Data encryption is a must-have feature in today’s world of cybersecurity. It allows you to encode your data making it unintelligible to someone who doesn’t have authorized access. To be more secure online, it might be a good idea to opt for software that comes with this useful feature by default.
In this article, you will find a list of the best programs with data encryption that run on Linux. Enjoy your reading!
Table of Contents
1. Internxt – Secure Cloud Storage with VPN
Internxt is an open-source cloud storage, file-sharing, and collaboration platform for individuals and businesses. Internxt Drive allows you to upload, sync, and back up your files with advanced encryption and security controls.
Unlike other solutions, such as Google Drive, Internxt encrypts data on your device before it is transmitted to the Internet. This end-to-end encryption protects your files from hackers and unauthorized access and ensures that all your confidential files are 100% private.
In addition to this security, Internxt offers secure file sharing to share files securely with friends or family or within teams and different departments with business plans.
Security features of Internxt include password protection for files, automatic backups, Two-Factor Authentication, and expiration dates for shared folders, giving administrators, teams, and customers the best privacy and security to protect files from data loss.
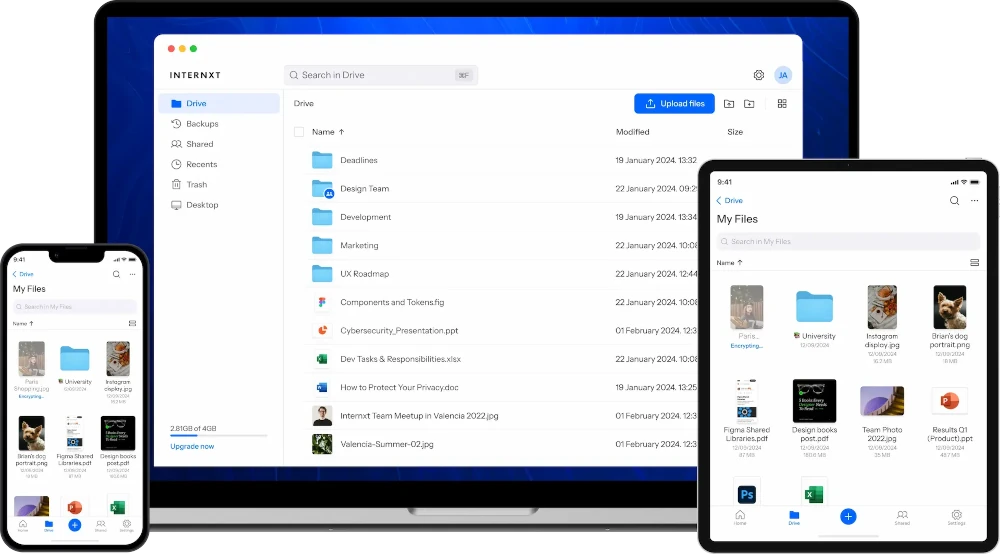
The Internxt app is easy to use and is available on Windows, Mac, Linux, and mobile apps for the App and Play Store.
All tecmint readers can get 70% off on all Internxt lifetime plans. However, the company often has higher sales onsite that you can keep an eye on.
2. Signal – Secure Text Messaging and Video Conferencing
Signal is an open-source instant messaging app that allows you to send text and voice messages, share photos, videos, GIFs, and even files for free. The application is not as popular as Telegram or WhatsApp, but most advanced users find it useful because it is focused on offering maximum data privacy.
The built-in security features make it almost impossible for others to intercept your communications, which can happen while using other messaging apps.
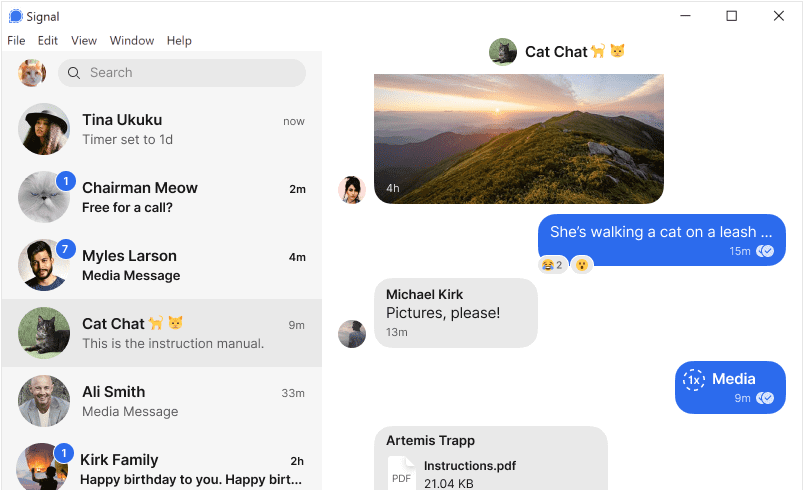
For all communications, the application uses an end-to-end encryption protocol called Signal Protocol and was developed by Open Whispers Systems, a non-profit organization of open-source software developers. All your messages leave your mobile phone already encrypted and are only decrypted when they reach the recipient’s device.
