SSH stands for Secure Shell is a network protocol, used to access remote machine in order to execute command-line network services and other commands over a Network. SSH is Known for its high security, cryptographic behavior and it is most widely used by Network Admins to control remote web servers primarily.

Here in this Interview Questions series article, we are presenting some useful 10 SSH (Secure Shell) Questions and their Answers.
1. SSH is configured on what Port Number, by default? How to change the port of SSH?
We can check port number of SSH by running the below one liner script, directly on terminal.
# grep Port /etc/ssh/sshd_config [On Red Hat based systems] # grep Port /etc/ssh/ssh_config [On Debian based systems]
To change the port of SSH, we need to modify the configuration file of SSH which is located at ‘/etc/ssh/sshd_config‘ or ‘/etc/ssh/ssh_config‘.
# nano /etc/ssh/sshd_config [On Red Hat based systems] # nano /etc/ssh/ssh_config [On Debian based systems]
Searh for the Line.
Port 22
And replace ‘22‘ with any UN-engaged port Number say ‘1080‘. Save the file and restart the SSH service to take the changes into effect.
# service sshd restart [On Red Hat based systems] # service ssh restart [On Debian based systems]
2. As a security implementation, you need to disable root Login on SSH Server, in Linux. What would you suggest?
To disable SSH root login, open the configuration file located at ‘/etc/ssh/sshd_config‘ or ‘/etc/ssh/ssh_config‘.
# nano /etc/ssh/sshd_config [On Red Hat based systems] # nano Port /etc/ssh/ssh_config [On Debian based systems]
Change the parameter ‘PermitRootLogin‘ to ‘no‘ and restart the SSH service as show above.
3. SSH or Telnet? Why?
4. Is it possible to login to SSH server without password? How
Create ssh-keygen using the command below.
$ ssh-keygen
Copy public keys to remote host using the command below.
$ ssh-copy-id -i /home/USER/.ssh/id_rsa.pub REMOTE-SERVER
Note: Replace USER with user name and REMOTE-SERVER by remote server address.
The next time we try to login to SSH server, it will allow login without asking password, using the keygen. For more detailed instructions, read how to login remote SSH server without password.
5. How will you allows users and groups to have access to SSH Sever?
Here again we need to edit the configuration file of SSH service. Open the configuration file and add users and groups at the bottom as show below and then, restart the service.
AllowUsers Tecmint Tecmint1 Tecmint2 AllowGroups group_1 group_2 group_3
6. How to add welcome/warning message as soon as a user login to SSH Server?
# nano /etc/issue
And add your custom message in this file. See, below a screen grab that shows a custom message as soon as user logged into server.
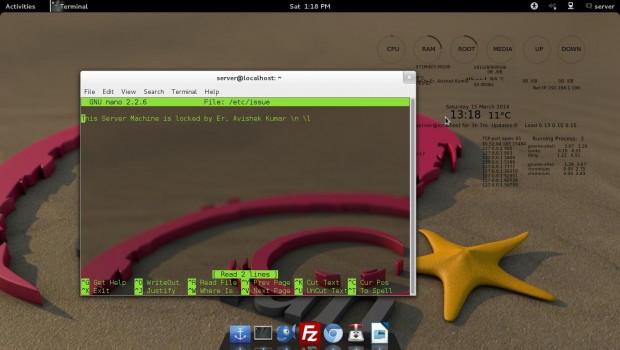
7. SSH has two protocols? Justify this statement.
Again, we need to open the SSH configuration file and add/edit the lines as shown below.
# protocol 2,1 to Protocol 2
Save the configuration file and restart the service.
8. Is it possible to trace unauthorized login attempts to SSH Server with date of Intrusion along with their corresponding IP.
# cat /var/log/secure | grep “Failed password for”
Note: The grep command can be tweaked in any other way to produce the same result.
9. Is it possible to copy files over SSH? How?
A dummy SCP command in action is depicted below:
$ scp text_file_to_be_copied Your_username@Remote_Host_server:/Path/To/Remote/Directory
For more practical examples on how to copy files/folders using scp command, read the 10 SCP Commands to Copy Files/Folders in Linux.
10. Is it possible to pass input to SSH from a local file? If Yes! How?
# ssh username@servername < local_file.txt
SSH is a very hot topic from interview point, of all times. The above questions would have surely added to your knowledge.
That’s all for now. I’ll soon be here with another interesting article. Till then Stay Tuned and connected to Tecmint. Don’t forget to provide us with your valuable feedback in our comment section.






In Redhat OS, there are 2 files under /etc/ssh i.e sshd_config and ssh_config? What is the difference and what is the use of both files and for what purpose??
sshd_config is for daemon – ssh _server_ process working on host you connect to.
ssh_config is used to set up system-wide default settings for ssh command (ssh-client)
when given three departments how can write policy document for the security system for the bank that ensures integrity authentication in the bank.
