To overcome the limitations of and to increase the security mechanisms provided by standard ugo/rwx permissions and access control lists, the United States National Security Agency (NSA) devised a flexible Mandatory Access Control (MAC) method known as SELinux (short for Security Enhanced Linux) in order to restrict among other things, the ability of processes to access or perform other operations on system objects (such as files, directories, network ports, etc) to the least permission possible, while still allowing for later modifications to this model.
and AppArmor Security Hardening Linux
Another popular and widely-used MAC is AppArmor, which in addition to the features provided by SELinux, includes a learning mode that allows the system to “learn” how a specific application behaves, and to set limits by configuring profiles for safe application usage.
In CentOS 7, SELinux is incorporated into the kernel itself and is enabled in Enforcing mode by default (more on this in the next section), as opposed to openSUSE and Ubuntu which use AppArmor.
In this article we will explain the essentials of SELinux and AppArmor and how to use one of these tools for your benefit depending on your chosen distribution.
Introduction to SELinux and How to Use it on CentOS 7
Security Enhanced Linux can operate in two different ways:
- Enforcing: SELinux denies access based on SELinux policy rules, a set of guidelines that control the security engine.
- Permissive: SELinux does not deny access, but denials are logged for actions that would have been denied if running in enforcing mode.
SELinux can also be disabled. Although it is not an operation mode itself, it is still an option. However, learning how to use this tool is better than just ignoring it. Keep it in mind!
To display the current mode of SELinux, use getenforce. If you want to toggle the operation mode, use setenforce 0 (to set it to Permissive) or setenforce 1 (Enforcing).
Since this change will not survive a reboot, you will need to edit the /etc/selinux/config file and set the SELINUX variable to either enforcing, permissive, or disabled in order to achieve persistence across reboots:
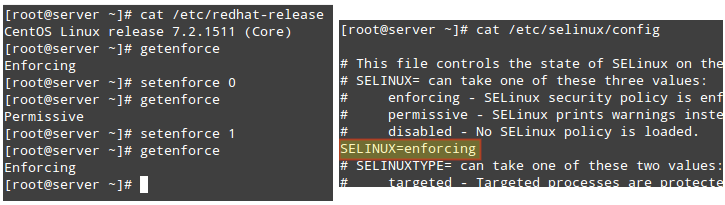
On a side note, if getenforce returns Disabled, you will have to edit /etc/selinux/config with the desired operation mode and reboot. Otherwise, you will not be able to set (or toggle) the operation mode with setenforce.
One of the typical uses of setenforce consists of toggling between SELinux modes (from enforcing to permissive or the other way around) to troubleshoot an application that is misbehaving or not working as expected. If it works after you set SELinux to Permissive mode, you can be confident you’re looking at a SELinux permissions issue.
Two classic cases where we will most likely have to deal with SELinux are:
- Changing the default port where a daemon listens on.
- Setting the DocumentRoot directive for a virtual host outside of /var/www/html.
Let’s take a look at these two cases using the following examples.
EXAMPLE 1: Changing the default port for the sshd daemon
One of the first thing most system administrators do in order to secure their servers is change the port where the SSH daemon listens on, mostly to discourage port scanners and external attackers. To do this, we use the Port directive in /etc/ssh/sshd_config followed by the new port number as follows (we will use port 9999 in this case):
Port 9999
After attempting to restart the service and checking its status we will see that it failed to start:
# systemctl restart sshd # systemctl status sshd
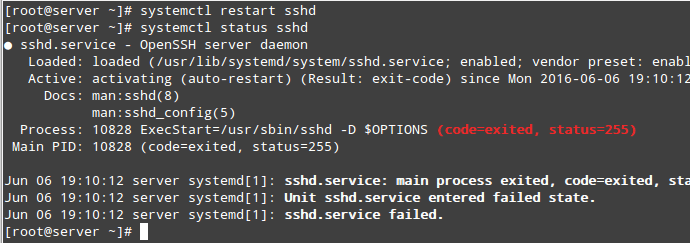
If we take a look at /var/log/audit/audit.log, we will see that sshd was prevented from starting on port 9999 by SELinux because that is a reserved port for the JBoss Management service (SELinux log messages include the word “AVC” so that they might be easily identified from other messages):
# cat /var/log/audit/audit.log | grep AVC | tail -1