This way, if someone intercepts them along the way, they won’t be able to read them. Unlike other apps such as Telegram, which only apply end-to-end encryption when you open a private conversation, Signal applies encryption by default to all messages and calls.
One of Signal’s most outstanding options is that it allows you to configure the self-destruction of the messages you send. Using this feature, you can set a period of time that can be from 5 seconds to a week so that the sent messages are automatically deleted after that time, which maximizes the security of your online conversations.
Another advantage is that Signal is open source, and the source code of the Signal mobile apps for Android and iOS as well as the desktop clients for Linux, Windows, and macOS can be found on Github. This means that Signal is an app that works transparently and that any developer or user can look at its code for vulnerabilities or bugs.
Install Signal in Linux
The following instructions only work for 64-bit Debian-based Linux distributions such as Ubuntu, Linux Mint, etc.
$ wget -O- https://updates.signal.org/desktop/apt/keys.asc | gpg --dearmor > signal-desktop-keyring.gpg $ cat signal-desktop-keyring.gpg | sudo tee -a /usr/share/keyrings/signal-desktop-keyring.gpg > /dev/null $ echo 'deb [arch=amd64 signed-by=/usr/share/keyrings/signal-desktop-keyring.gpg] https://updates.signal.org/desktop/apt xenial main' |\ sudo tee -a /etc/apt/sources.list.d/signal-xenial.list $ sudo apt update && sudo apt install signal-desktop
3. Nextcloud – Secure File Sharing
Nextcloud is an open-source content collaboration platform that allows you to set up your own personal environment on a server for file sharing and synchronization.
Once installed and configured, it makes it possible to host data and files between different devices (including mobile) and users.
Compared with the proprietary software, the functionality of Nextcloud is not only equivalent to the well-known Google Drive. The platform also offers some features that are very similar to Google Calendar and Google Photos.