Oh-oh-oh. There is no difference in config file names between RH, Debian, Gentoo and so on. I.e.
==================================================================
root@seafile:~# lsb_release -d
Description: Debian GNU/Linux 8.6 (jessie)
root@seafile:~# ls /etc/ssh/*_config
/etc/ssh/ssh_config /etc/ssh/sshd_config
root@seafile:~# head -n 3 /etc/ssh/ssh_config
# This is the ssh client system-wide configuration file. See
# ssh_config(5) for more information. This file provides defaults for
root@seafile:~# head -n 5 /etc/ssh/sshd_config
# Package generated configuration file
# See the sshd_config(5) manpage for details
# What ports, IPs and protocols we listen for
Port 22
==================================================================
[root@aloe ~]# cat /etc/redhat-release
CentOS release 4.9 (Final)
[root@aloe ~]# ls /etc/ssh/*_config
/etc/ssh/ssh_config /etc/ssh/sshd_config
[root@aloe ~]# head -n 3 /etc/ssh/ssh_config
# $OpenBSD: ssh_config,v 1.19 2003/08/13 08:46:31 markus Exp $
# This is the ssh client system-wide configuration file. See
[root@aloe ~]# head -n 5 /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.69 2004/05/23 23:59:53 dtucker Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
==================================================================
isa ~ # cat /etc/gentoo-release
Gentoo Base System release 2.3
isa ~ # ls /etc/ssh/*_config
/etc/ssh/ssh_config /etc/ssh/sshd_config
isa ~ # head -n 3 /etc/ssh/ssh_config
# $OpenBSD: ssh_config,v 1.30 2016/02/20 23:06:23 sobrado Exp $
# This is the ssh client system-wide configuration file. See
isa ~ # head -n 5 /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.99 2016/07/11 03:19:44 tedu Exp $
# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.
==================================================================
Ubuntu, Mint, Calculate all of them have two config files ssh_config for ssh client and sshd_config for daemon.
So seriously mistakes… :( Very bad!
Hi Ravi,
How does ssh work, mean to say what is the functionality of public and private key ,how the communication takes place b/w client and server.
It was asked to me in vmware interview.
Can you please help
Can SSH is used for making http requests to a web server, checking network path to a remote, and writing a web server, accessing a remote computer. please tell me the answer
@Deepa,
SSH is used to only connect remote Linux servers, and on the remote client SSH client must be installed to make a SSH connection…not for HTTP requests..
ok. thank u sir
which you provide information regarding ssh is nice, it ‘s very useful to sysadmins in linux.
Hello.
I hope you can help me.
What is the -f flag in scp?
Thank you
@Alan,
There isn’t any -f switch in scp man pages, yes there is capital -F option, which is used to specify per-user configuration file for ssh.
I found that is a undocumented option to, specified “from” (-f) and “to” (-t)
“In all cases aside from remote-to-remote scenario the scp command processes command line options and then starts an SSH connection to the remote host. Another scp command is run on the remote side through that connection in either source or sink mode. Source mode reads files and sends them over to the other side, sink mode accepts them. Source and sink modes are triggered using -f (from) and -t (to) options, respectively. These options are for internal usage only and aren’t documented. There is also the 3rd hidden option, -d, when the target is expected to be a directory.”
http://docstore.mik.ua/orelly/networking_2ndEd/ssh/ch03_08.htm
And this:
“So, how does the transfer protocol actually works? If you forget about ssh, sshd and the connection between them and concentrate only on interaction between scp in “normal” mode and scp in the sink mode, you can see the scenario like this (if you copied from remote to local the remote scp command would have been run with -f option instead of -t, denoting the source mode):”
https://blogs.oracle.com/janp/entry/how_the_scp_protocol_works
@Alan,
Thanks for the detailed information about background process of ssh and scp, very helpful, let me go through it and come back to you..
I face most of the problems in Linux Network commands. What are the main questions related to Networking in ssh ?
in #6. How to add welcome/warning message as soon as a user login to SSH Server?
the command nano/etc/issue is not working, any other solution for this…
but i am using /etc/motd for welcome/warning message
Seems you have not installed nano editor.
try
# vi /etc/issue
[Note there is gap between vi and /etc]
At Debian systems the SSH config could be found at “/etc/ssh/sshd_config” not “/etc/ssh/ssh_config” this is the SSH-Client config!
good one!
Thanks for the recognition.
keep Connected for more such posts.
On Debian and most Debian-based systems like, Ubuntu the ssh server configuration is in /etc/ssh/sshd_config
There are a lot of differences between Debian and Red Hat, but this is identical!
They always say something like “love to research nix” but they seem to never do that before posting articles.
