Tiger is a free, open source collections of shell scripts for security audit and host intrusion detection, for Unix-like systems such as Linux. It’s a security checker written entirely in shell language and employs various POSIX tools in the backend. It’s major purpose is to check the system configuration and status.
It’s very extensible than the other security tools, and has a good configuration file. It scans system configuration files, file systems, and user configuration files for possible security problems and reports them.
In this article, we will show how to install and use Tiger security checker with basic examples in Linux.
How to Install Tiger Security Tool in Linux
On Debian and its derivatives such Ubuntu and Linux Mint, you can easily install Tiger security tool from the default repositories using package manger as shown.
$ sudo apt install tiger
On other Linux distributions, you can download the latest source (the current stable release is 3.2.3, at the time of writing) and run it straight away from the terminal as as root or use the sudo command to gain root privileges.
$ wget -c http://download.savannah.gnu.org/releases/tiger/tiger-3.2rc3.tar.gz $ tar -xzf tiger-3.2rc3.tar.gz $ cd tiger-3.2/ $ sudo ./tiger
By default all checks are enabled, in the tigerrc file and you can edit it using a CLI editor of your liking to enable only the checks you are interested in:
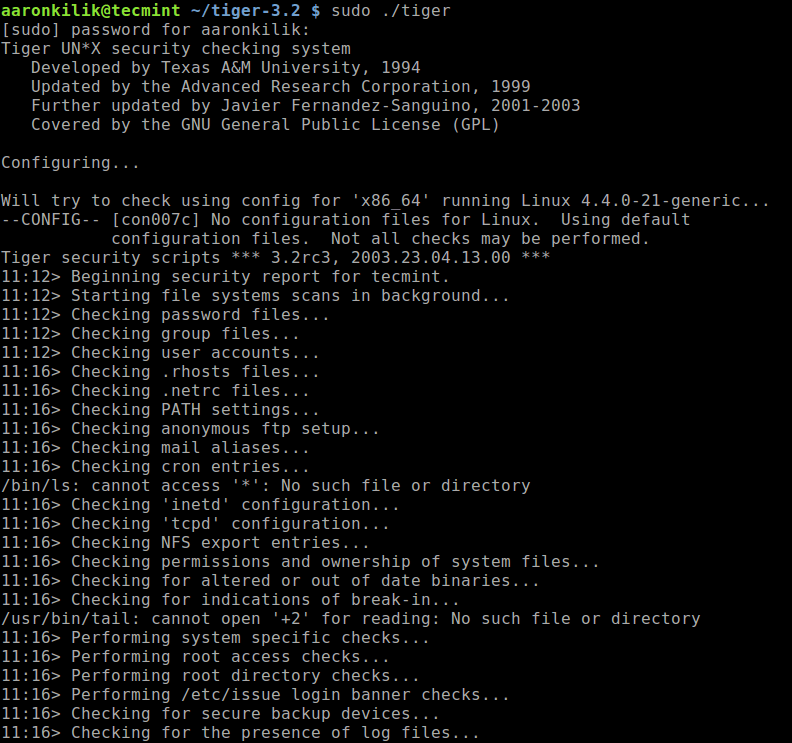
When the security scan is complete, a security report will be generated in the log sub directory, you will see a message similar to this (where tecmint is the hostname):
Security report is in `log//security.report.tecmint.181229-11:12'.
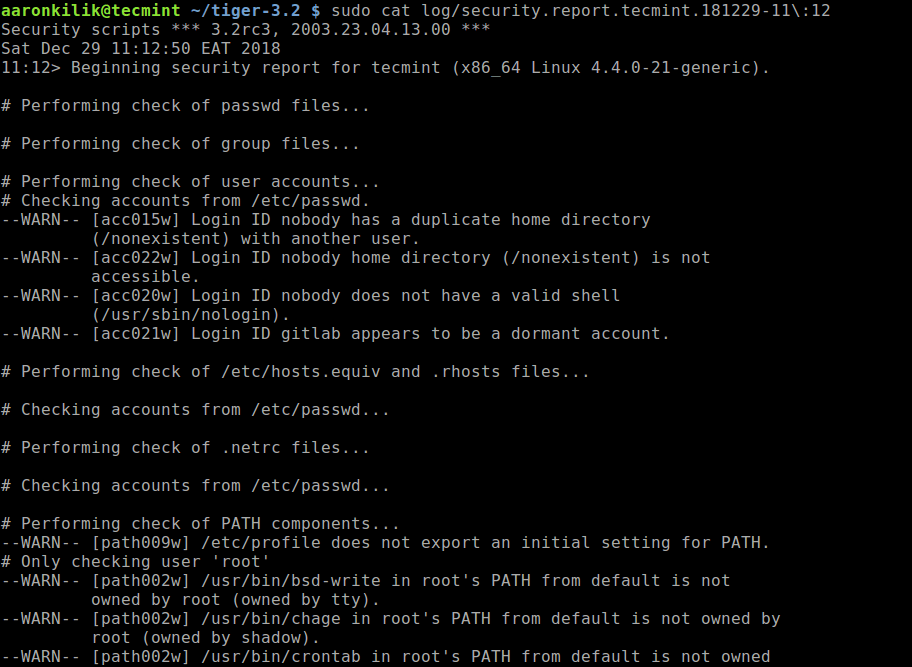
You can view the contents of the security report file using cat command.