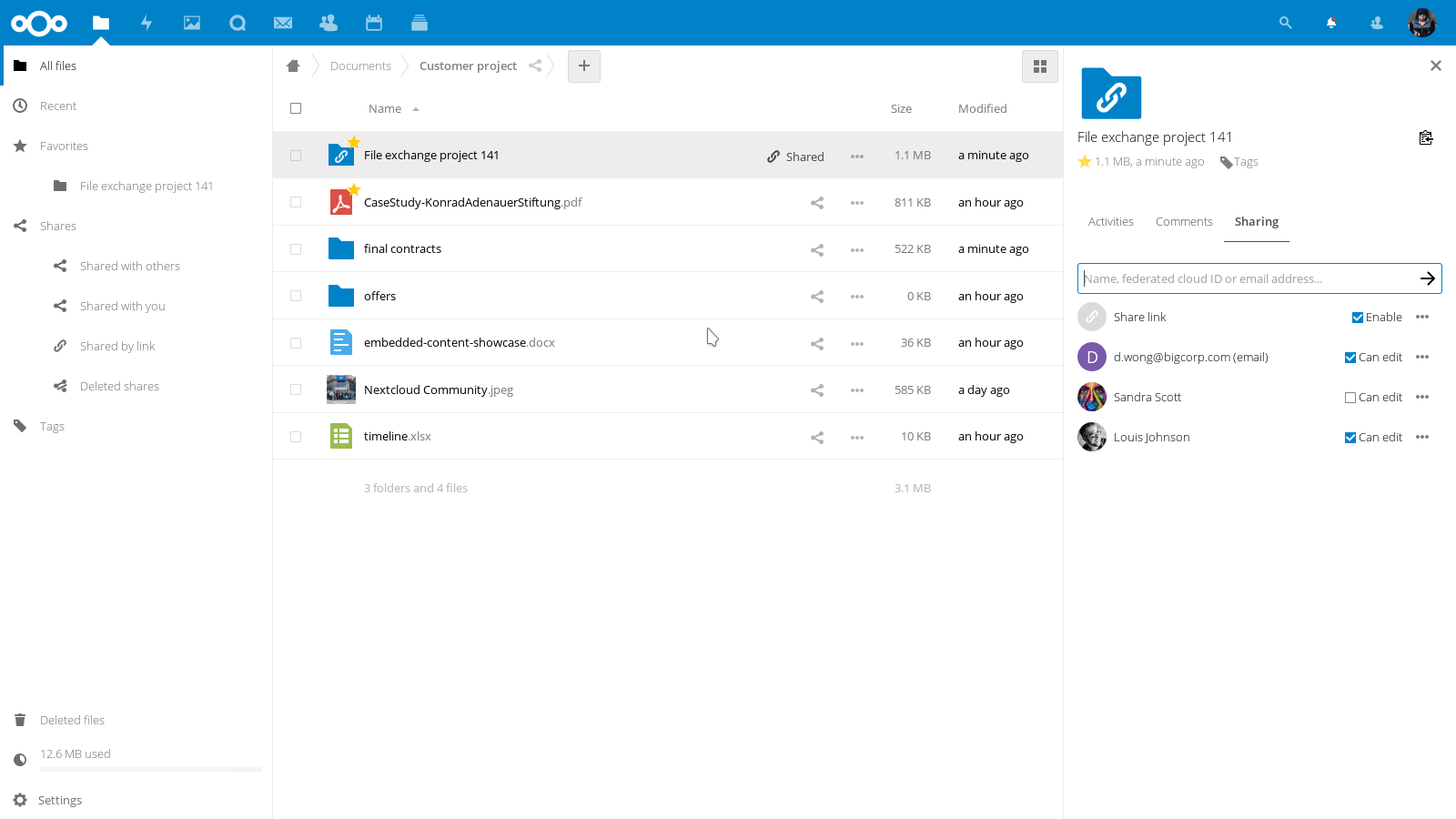
On the official Nextcloud App Store, there are plenty of additional applications that let you bring different kinds of extra features to your Nextcloud platform making it a powerful collaborative environment.
For example, you can add blogs, maps, multimedia players, SMS synchronizers, office suites, Markdown text editors, video conferencing tools, task managers, notes or passwords managers, RSS readers, and more.
Nextcloud provides universal access, both through a web browser and mobile or desktop applications for Linux, Windows, and macOS. You can share the platform with other people by creating multiple accounts, which makes Nextcloud a good option for collaborative work.
Nextcloud not only allows you to encrypt your files in transit when sharing them with other users, for example, via password-protected public links but also makes it possible to encrypt your local storage. Thus, all the data is stored in secure mode and even the administrators cannot read the user’s files.
4. Tor Browser – Secure Internet Surfing
If you are interested in safe and anonymous Internet surfing, you might have heard about the Tor Project. Tor stands for The Onion Router, a global network of servers for anonymous Internet surfing.
Generally speaking, it’s a system based on a layered structure (that’s why it is called “onion“) that allows you to jump from one layer to another, being protected by them and thus improving anonymity or privacy.
Tor creates a decentralized network across multiple nodes so that traffic can’t be traced back to you. The more users connect to the network, the more protected the information is.
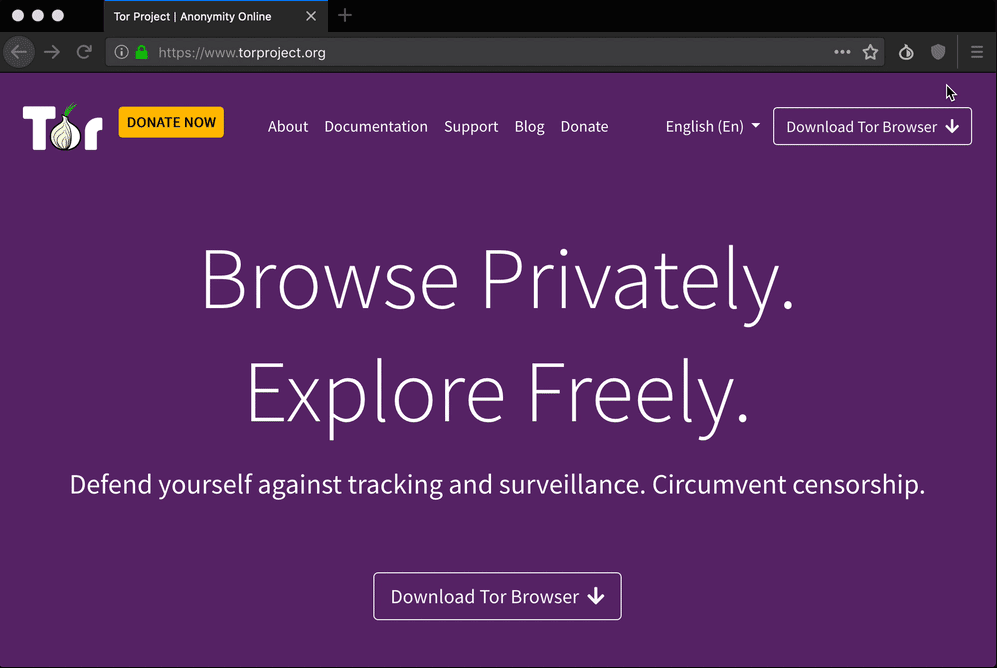
The Tor project offers a special web browser that allows you to connect to the Tor network without the need to install proxy applications or perform any complex configuration. It’s available for Linux, Windows, and macOS and has an Android version for mobile devices.
