Reporting Usage and Performance on Your Network
Although there are several available tools to analyze and troubleshoot network performance, two of them are very easy to learn and user friendly.
To install both of them on CentOS, you will need to enable the EPEL repository first.
1. nmon utility
nmon is a system tuner and benchmark tool. As such, it can display the CPU, memory, network, disks, file systems, NFS, top processes, and resources (Linux version & processors). Of course, we’re mainly interested in the network performance feature.
To install nmon, run the following command on your chosen distribution:
# yum update && yum install nmon [On CentOS] # aptitude update && aptitude install nmon [On Ubuntu] # zypper refresh && and zypper install nmon [On openSUSE]
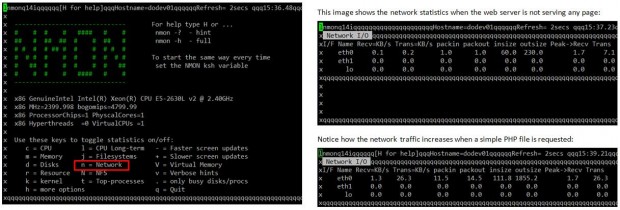
Make it a habit to look at the network traffic in real time to ensure that your system is capable of supporting normal loads and to watch out for unnecessary traffic or suspicious activity.
Vnstat Utility
vnstat is a console-based network traffic monitor that keeps a log of hourly (daily or monthly as well) network traffic for the selected interface(s).
# yum update && yum install vnstat [On CentOS] # aptitude update && aptitude install vnstat [On Ubuntu] # zypper refresh && and zypper install vnstat [On openSUSE]
After installing the package, you need to enable the monitoring daemon as follows:
# service vnstat start [On SysV-based systems (Ubuntu)] # systemctl start vnstat [On systemd-based systems (CentOS / openSUSE)]
Once you have installed and enabled vnstat, you can initialize the database to record traffic for eth0 (or other NIC) as follows:
# vnstat -u -i eth0
As I have just installed vnstat in the machine that I’m using to write this article, I still haven’t gathered enough data to display usage statistics:
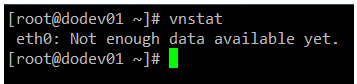
The vnstatd daemon will continue running in the background and collecting traffic data. Until it collects enough data to produce output, you can refer to the project’s web site to see what the traffic analysis looks like.
Transferring Files Securely Over the Network
If you need to ensure security while transferring or receiving files over a network, and specially if you need to perform that operation over the Internet, you will want to resort to 2 secure methods for file transfers (don’t even think about doing it over plain FTP!).
Example 8: Transferring files with scp (secure copy)
Use the -P flag if SSH on the remote hosts is listening on a port other than the default 22. The -p switch will preserve the permissions of local_file after the transfer, which will be made with the credentials of remote_user on remote_hosts. You will need to make sure that /absolute/path/to/remote/directory is writeable by this user.
# scp -P XXXX -p local_file remote_user@remote_host:/absolute/path/to/remote/directory
Example 9: Receiving files with scp (secure copy)
You can also download files with scp from a remote host:
# scp remote_user@remote_host:myFile.txt /absolute/path/to/local/directory
Or even between two remote hosts (in this case, copy the file myFile.txt from remote_host1 to remote_host2):
# scp remote_user1@remote_host1:/absolute/path/to/remote/directory1/myFile.txt remote_user1@remote_host2:/absolute/path/to/remote/directory2/
Don’t forget to use the -P switch if SSH is listening on a port other than the default 22.
You can read more about SCP commands.
Example 10: Sending and receiving files with SFTP
Unlike SCP, SFTP does not require previously knowing the location of the file that we want to download or send.
This is the basic syntax to connect to a remote host using SFTP:
# sftp -oPort=XXXX username@host
Where XXXX represents the port where SSH is listening on host, which can be either a hostname or its corresponding IP address. You can disregard the -oPort flag if SSH is listening on its default port (22).
Once the connection is successful, you can issue the following commands to send or receive files:
get -Pr [remote file or directory] # Receive files put -r [local file or directory] # Send files
In both cases, the -r switch is used to recursively receive or send files, respectively. In the first case, the -P option will also preserve the original file permissions.
To close the connection, simply type “exit” or “bye”. You can read more about sftp command.
Summing Up
You may want to complement what we have covered in this article with what we’ve already learned in other tutorials of this series, for example Part 8: How To Setup an Iptables Firewall.
If you know your systems well, you will be able to easily detect malicious or suspicious activity when the numbers show unusual activity without an apparent reason. You will also be able to plan ahead for network resources if you’re expecting a sudden increase in their use.
As a final note, remember to shut down the ports that are not strictly needed, or change the default to a higher number (~20000) to avoid common port scans to detect them.
As always, don’t hesitate to let us know if you have any questions or concerns about this article.








@Gabriel , You have nicely explained the use of ss & nmap, kudos friend :).
OpenSSH 6.0p1 Debian 4 doesn’t mean that the server is running on Debian 4…
@undert4ker,
Would you be as kind as to point out the exact statement in this article you are referring to?
Passed both LFCS and LFCE exams :)
Thanks
@Artur,
Congratulations…:)
Thanks for this post, do you have the LFCE certification? I will take this exam in July and I need information, is very difficult the test? sorry for my english
Very thank you
@helloworld,
You’re welcome! Please keep coming back to Tecmint.com for more great articles and series. Also, feel free to spread the word!