The primary application we require to perform our internet activity is a browser, a web browser to be more perfect in terms of privacy and security of online activities.
Over the Internet, most of our’s activity is logged to the Server/Client machine which includes IP address, Geographical Location, search/activity trends, and a whole lot of information that can potentially be very harmful if used intentionally the other way.
Moreover, the National Security Agency (NSA) aka International Spying Agency keeps track of our digital footprints. Not to mention a restricted proxy server which again can be used as a data ripping server is not the answer.
Today, most corporates and companies won’t allow you to access a proxy server, in case a VPN service is a reliable choice for browsing the internet securely and anonymously.
So, what we need here is an application, preferably small in size, and let it stand-alone, portable, and serves the purpose. Here comes an application – the Tor Browser, which has all the above-discussed features and even beyond that.
In this article, we will be discussing the Tor browser, its features, its usages and area of application, installation, and other important aspects of the Tor browser.
What is Tor Browser?
Tor is a freely distributed application software, released under BSD style licensing which allows one to surf the internet anonymously, through its safe and reliable onion-like structure.
Tor previously was called ‘The Onion Router‘ because of its structure and functioning mechanism, which is purely written in C programming Language.
Features of Tor Browser
- Cross-Platform availability. i.e., Tor is available for Linux, Windows as well as Mac.
- Complex data encryption before it is sent over the Internet.
- Automatic data decryption at the client side.
- It is a combination of the Firefox Browser + the Tor Project.
- It provides anonymity to servers and websites.
- It makes it possible to visit locked websites.
- Performs task without revealing the IP of Source.
- Capable of routing data to/from hidden services and applications behind the firewall.
- Portable – Run a pre-configured web browser directly from the USB storage device. No need to install it locally.
- Available for architectures x86 and x86_64.
- Easy to set FTP with Tor using configuration as “socks4a” proxy on “localhost” port “9050”
- Tor is capable of handling thousands of relays and millions of users.
How Does Tor Browser Work?
Tor works on the concept of Onion routing. Onion routing resembles an onion in structure. In onion routing, the layers are nested one over the other similar to the layers of an onion.
This nested layer is responsible for encrypting data several times and sending it through virtual circuits. On the client side, each layer decrypts the data before passing it to the next level. The last layer decrypts the innermost layer of encrypted data before passing the original data to the destination.
In this process of decryption, all the layers function so intelligently that there is no need to reveal the IP and Geographical location of the user thus limiting any chance of anybody watching your internet connection or the sites you are visiting.
All these working seems a bit complex, but the end-user execution and working of the Tor browser is nothing to worry about. In fact, Tor browser resembles any other browser (Especially Mozilla Firefox) in functioning.
How to Install Tor Browser in Linux
As discussed above, the Tor browser is available for Linux, Windows, and Mac. The user needs to download the latest version (i.e. Tor Browser 12.0.6) application from the link below as per their system and architecture.
Alternatively, you can use the following wget command to download the tor browser directly in the command line.
---------------- On 64-Bit System ---------------- $ wget https://dist.torproject.org/torbrowser/12.0.6/tor-browser-linux64-12.0.6_ALL.tar.xz ---------------- On 32-Bit System ---------------- $ wget https://dist.torproject.org/torbrowser/12.0.6/tor-browser-linux32-12.0.6_ALL.tar.xz
After downloading the Tor browser, extract the archive using the tar command and set the execute permission to allow the program to run.
$ tar -xvf tor-browser-linux*
$‘ which means that the package is extracted as a user and not the root. It is strictly suggested to extract and run the tor browser as a regular user.After successful extraction, we can move the extracted browser anywhere in the system or to any USB Mass Storage device and run the application from the extracted folder as a regular user as shown.
$ cd tor-browser/ $ ./start-tor-browser.desktop
Trying to connect to the Tor Network. Click “Connect” and Tor will do the rest of the settings for you.
