Have you ever wondered why there is a special account named root in Linux? Do you know what are the recommended best practices to use this account? Are you aware of the scenarios where it must be used and those where it doesn’t? If you answered “yes” to one or more of these questions, keep reading.
In this post we will provide a reference with information about the root account that you will want to keep handy.
What is root?
To begin, let us keep in mind that the hierarchy of directories in Unix-like operating systems has been designed as a tree-like structure. The starting point is a special directory represented by a forward slash (/) with all other directories initially branching off from it. Since this is analogous to an actual tree, / is called the root directory.
In the following image we can see the output of:
$ tree -d / | less
which illustrates the analogy between / and the root of a tree.

Although the reasons behind the naming of the root account are not quite clear, it is likely due to the fact that root is the only account having write permissions inside /.
Additionally, root has access to all files and commands in any Unix-like operating system and it is often referred to as the superuser for that reason.
On a side note, the root directory (/) must not be confused with /root, which is the home directory of the root user. In fact, /root is a subdirectory of /.
Gaining Access to root Permissions
When we talk about root (or superuser) privileges, we refer to the permissions that such account has on the system. These privileges include (but are not limited to) the ability to modify the system and to grant other users certain access permissions to its resources.
The reckless use of this power can lead to system corruption at best and total failure at worst. That is why the following guidelines are accepted as best practices when it comes to accessing the privileges of the root account:
Initially, use the root account to run visudo. Use that command to edit /etc/sudoers to grant the minimum superuser privileges that a given account (e.g. supervisor) needs.
This may include, for example, the ability to create (adduser) and modify (usermod) user accounts – and nothing else.
Moving forward, login as supervisor and use sudo to perform user management tasks. You will notice that attempting to perform other tasks that require superuser permissions (removing packages, for example) should fail.
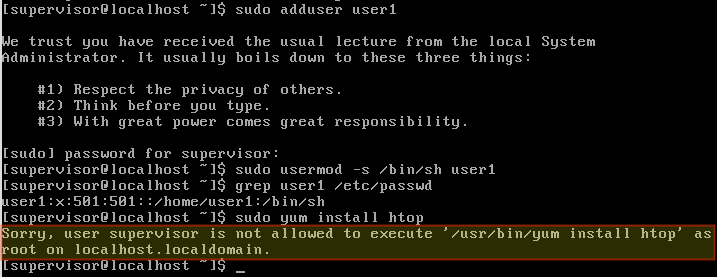
Repeat the above two steps whenever needed, and once done, use the exit command to return to your unprivileged account immediately.
At this point you should ask yourself, Are the any other tasks that pop up on a periodic basis that need superuser privileges? If so, grant the necessary permissions in /etc/sudoers either for a given account or group, and continue avoiding the use of the root account at the extent possible.
Summary
This post can serve as a reference for the proper use of the root account in a Unix-like operating system. Feel free to add it to your bookmarks and return as many times as you want!
As always, drop us a note using the comment form below if you have any questions or suggestions about this article. We look forward to hearing from you!





It is probably called root because all other users derive from it in a tree shape.
I believe you are confusing users with filesystem structure, as explained in this article.
The root user is the user with permissions by default to change ANYTHING in a Linux system. Root is a powerful and dangerous ability in any computer system.
I commonly have a root account and a password that is used only for that account. I then use sudo for installation of software and some other duties. This protects the system from intrusion and suchlike. It also provides some minimal protection from installer scripts that are malicious.
The sudo password can be given for those who need to install software, or a different password for those who need to be able to inspect/read/write to other users accounts. (E.G. supervisors of group accounts.) These sudo accounts are also potentially dangerous, so proper care should be exercised. Root should be used only by the primary administrators.
That said, never Never NEVER have only one person who knows your systems root password. If you do, then you have given that person total control over your system. If they leave for any reason, you might have to reinstall the complete system to fix it. (The legendary “Hit by a Bus” scenario.)
I always create a fully functional root account on my Linux systems. Unfortunately several Linux distributions have decided to protect me from myself by blocking the creation of a fully functional root account as much as possible.
So every time I install a new release of a Linux distribution I have to go into the system control files and undo the damage that the distribution has deliberately done to the root account.
Whether or not to install a root account and let a user log into root on the GUI login screen should be an option at install time.
Steve Stites
So you didn’t answer your own question really, who is root? You are assuming that it’s likely due to the fact that root is the only account having write permissions inside. What a waste of time this reading was.
It is not that way. The question has been answered well. Root is the main user, as Sir Gabriel has said.