Ref #6
I would also like a message when i login, but I only get a message, maybe my configuration is wrong ;-)
Ref #8
A better way is
grep “Failed password for” /var/log/secure
because pipe will fork another process.
On #1 and #2, as has been said by others, the /etc/ssh/ssh_config file is the client configuration while /etc/ssh/sshd_config is the server configuration file. All distributions should have both. Debian is not special here.
On #2 I prefer the without-password setting for PermitRootLogin. This disables password authentication for the root account but still allows root access via more secure authentication methods. Normally that means key authentication but it can also mean any other non-password authentication you have configured (such as the also previously mentioned Kerberos).
On #4 you would only need to specify a key file to ssh-copy-id if the file is not one of the standard file names and is not loaded into an agent. Otherwise ssh-copy-id will authorize every key it can find. You should also mention how to manually authorize a key since servers often have password authentication disabled (something that should be an additional question) and therefore ssh-copy-id can’t get in to authorize your key(s).
On #9 both sftp and rsync should also be mentioned. Both are actually superior to scp unless you need the rarely used scp -3 functionality.
Thank you Kumar, excellent article. One quick question, I was checking for the “/var/log/secure” file on my linux mint 17 Qiana and was not there. Is there a command or comment change I need to do to get SSH to start keeping logs about fail log in attempts.? Thank you in advance!
Actually, I found out that in Debian based systems the “/var/log/secure” file is in “/var/log/auth.log” ^.^ Thank you!
hye! I’m trying to change port number for ssh , but it refuse to work…
@halcyon,
How you changing? are you changing in sshd_config file? or any other way.. The proper way is to edit the sshd_config file and replace the port 22 with your choice of port…and restart ssh to work on new port..
/etc/ssh/ssh_config is on client side
Thanks good article regarding SSH questions.
Welcome @ raman
Thank you !!!!!!!!!!!!!!!!!!Nice topics and also comment of Roberto C. Sanchez is also very good .
thanks for sharing info.
Welcome @ venky
Nice article thanks for sharing :)
Welcome @ kiran
Nice and very valuable information
Thanks for the feedback @ Ravindra Reddy.
“ssd_config” to alter SSH SERVER configuration on Debian? Really? ?? I stopped reading here.
Thanks for Pointing the TYPO!
Requesting Admin to correct it.
Great Info…!
Thanks a lot Roberto for alternative methods and other useful features of SSH..!
Cheers..!
Welcome @ abilash.
Somebody forgot to proof read this article to the point that it’s factually incorrect.
Example:
“Protocol 1 is less secure than protocol 1 and should be disabled in the config file.”
Several notes about your article (I numbered them to correspond to your questions):
1. The /etc/ssh/ssh_config file is NOT the correct file. That file is for the system-wide ssh client configuration. The daemon is configured by /etc/ssh/sshd_config (as in other distros). Also, it is valid to specify the port directive with any sort of capitalization (e.g., “port” or “PORT” or even “pOrT”), so the grep command should be ‘grep -i port /etc/ssh/sshd_config’. Additionally, that command will only tell you what port has been configured, not what port the running daemon is actually listening on. That is, if the port specification in the configuration is changed but the daemon is not restarted, you will be misled. To see what port the daemon is currently listening on, you can run ‘netstat -nplt |grep sshd’. There is no ‘service’ command on Debian. You can restart ssh by running ‘/etc/init.d/ssh restart’.
2. Same as with #1, the file in Debian is /etc/ssh/sshd_config. Also, the command ‘nano Port /etc/ssh/ssh_config’ does not make sense.
3. In a Kerberos environment with a Kerberos-enabled telnet, it can use encryption. Of course, SSH can also take advantage of Kerberos authentication, so it is still likely a better choice these days than even encrypted telnet.
4. It is also possible to login via SSH without a password when using Kerberos for authentication.
6. /etc/issue is just the default, you can use any file with the directive ‘Banner /path/to/message’ in sshd_config. This can be used if you need to display different welcome messages to remote users than to local users.
8. First, it is pointless and unnecessary to ‘cat’ a file only to pipe it into ‘grep’. If the file is very large, it can be unnecessarily slow. You can achieve exactly the same by running ‘grep “Failed password for” /var/log/secure’. Also, there is no /var/log/secure on Debian systems. On a Debian system you would look in /var/log/auth.log. Also, the string “Failed password for” will only show you when someone tries to log in as an authorized user. If the user is not authorized (because you have used the AllowedUsers and/or AllowedGroups), then you should also look for “Invalid user”.
9. You make no mention of the sftp command.
10. You left out mention of some very useful features of ssh, including using the -f option to background ssh before executing a command on the remote host, as well as setting up secure tunnels with ssh.
You are doing the lord’s work, Roberto Sanchez. You covered everything I was going to gripe about and added in some nuggets I was unaware of. Bravo.