Tor Browser is very similar to any other web browser and doesn’t require a lot of knowledge to get started. It isolates each web page you visit to make it impossible for third-party trackers and ads to follow your activity. The browser automatically clears all cookies and browsing history when you log out.
When you surf the Internet through Tor Browser, all your traffic is encrypted three times passing over the Tor network. Thus, your online activity always remains private.
5. Tutanota – Secure Email Messaging
Tutanota is a web-based email service from Germany. Under the motto “Secure email for everyone!”, the software puts a strong emphasis on security and privacy above all else.
This includes supporting end-to-end encryption to make interception nearly impossible, protecting your identity by not keeping records or requiring tons of personal information when registering, and providing secure methods for communicating with people who use traditional email providers like Gmail or Outlook.
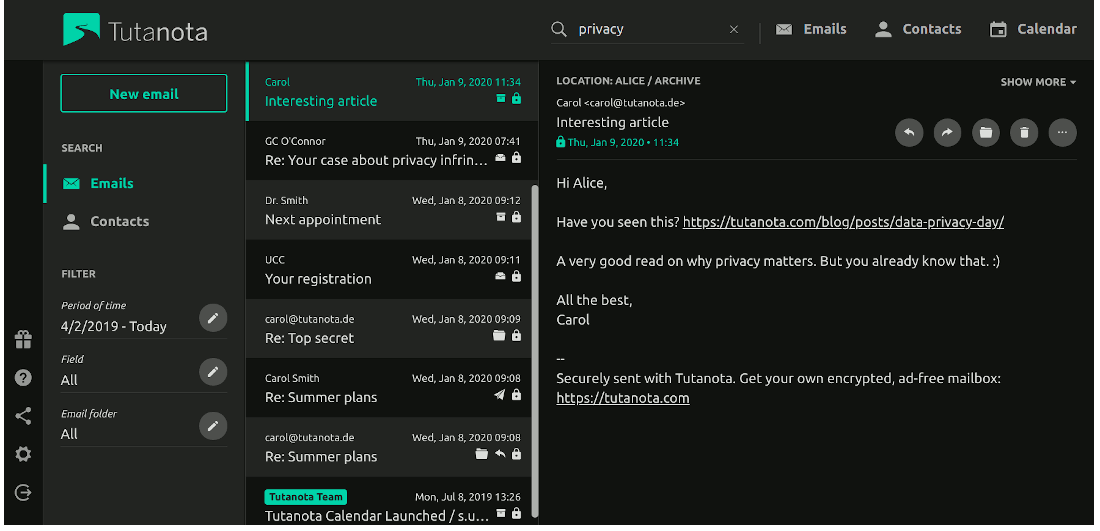
Using Tutanota, you get a custom email address when you register a free account. Tutanota offers a couple of pricing tariff plans for users, starting at $0 per month and working up from there.
The main difference between the free account and the paid offerings is that the free account has limited users, limited storage, and comes with fewer personalization options.
When it comes to security, Tutanota has multiple ways to implement encryption. It has end-to-end encryption between Tutanota clients, as well as optional password-protected encryption when a Tutanota user sends an email to someone using another email provider.
Although Tutanota is usually accessed through the web app, there are open-source apps for Android and iOS and a desktop client for Linux, Windows, and macOS.
