There are plenty of network monitoring tools you can find in the Linux ecosystem, that can generate for you a summary of the total number of devices on a network including all their IP addresses and more.
However, sometimes what you actually need may be a simple command line tool that can provide you the same information by running a single command.
This tutorial will explain you how to find out all live hosts IP addresses connected to a given network. Here, we will use Nmap tool to find out all IP addresses of devices connected on a same network.
Suggested Read: 29 Examples of ‘Nmap’ Commands for System/Network Administration
The Nmap (short form for Network Mapper) is an open source, powerful and a very versatile command line tool for exploring networks, perform security scans, network audit and finding open ports on remote machine and so much more.
In case you do not have Nmap installed on your system, run the appropriate command below for your distribution to install it:
$ sudo yum install nmap [On RedHat based systems] $ sudo dnf install nmap [On Fedora 22+ versions] $ sudo apt-get install nmap [On Debian/Ubuntu based systems]
Once you have Nmap installed, the syntax for using it is:
$ nmap [scan type...] options {target specification}
Where the argument {target specification}, can be replaced by hostnames, IP addresses, networks and so on.
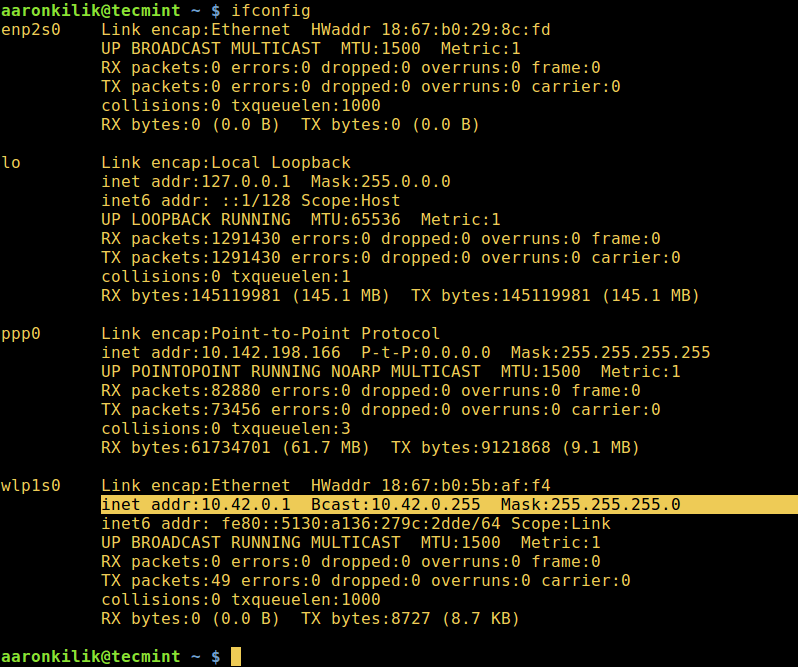
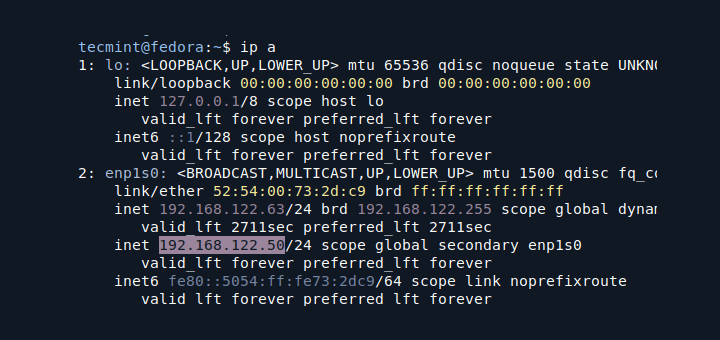
Therefore to list the IP addresses of all hosts connected to a given network, first of all identify the network and its subnet mask using the ifconfig command or ip command like so:
$ ifconfig OR $ ip addr show
Next, run the Nmap command below:
$ nmap -sn 10.42.0.0/24
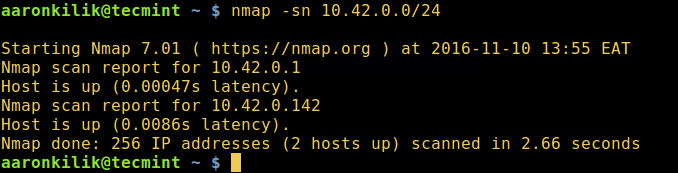
In the command above:
-sn– is the type of scan, which means a ping scan. By default, Nmap performs port scanning, but this scan will disable port scanning.10.42.0.0/24– is the target network, replace it with your actual network.
For a comprehensive usage information, make an effort to look into Nmap man page:
$ man nmap
Else, run Nmap without any options and arguments to view a summarized usage information:
$ nmap
In addition, for those interested in learning security scanning techniques in Linux, you can read through this practical guide to Nmap in Kali Linux.
Well, that’s it for now, remember to send us your questions or comments through the response form below. You can as well share with us other methods for listing the IP addresses of all devices connected to a given network.




This will work on IPv4 but not on an IPv6 network. a sub-net on IPv6 has 64 bits of address space in each sub-net. It would take a 1000 years for a fast computer to scan that IP range. I was hoping that there might be a reference to some Neighbor discovery tool to achieve this on an IPv6 network
@Rms-Mit
That is correct, and because the we have been using IPv4 on our LANs, we did not mention any point concerning IPv6 support here. However, recent versions of Nmap offer support for IPv6 and you can read more from here: https://nmap.org/ and here is an additional resource providing more insights on scanning IPv6 addresses using Nmap: http://security.stackexchange.com/questions/51523/how-do-i-use-nmap-to-scan-a-range-of-ipv6-addresses.
Using nmap is an active scan, but that’s not necessary for this purpose. All hosts arp to identify themselves to other hosts on the network, so simply displaying the arp table will show you what you want, instantly.
arp -n | grep -v “incomplete\|Flags” | sort -V
@Mace
This is an effective and reliable option as well, thanks for sharing this tip with us.
This is nice. Is there a command that will display (all live non assigned) available IP addresses in a network?
@Mighty,
I suggest you to read our complete Nmap guide for finding out all live non assigned IP address at https://www.tecmint.com/nmap-network-security-scanner-in-kali-linux/