$ sudo cat log/security.report.tecmint.181229-11\:12
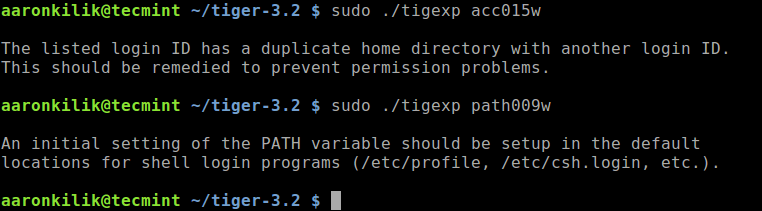
If you just want more information on a specific security message, run the tigexp (TIGer EXPlain) command and provide the msgid as an argument, where “msgid” is the text inside the [] associated with each message.
For example, to get more information about the following messages, where [acc001w] and [path009w] are the msgids:
--WARN-- [acc015w] Login ID nobody has a duplicate home directory (/nonexistent) with another user. --WARN-- [path009w] /etc/profile does not export an initial setting for PATH.
Simply run these commands:
$ sudo ./tigexp acc015w $ sudo ./tigexp path009w
If you want to insert the explanations (more information on a particular message generated by tiger) in the report, you can either run tiger with the -E flag.
$ sudo ./tiger -E
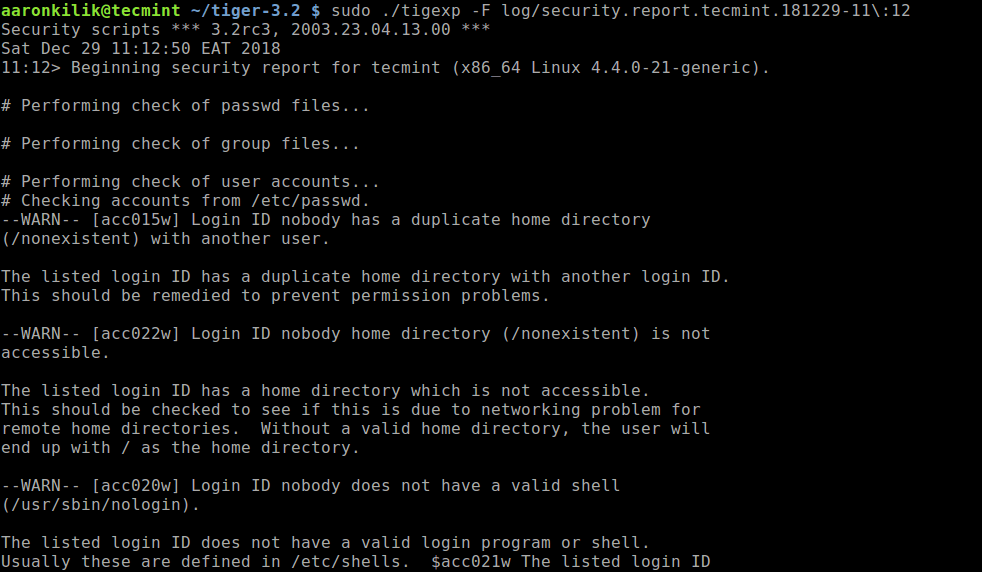
Or if you have already run it, then use tigexp command with the -F flag to specify the report file, for example:
$ sudo ./tigexp -F log/security.report.tecmint.181229-11\:12
To generate a separate explanation file from a report file, run the following command (where -f is used to specify the report file):
$ sudo ./tigexp -f log/security.report.tecmint.181229-11\:12
As you can see, installing tiger is not necessary. However, if you want to install it on your system for purposes of convenience, run the following commands (use ./configure – -help to check configure script options):
$ ./configure $ sudo make install
For more information, see the man pages under the ./man/ sub-directory, and use the cat command to view them. But if you have installed the package, run:
$ man tiger $ man tigerexp
Tiger project homepage: https://www.nongnu.org/tiger/
Tiger is a set of scripts that scan a Unix-like system looking for security problems – it’s a security checker. In this article, we have shown how to install and use Tiger in Linux. Use the feedback form to ask questions or share your thoughts about this tool.





Is the fact that Tiger appears to not have been updated since 2003 not a concern? That would be extremely unusual…
@Unusual
Okay, thanks for sharing this great concern. We will cross-check this.
17586 lines of warnings and failures on a system not tampered with.
How serious should this be taken?
@Gerard
Those are potential security issues with the filesystem, that it has detected. It reports for possible security problems with system configuration files, file systems, and user configuration files that it has scanned. You can read the documentation for more information:https://www.nongnu.org/tiger/index.html#documentation