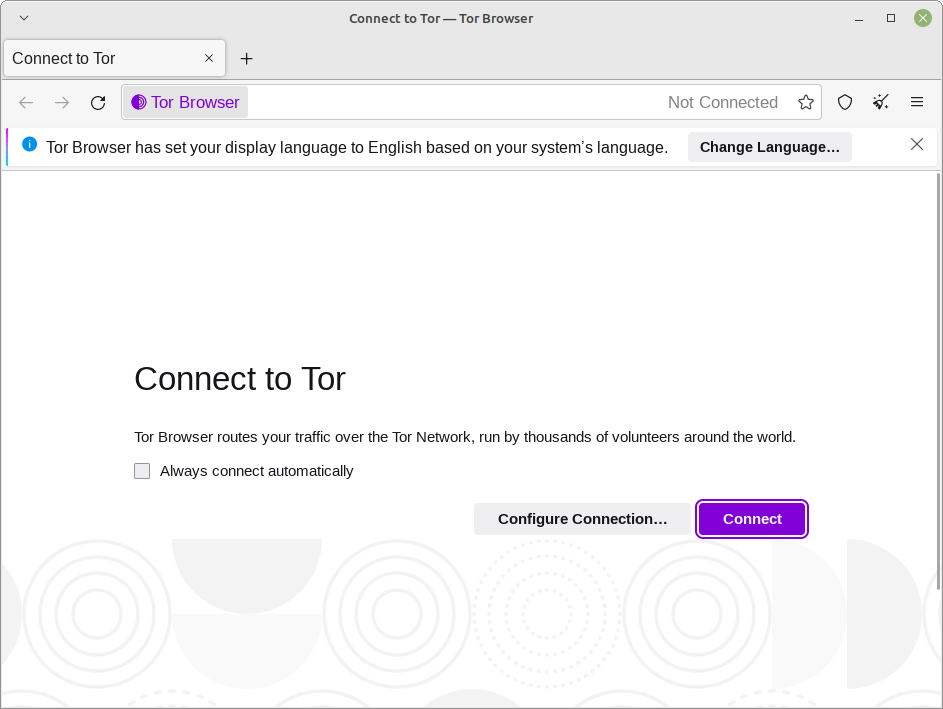
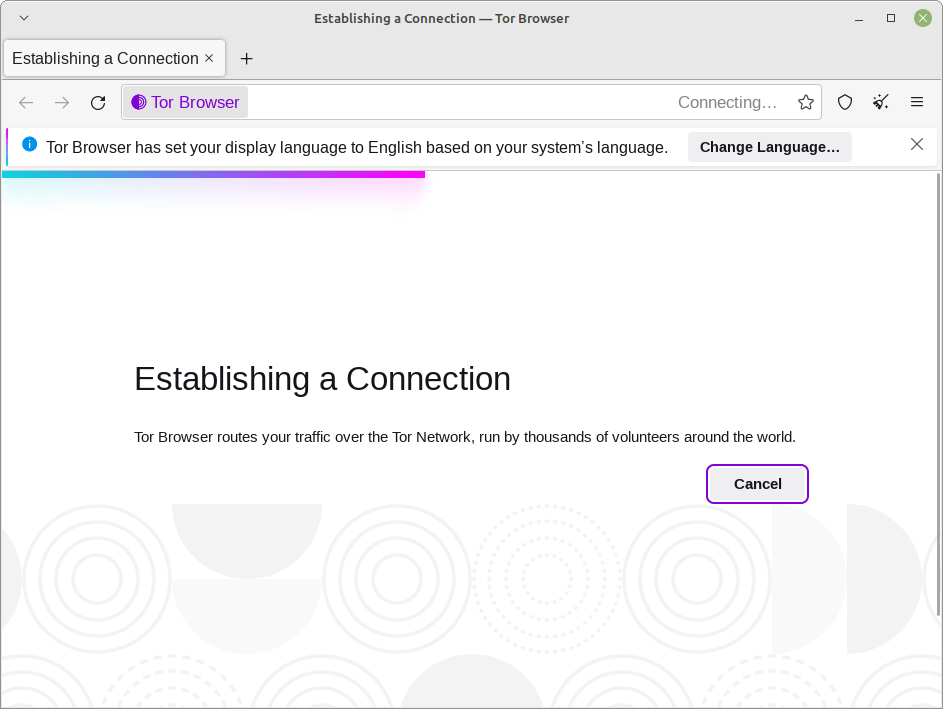
The welcome Window/Tab.
Create Tor Desktop Shortcut in Linux
Remember that you need to point to the Tor startup script using text session, every time you want to run Tor. Moreover, a terminal will be busy all the time until you are running tor. How to overcome this and create a desktop/dock-bar icon?
We need to create tor.desktop the file inside the directory where extracted files reside.
$ touch tor.desktop
Now edit the file using your favorite editor with the text below. Save and exit. I used nano.
$ nano tor.desktop
#!/usr/bin/env xdg-open [Desktop Entry] Encoding=UTF-8 Name=Tor Comment=Anonymous Browse Type=Application Terminal=false Exec=/home/tecmint/Downloads/tor-browser/start-tor-browser.desktop Icon=/home/tecmint/tor-browser/Browser/browser/chrome/icons/default/default128.png StartupNotify=true Categories=Network;WebBrowser;
Once done! double click the file tor.desktop to fire the Tor browser.
