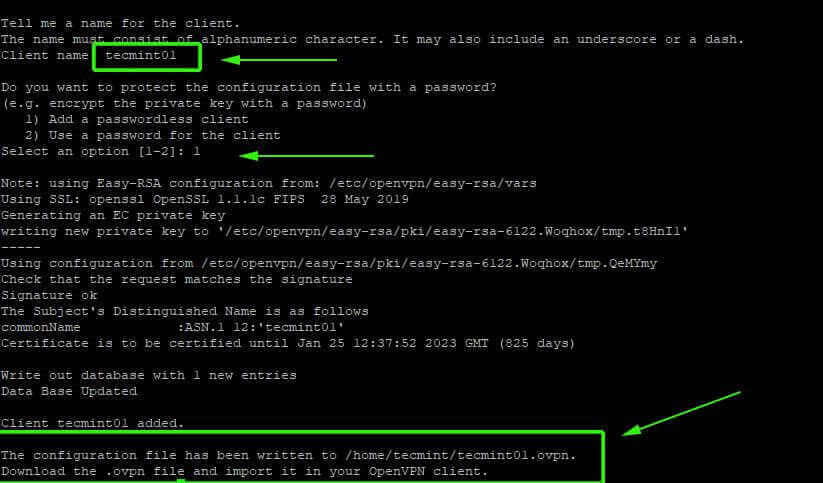
8. Lastly, a client configuration file will be generated using the easy-RSA package which is a command-line tool used for managing security certificates.
Simply provide the name of the client and go with the default selections. The client file will be stored in your home directory with a .ovpn file extension.
9. Once the script is done setting up the OpenVPN server and creating the client configuration file, a tunnel interface tun0 will be spawned. This is a virtual interface where all traffic from the client PC will be tunnelled to the server.
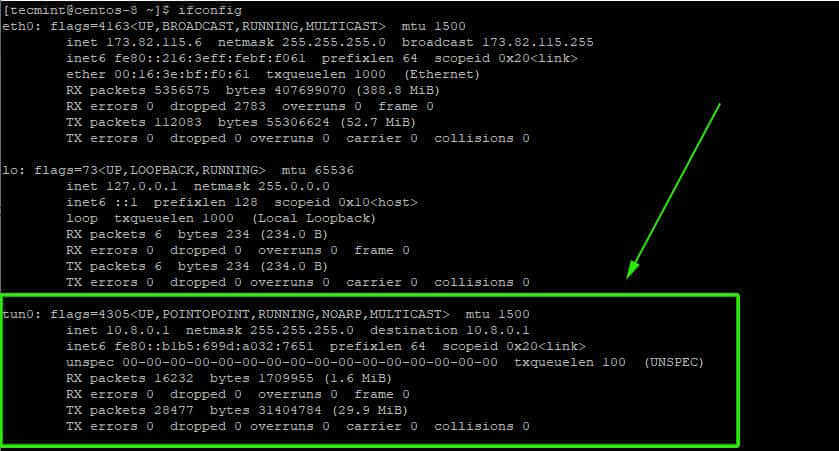
10. Now, you can start and check the status of the OpenVPN server as shown.
$ sudo systemctl start [email protected] $ sudo systemctl status [email protected]
How to Configure OpenVPN Client in Linux
11. Now head over to the client system and install EPEL repository and OpenVPN software packages.
$ sudo dnf install epel-release -y $ sudo dnf install openvpn -y
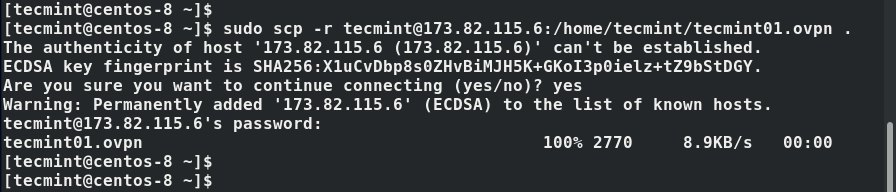
12. Once installed, you need to copy the client configuration file from the OpenVPN server to your client system. You can do this using the scp command as shown
$ sudo scp -r [email protected]:/home/tecmint/tecmint01.ovpn .
13. Once the client file is downloaded to your Linux system, you can now initialize a connection to the VPN server, using the command:
$ sudo openvpn --config tecmint01.ovpn
You will get output similar to what we have below.