6. ONLYOFFICE Workspace – Secure Document Collaboration
ONLYOFFICE Workspace is an open-source online office suite that comes with collaborative editors for text documents, spreadsheets, and presentations as well as with a set of web apps for document and file management, projects, CRM, email messaging, calendaring, real-time communication, and social networking (forums, blogs, news broads, wiki databases, polls, etc.).
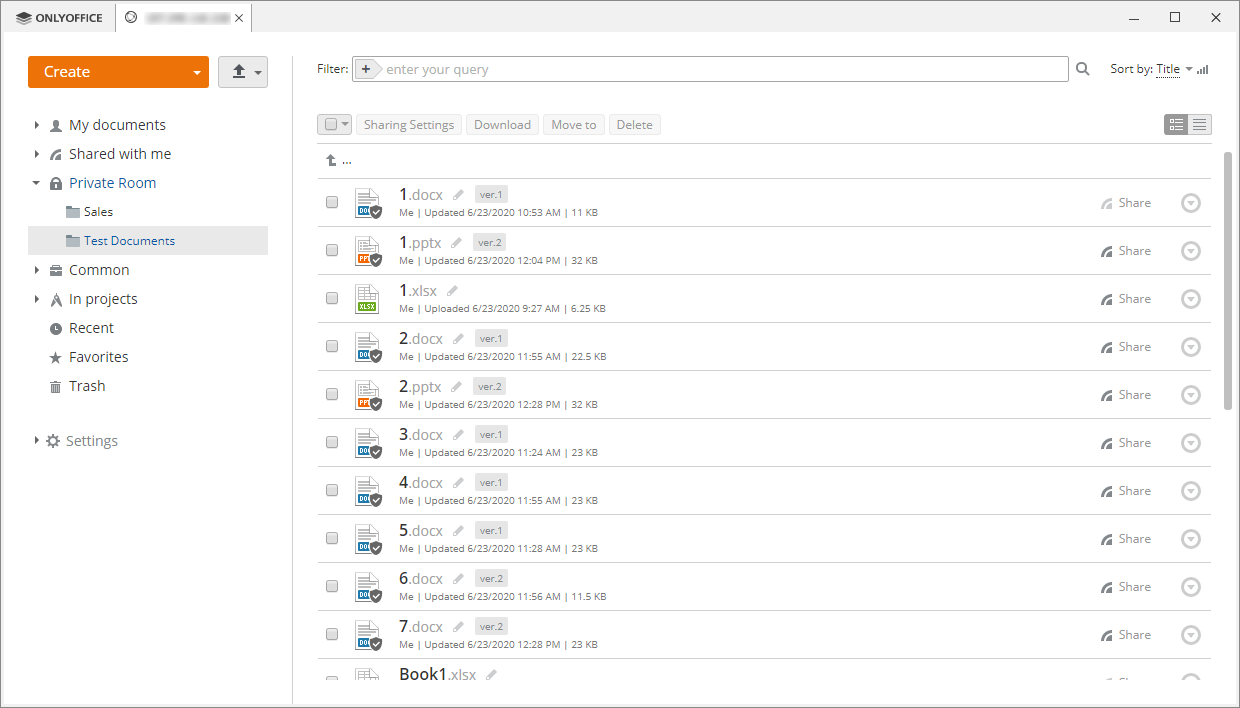
ONLYOFFICE Workspace uses the HTTPS protocol and JSON Web Token for data protection. It also provides such security features as two-factor authentication, SSO, and automatic and manual data backups.
End-to-end encryption in ONLYOFFICE Workspace is implemented through the Private Rooms feature. It’s a special section in the Documents module where you can create and co-edit documents in real time with safety.
All the documents you keep in a Private Room are encrypted using the AES-256 algorithm. When collaborating online on a document from the Private Room, all the changes are encrypted locally on one end, transferred to the ONLYOFFICE server in an encrypted form, and then decrypted on the other end.
Private Rooms work through ONLYOFFICE Desktop Editors and are easy to use. All you need to do is to connect the desktop application to your ONLYOFFICE Workspace instance and start editing your documents as you usually do. There is no need to invent or enter any passwords as the encryption process is automatic.
Conclusion
Please remember that data encryption is just a tool that can help you stay safe online. It doesn’t guarantee the complete privacy of your data if you don’t follow the basic security tips like preventing authorized access to your devices and networks and don’t use special software like password managers and backup applications.
However, if applied correctly in combination with other tools, data encryption makes things much easier and more secure.



The only way two people can keep a secret is if one of them is dead.
As soon as you start sharing data with others, your security goes out the window. The loss of security is in a geometric proportion to the number of people sharing the data.