It wasn’t too long ago that we published a list of the best command line tools for Linux. Today, we turn our focus to encryption methods as we bring you a list of the best file and disk encryption software for your Linux machine.
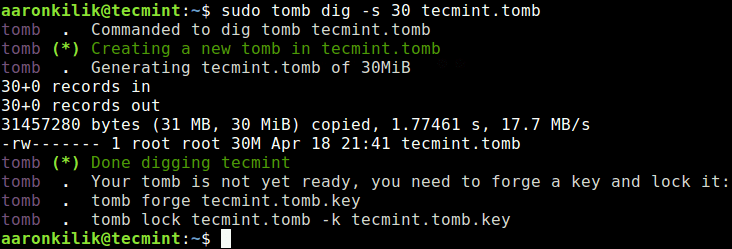
1. Tomb
Tomb is a free and open-source tool for easily encrypting and backing up files on GNU/Linux systems. It consists of a simple shell script that implements standard GNU tools alongside cryptsetup and LUKS (the Linux kernel’s cryptographic API).
Tomb aims to improve safety by adopting a handful of well-tested standards and implementations, applying good practices for key storage, and a minimalist design consisting of concise readable code.
Learn more about Tomb encryption software from our review – Tomb – A File Encryption Tool for Linux.
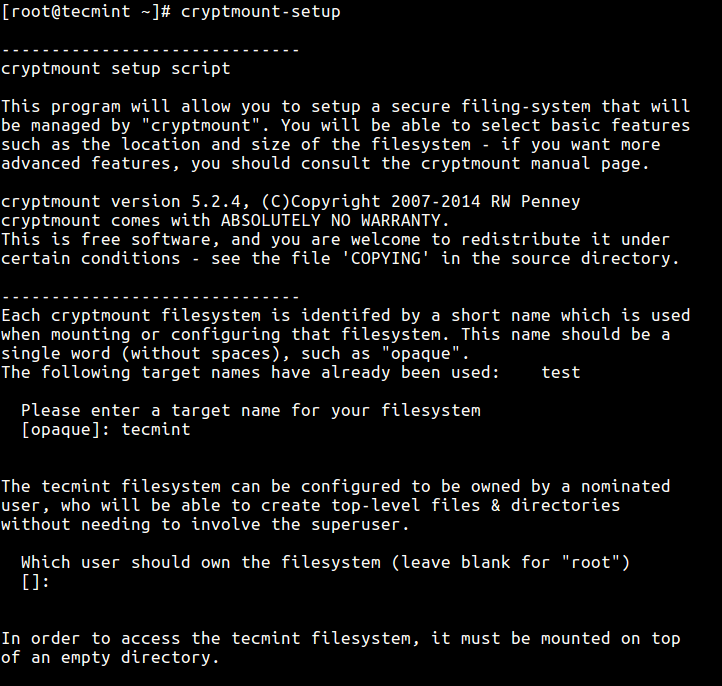
2. Cryptmount
Cryptmount is an open-source utility created for GNU/Linux Operating Systems to enable users to mount encrypted files without root privileges.
It works using the newer devmapper mechanism which offers several advantages including improved functionality in the kernel, support for encrypted swap partitions for superusers, support for crypto-swap at system boot, storing multiple encrypted filesystems in a single disk, etc.
Learn more about Cryptmount from our review – Cryptmount – Create Encrypted Filesystems in Linux.
3. CryFS
CryFS is a free and open-source cloud-based encryption tool for safely storing files anywhere. It is easy to set up, runs in the background, and works nicely with any popular cloud service not excluding Dropbox, OneDrive, and iCloud.
CryFS ensures that no data, including directory structure, metadata, and file content, leaves your computer in an unencrypted format.
4. GnuPG
GnuPG, often referred to as GPG, stands for GNU Privacy Guard and it is a free and open-source collection of cryptographic tools created as a replacement for Symantec’s PGP cryptographic software suite.
It is compliant with the IETF standards-track specification of OpenPGP and RFC 4889. We have covered GnuPG in a little more detail in our best Linux Encrypt/Decrypt tools article.

5. VeraCrypt
VeraCrypt is a multi-platform, freeware open-source tool created to provide users with on-the-fly encryption. You can use it to encrypt entire storage devices or only select partitions using pre-boot authentication.
VeraCrypt’s features include the ability to create virtual encrypted disks and mount them as if they’re real, provision of plausible deniability, pipelining, parallelization, etc.
6. EncFS
EncFS is a free and mostly open-source tool for mounting EncFS folders on Mac and Windows. You can use it to create, edit, change, and export the password of EncFS folders and it is 100% compatible with EncFS 1.7.4 on GNU/Linux platforms.
7. 7-zip
7-zip is a popular, free, and mostly open-source multi-platform file archiving utility for compressing files (or file groups) into containers referred to as archives.
7-zip is among the most popular archiving utilities because of its high compression ratio in 7z format with LZMA and LZMA2 compression, a plugin for FAR manager, integration with Windows Shell, and AES-256 encryption in 7z and ZIP formats, among other features.
8. dm-crypt
dm-crypt is a disk encryption subsystem for encrypting disks, partitions, and portable containers. It was created to address certain reliability problems in cryptoloop and can be used to back up several volume types.
9. ecryptfs
eCryptfs is a free and open-source all-in-one collection of software for disk encryption on Linux. It aims to mirror GnuPG’s functionality by implementing a POSIX-compliant filesystem-level encryption layer and it is been part of the Linux kernel since its 2.6.19 version release.
ecryptfs is cool because you can use it to encrypt directories and partitions irrespective of their underlying file system.
10. cryptsetup
cryptsetup is an open-source utility created to enable users to easily encrypt files based on the DMCrypt kernel module with an emphasis on LUKS design.
LUKS stands for Linux Unified Key Setup and has since become the standard for Linux hard disk encryption thanks to its ability to facilitate distro compatibility, seamless data transport and/or migration, and secure management of multiple user passwords.
How useful are encryption tools to you and which utilities are your favourite to use? Feel free to drop your comments, questions, and suggestions below.


Do you know, what type of encryption if the result extension is .mpro?
Must have VeraCrypt and 7-zip. BUT another one is KeePassXC too.
Thanks a lot man! VeraCrypt is perfectly what I’m looking for.
Check video in link
FinalCrypt: Unbreakable OTP Encryption missing in this list –
http://www.finalcrypt.org/.These are great options for encryption. From this list, I’m familiar only with “Veracrypt” which I used for about three months. However, this was not enough time for me to get used to its design and I decided to try a free version of “Nordlocker” which was released by the VPN provider that I use so I was highly interested.
Now I feel more comfortable since it’s really easy to use and not planning to change it to another software.
Nordlocker is proprietary, so there is no way to know if it’s secure. It may be flawed, intentionally or not. It’s not something that an average user should trust, especially if security is your main priority.
Without ways to verify what it’s doing, that’s something to worry about. Is there a backdoor? Is it sending you information to a remote server? Questions that can’t be answered.
Does Nordlocker work on Linux?
Hi Ravi,
Its really helpful tutorial and thanks for sharing. However I have one question regarding encrypting full disk without formatting the drive. Is there any way to do so?
@Amol,
You can use any of these tools to Encrypt your full disk without formatting..
Hi Ravi,
I looked for the tuts over internet and all those tuts mentioned to format the disk. Not sure how to without formatting. Could you please help me with this? Thanks in advanced.
@Amol,
Check this article – Cryptmount – A Utility to Create Encrypted Filesystems in Linux