When you have important sensitive data, then its crucial to have an extra layer of security to your files and directories, specially when you need to transmit the data with others over a network.
That’s the reason, I am looking for a utility to encrypt and decrypt certain files and directories in Linux, luckily I found a solution that tar with OpenSSL can do the trick, yes with the help of these two tools you can easily create and encrypt tar archive file without any hassle.
Don’t Miss: 7 Tools to Encrypt and Decrypt Files in Linux
In this article, we will see how to create and encrypt a tar or gz (gzip) archive file with OpenSSL:
Remember that the conventional form of using OpenSSL is:
# openssl command command-options arguments
Encrypt Files in Linux
To encrypt the contents of the current working directory (depending on the size of the files, this may take a while):
# tar -czf - * | openssl enc -e -aes256 -out secured.tar.gz
Explanation of the above command:
enc– openssl command to encode with ciphers-e– a enc command option to encrypt the input file, which in this case is the output of the tar command-aes256– the encryption cipher-out– enc option used to specify the name of the out filename, secured.tar.gz
Decrypt Files in Linux
To decrypt a tar archive contents, use the following command.
# openssl enc -d -aes256 -in secured.tar.gz | tar xz -C test
Explanation of the above command:
-d– used to decrypt the files-C– extract in subdirectory named test
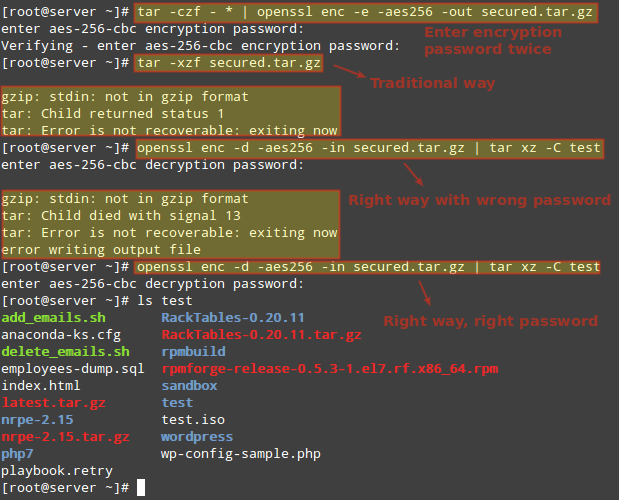
The following image shows the encryption process and what happens when you try to:
- extract the contents of the tarball the traditional way
- use the wrong password, and
- when you enter the right password
When you are working on a local network or the Internet, you can always secure your vital documents or files that you share with others by encrypting them, this can help reduce the risk of exposing them to malicious attackers.
We looked at a simple technique of encrypting tarballs using OpenSSL, a openssl command line tool. You can refer to its man page for more information and useful commands.
As usual, for any additional thoughts or simple tips that you wish to share with us, use the feedback form below and in the upcoming tip, we shall look at a way of translating rwx permissions into octal form.




I am bothered by the comment of Quiark who claims to know something about the security of cryptographic methods, but shows that he knows nothing. Zomegagon references articles implying that openssl is inherently insecure, vs gpg.
However, neither openssl nor gpg are cryptographic methods in themselves. They are front ends that call crypto algorithms from open source crypto libraries, and the user selects the crypto of his choice and the crypto parameters to suite his needs.
These libraries are the gold standards upon which most of the modern internet depends. Unless you believe that closed source, proprietary cryptography is superior to open source cryptography. That argument, (security by obscurity) has been made many times and lost.
This is unsafe. Please don’t write about crypto if you don’t understand it, putting your readers at risk (that probably want to encrypt sensitive data, you know?)
@Quiark,
Please enlighten us and share your wisdom – why is this unsafe in your opinion? An actual proof will be most appreciated. In the true spirit of open source and knowledge sharing, pointing out a flaw without providing a suggestion to improve something isn’t the way to go, you know?
Check these out:
1. https://stackoverflow.com/questions/16056135/how-to-use-openssl-to-encrypt-decrypt-files#16056298
2. https://stackoverflow.com/questions/28247821/openssl-vs-gpg-for-encrypting-off-site-backups\
3. https://security.stackexchange.com/questions/29106/openssl-recover-key-and-iv-by-passphrase/29139#29139
4. https://security.stackexchange.com/questions/31492/file-security-when-encrypting-files-directly-with-the-openssl-command-and-what/31494#31494
Unless things have changed in the past 2 years, Openssl uses custom and insecure constructs and practices to encrypt data. That’s the gist of the posts.
NOTE: I just posted these to give anyone who reads this something to think about. I am *not* saying that openssl is *not* the tool for encrypting files.
I’m saying that it *wasn’t* the tool in the past, how and if that has changed is up to the readers of this post to figure out. I’m no Openssl or Security expert unfortunately.