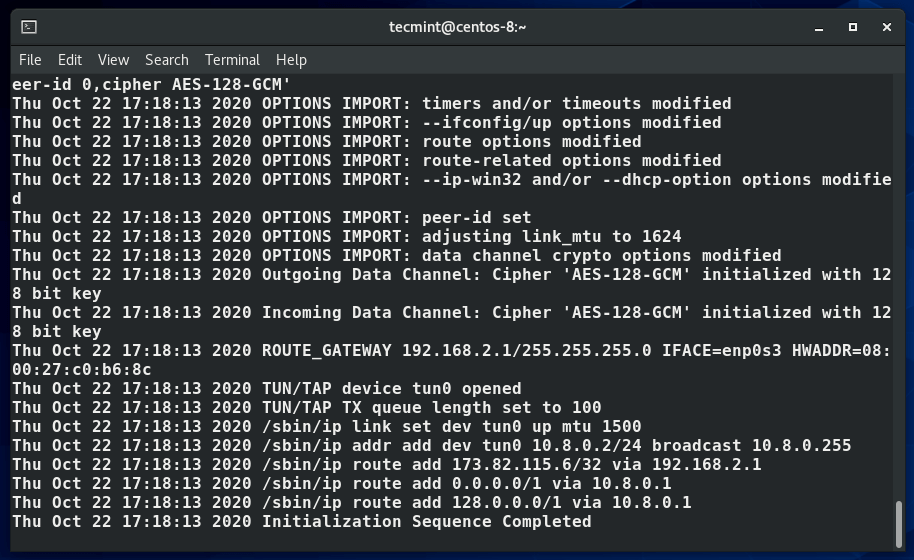
14. A new routing table is created and a connection is established with the VPN server. Again, a virtual interface tunnel interface tun0 is created on the client system.
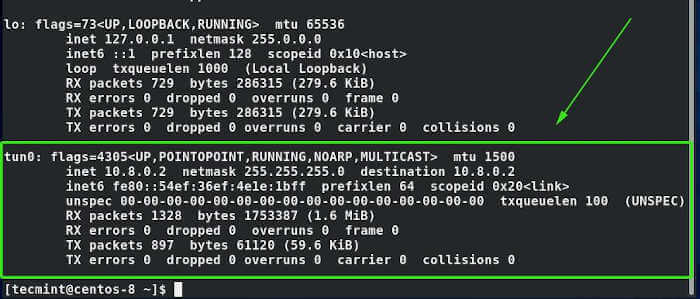
As mentioned earlier, this is the interface that will tunnel all traffic securely to the OpenVPN server via an SSL tunnel. The interface is assigned an IP address dynamically by the VPN server. As you can see, our client Linux system has been assigned an IP address of 10.8.0.2 by the OpenVPN server.
$ ifconfig
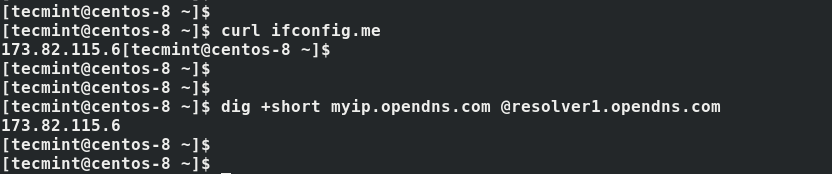
15. Just to be certain that we are connected to the OpenVPN server, we are going to verify the public IP.
$ curl ifconfig.me
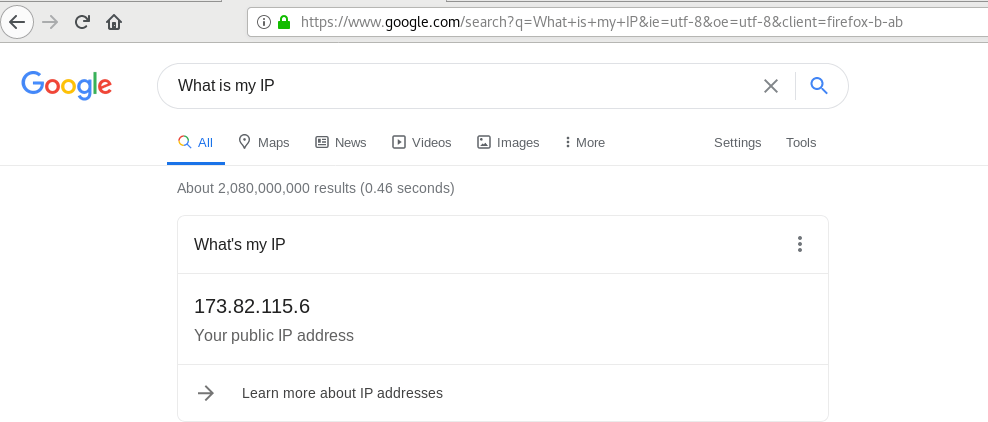
And voila! our client system has picked the VPN’s public IP confirming that indeed we are connected to the OpenVPN server. Alternatively, you can fire up your browser and Google search “What is my IP address” to confirm that your public IP has changed to that of the OpenVPN server.
How to Configure OpenVPN Client on Windows
16. On Windows, you will need to download the official OpenVPN Community Edition binaries that come with a GUI.
17. Next, download your .ovpn configuration file into the C:\Program Files\OpenVPN\config directory and as an Administrator, start OpenVPN GUI from Start –> All programs –> OpenVPN, and it will be launched in the background.
18. Now fire up a browser and open http://whatismyip.org/ and you should see the IP of your OpenVPN server instead of the public IP provided by your ISP:
Summary
In this article, we have explained how to set up and configure a VPN server using OpenVPN, and how to set up two remote clients (a Linux box and a Windows machine). You can now use this server as a VPN gateway to secure your web browsing activities. With a little extra effort (and another remote server available) you can also set up a secure file/database server, to name a few examples.