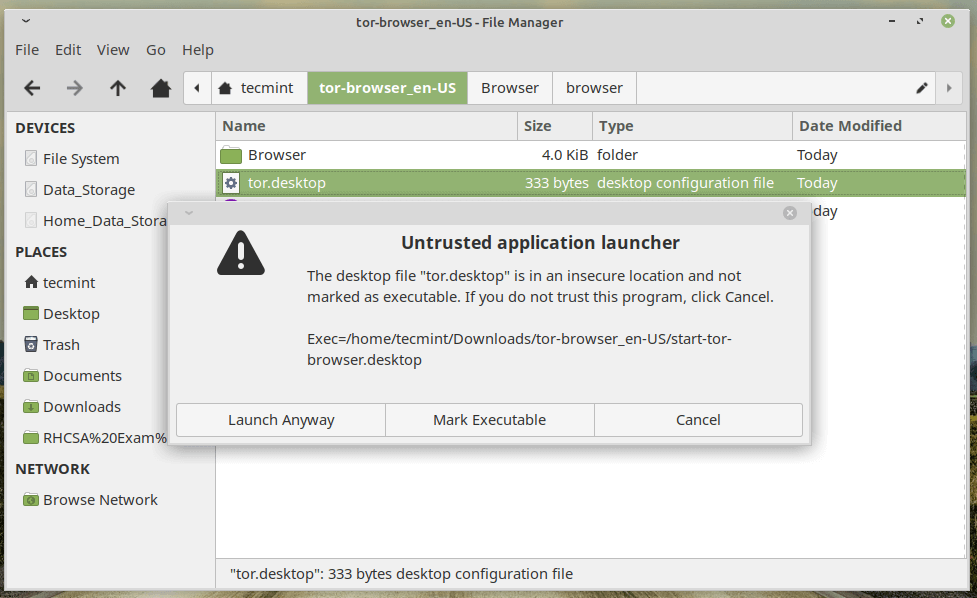
Once you trust you might note that the icon of tor.desktop changed.
You may now copy the tor.desktop icon to create a shortcut on the Desktop and launch it.
If you are using an older version of Tor, you may update it from the About window.
Conclusion
Tor browser is a must-have tool in the present time where the organization you are working for doesn’t allow you to access certain websites if you don’t want others to look into your private business or you don’t want to provide your digital footprints to NSA.
This post is totally for educational purposes and for any illegal use of it, neither the author nor Tecmint will be responsible. It is the sole responsibility of the user.
Tor browser is a wonderful application and you must give it a try. That’s all for now. I’ll be here again with another interesting article you people will love to read.
Till then stay tuned and connected to Tecmint. Don’t forget to provide us with your valuable feedback in our comment section below.





registers the browser to the launcher by creating the .desktop file.
“Tor browser is a must tool in the present time where the organization you are working for doesn’t allow you to access certain websites”
Do you really think that your employer will allow you to install, much less to use, an application that bypasses corporate security? I guarantee you would be fired on the spot. All the companies I have worked for were very particular about the software installed on corporate workstations. In some cases, installing, and using, Firefox or Chrome instead of Internet Explorer was a no-no.
@Dragonmouth,
I agree with your point, but you no need to install it, just download and run it from anywhere or from you pen drive…:)
No matter how you run it, there always will be a record of the execution of the program. Plus the employer can block the execution of certain programs. Even if you use your own laptop, you still may not be able to run Tor since you would have to go through the company network.
“Moreover the National Security Agency (NSA) aka International Spying Agency keeps tracks of ours digital footprints.”
Let’s not single out the NSA. GHCQ in United Kingdom and other governments’ security agencies also do a very good job of spying and keeping track of people’s digital footprints. Just because you happen to live outside the United States don’t labor under the illusion that YOUR electronic activities are not being tracked by your government.
Since i heard the benefits of Tor, I’ve also heard how harmful tor can be. I still make use of it though. Would like to know any alternative to tor.
Tor seems too fishy to me. Instead of using Tor, I’d definitely choose the cheapest VPN like Hide My IP, which at least hides all online activity. On the other hand, Tor keeps cutting and lags a lot.
Do you mean 64-bit. It reads 62 bit and I’m not skilled enough to know whether this is some strange mistake or something that matters. I do know I have a 64 bit OS.
@Stephen,
Sorry, it was a typo..corrected in the write up…
This is why proofreading and research, especially on technology sites, is so important. Novices to the field will be taking this information at face value and then wondering why so many things they thought they had learned are wrong.
If the service a website provides is to educate, proofreading and fact-checking are tantamount to that goal.
Great job..Surely will give this browser a try…
Great job man~
Thanks @ Shaunx,
for this valueable feedback.