At this point most people would probably disable SELinux but we won’t. We will see that there’s a way for SELinux, and sshd listening on a different port, to live in harmony together. Make sure you have the policycoreutils-python package installed and run:
# yum install policycoreutils-python
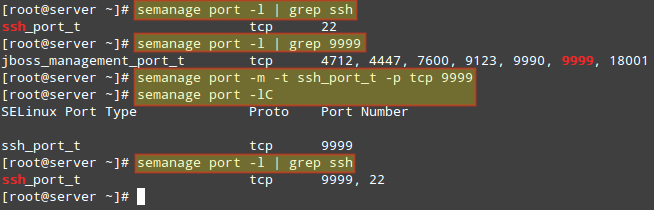
To view a list of the ports where SELinux allows sshd to listen on. In the following image we can also see that port 9999 was reserved for another service and thus we can’t use it to run another service for the time being:
# semanage port -l | grep ssh
Of course we could choose another port for SSH, but if we are certain that we will not need to use this specific machine for any JBoss-related services, we can then modify the existing SELinux rule and assign that port to SSH instead:
# semanage port -m -t ssh_port_t -p tcp 9999
After that, we can use the first semanage command to check if the port was correctly assigned, or the -lC options (short for list custom):
# semanage port -lC # semanage port -l | grep ssh
We can now restart SSH and connect to the service using port 9999. Note that this change WILL survive a reboot.
EXAMPLE 2: Choosing a DocumentRoot outside /var/www/html for a virtual host
If you need to set up a Apache virtual host using a directory other than /var/www/html as DocumentRoot (say, for example, /websrv/sites/gabriel/public_html):
DocumentRoot “/websrv/sites/gabriel/public_html”
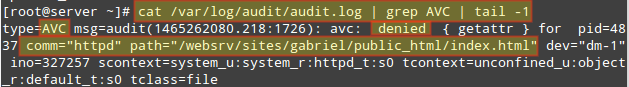
Apache will refuse to serve the content because the index.html has been labeled with the default_t SELinux type, which Apache can’t access:
# wget http://localhost/index.html # ls -lZ /websrv/sites/gabriel/public_html/index.html

As with the previous example, you can use the following command to verify that this is indeed a SELinux-related issue:
# cat /var/log/audit/audit.log | grep AVC | tail -1
To change the label of /websrv/sites/gabriel/public_html recursively to httpd_sys_content_t, do:
# semanage fcontext -a -t httpd_sys_content_t "/websrv/sites/gabriel/public_html(/.*)?"
The above command will grant Apache read-only access to that directory and its contents.
Finally, to apply the policy (and make the label change effective immediately), do:
# restorecon -R -v /websrv/sites/gabriel/public_html
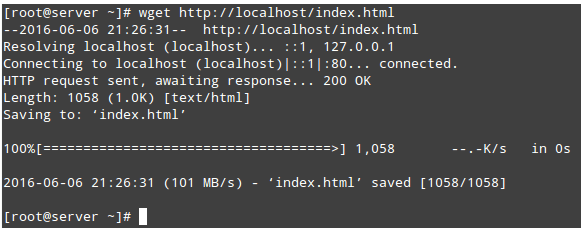
Now you should be able to access the directory:
# wget http://localhost/index.html
For more information on SELinux, refer to the Fedora 22 SELinux and Administrator guide.







semanage fcontext -a -t httpd_sys_content_t ‘/websrv/sites/gabriel/public_html(/.*)?’
Instead of using double quotation we have to use single quotations while changing the context of the file index.html
Thanks for another great write-up Gabriel. There isn’t much out there on AppArmor and how it may apply to the LFCS exam and your article is a huge help. I’d like to add that as of Ubuntu 16.04, in order to run the commands aa-enforce and aa-complain, you’ll need to first install the package named apparmor-utils.
Once this package is installed, it also provides the command aa-status, which does the same thing as apparmor_status.
Thanks again!
Very useful, thanks.
Do you also need to use restorecon to apply the policy change for the SSH example?
I’ve recently encountered an instance of SELinux blocking access to krb5.conf when trying to setup and configure Kerberos authentication (CentOS 7). At the time I wasn’t aware of SELinux, and rebooting the server had no effect on updating the newly installed packages.
I was unable to log in physically or SSH in with a Kerberos user account, but could use SU to switch to a Kerberos user account if I logged into a local account first. This all looked PAM realted.
It turned out that disabling and re-enabling SELinux updated the SELinux policy somehow, so I didn’t leave it disabled or permissive (rebooted, temporarily disabled selinux in grub by applying selinux=0 to the boot line, logged in with an account using Kerberos, then rebooted again without disabling selinux).
I’ll play again in due course with a fresh installation, and see if the commands here reveal anything interesting.
Show Debian/Ubuntu based distributions examples, please.
@Anon,
Debian is not one of the distributions that you can choose to take the exam. In Ubuntu, you can use AppArmor.