We look forward to hearing from you, so feel free to drop us a note using the form below. Comments, suggestions, and questions about this article are most welcome.



Hello,
I have setup the OpenVPN however whenever I connect to the VPN, I cannot access my internal network appliances. How can I get this working?
Please advise.
@Imtiaz,
Configure routing on the OpenVPN server to allow traffic between the VPN subnet and the internal network.
How can I add more clients VPN?
is there is a script?
Run the script again and select add client.
How many clients can this OpenVPN server support at the same time?
@Weng,
The OpenVPN server can handle 500 user accounts, but only license it for 100 connections.
Why you skip important moments about firewalls?
How to open port and redirect tun0 to eth0 for the internet? without it I can connect to vpnserver, but there is no internet.
Please help me.
Sample Output
● [email protected] - OpenVPN service for server
Loaded: loaded (/etc/systemd/system/[email protected]; enabled; vendor>
Active: active (running) since Tue 2020-10-27 10:30:47 +05; 1min 38s ago
Docs: man:openvpn(8)
https://community.openvpn.net/openvpn/wiki/Openvpn24ManPage
https://community.openvpn.net/openvpn/wiki/HOWTO
Main PID: 63764 (openvpn)
Status: "Initialization Sequence Completed"
Tasks: 1 (limit: 23956)
Memory: 1.5M
CGroup: /system.slice/system-openvpn\x2dserver.slice/[email protected]>
└─63764 /usr/sbin/openvpn --status /run/openvpn-server/status-server>
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: Could not determine IPv4/IPv6 protoco>
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: Socket Buffers: R=[212992->212992] S=>
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: UDPv4 link local (bound): [AF_INET][u>
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: UDPv4 link remote: [AF_UNSPEC]
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: GID set to nobody
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: UID set to nobody
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: MULTI: multi_init called, r=256 v=256
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: IFCONFIG POOL: base=10.8.0.2 size=252>
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: IFCONFIG POOL LIST
Oct 27 10:30:47 ubtuitvpn openvpn[63764]: Initialization Sequence Completed
lines 1-23/23 (END)
Can you give us some commands or guide to managing user restrictions over network clients?
How many clients can this OpenVPN server support at the same time???
Excellent article, helping me learn about OpenVPN and certificates, thanks.
Failed to start OpenVPN Robust And Highly Flexible Tunneling Application On server. not able to start openvpn services
After executing below command, getting following error..
Job for [email protected] failed because the control process exited with error code. See “systemctl status [email protected]” and “journalctl -xe” for details.
Failed to start OpenVPN Robust And Highly Flexible Tunneling Application On server.
Fedora have simplified how this works now but NOWHERE seems to have bothered to document it.
You put server.conf files into /etc/openvpn/server/ and clients into /etc/openvpn/client/. This way you can easily enable/disable them without changing the service file.
Simply issue systemctl enable openvpn-server@config where the bit after the @ is the name of your conf file without the conf at the end.
Great walkthrough thanks a lot!
One question:
Where do client.ca and client.key come from? do I have to generate them on my client (windows)?
Thanks
Got it.
On the second page instead of downloading the server.crt and server.key to my client I should have downloaded the client.crt/key I generated earlier. Makes sense.
[root@testing-1 keys]# systemctl -l status openvvpn@server
Unit [email protected] could not be found.
[root@testing-1 keys]# systemctl -l status openvvpn@testing-1
Unit [email protected] could not be found.
[root@testing-1 keys]# systemctl -l status [email protected]
Unit [email protected] could not be found.
Did you notice there’s a typo in your command? It’s openvpn, not openvvpn.
[root@localhost user]# yum install openvpn
Loaded plugins: fastestmirror, langpacks
Loading mirror speeds from cached hostfile
* base: mirrors.vooservers.com
* extras: mirror.vorboss.net
* updates: mirror.mhd.uk.as44574.net
No package openvpn available.
Error: Nothing to do
@Big Ian,
Have you installed epel-release package on the system? if not first install it as shown:
Once epel installed, you can install openvpn.
I would use this Script from nyr. In my opinion is this the best alternative.
https://github.com/Nyr/openvpn-install
-derpadi49
Small typo:
cp ca.crt server.crt server.key /../.. (should be “../../”)
Please I am looking for how to install Open VPN Server on Linux, I want to run my computer..
ca somethingelse.crt <—– shouldn't this be ca.crt?
cert somethingelse.crt
key somethingelse.key
@testsubject,
I am not really sure exactly what part of this article you are referring to. Please clarify (section and exact command where you see the error).
Here is an even quicker way of doing this that creates the Endpoint in any AWS region on demand. https://github.com/ttlequals0/autovpn
Obsolete already
Nice article!
Would love to see add user account, and point into different vlan
Hi,
is there an error in that sentence?
To set up a client (regardless of the distribution or operating system) you will need to copy the ca.crt, server.crt, and server.key files from /etc/openvpn/rsa/keys.
wouldn’t be the client.crt and client.key files copied instead?
journalctl –xn must be written with one dash, at least it is in Fedora. Double dash is not recognized