Are you a Linux system administrator and want to monitor interactive activity of all system users (Linux commands they executes) in real-time. In this brief Linux system security guide, we will explain how to view all Linux shell commands executed by system users in real-time.
Read Also: How to Monitor User Activity with psacct or acct Tools
If your system has bash, the most commonly used shell out there then all commands executed by normal system users will be stored in the .bash_history hidden file which is kept in each user’s home directory. The content of this file can be viewed by users, using the history command.
To view a user aaronkilik’s .bash_history file, type:
# cat /home/aaronkilik/.bash_history
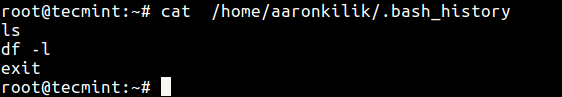
From the screen shot above, the date and time when a command was executed is not shown. This is the default setting on most if not all Linux distributions.
You can follow this guide to set date and time for each command in bash_history file.
Monitor User Activity in Real-time Using Sysdig in Linux
To get a glimpse of what users are doing on the system, you can use the w command as follows.
# w
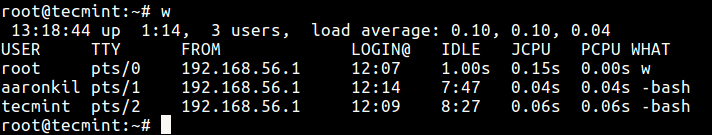
But to have a real-time view of the shell commands being run by another user logged in via a terminal or SSH, you can use the Sysdig tool in Linux.
Sydig is an open-source, cross-platform, powerful and flexible system monitoring, analysis and troubleshooting tool for Linux. It can be used for system exploration and debugging.
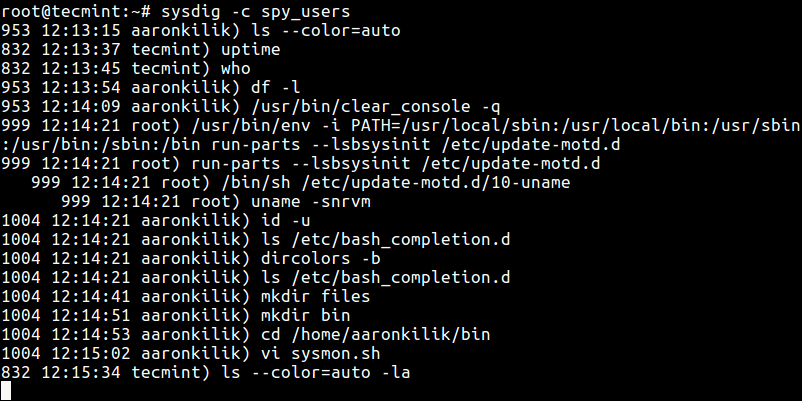
Once you have installed sysdig, use the spy_users chisel to spy on users by running the command below.
# sysdig -c spy_users
The above command displays every command that users launch interactively as well as every directory users visit.
That’s all, you can also check out these following related articles:
- 25 Hardening Security Tips for Linux Servers
- Lynis – Security Auditing and Scanning Tool for Linux Systems
- 10 Useful Open Source Security Firewalls for Linux Systems
- A Practical Guide to Nmap (Network Security Scanner) in Linux
In this system security guide, we described how to view users bash history file, show logged on users and what they are doing, and we also explained how to view or monitor all commands executed by system users in real-time.
If you want to share any other methods or ask questions, please do so via the comment section below.





What happens if the user that has sudo privileges suddenly changes profile and elevates to root profile? ie… ‘sudo su – ‘ at this point the user is in root profile /root . can this sysdig utility still monitor in this case?
@Jor
This is a good question, yes sysdig will still monitor the users activity. But it will show the user as root, this means as a system admin, you need to review logfiles(to be specific files in /var/log/audit/ or /var/log/auth.log) to see users who switched to root the account.
By default settings the bash_history is only written to when the shell is closed. Moreover starting your command line with a space doesn’t append it to the history. So using the bash history to monitor user activity looks like complete nonsense to me.
@K0n24d
~/.bash_history is only used to view previous commands as clearly stated in the article.
watch -n 1 tail ~/.bash_history
@TheOuterLinux
This will only help a user watch their own command history, as a sys admin, you would use something like:
#watch -n 1 tail /home/username/.bash_history
But this only allows you to watch one users commands history. Therefore, sysdig as shwon above is still more appropriate for keeping an eye on all users’ command line.