In this guide, we will show how to switch to another or a specific user account without requiring a password. For example, we have a user account called postgres (the default PostgreSQL superuser system account), we want every user (typically our PostgreSQL database and system administrators) in the group called postgres to switch to the postgres account using the su command without entering a password.
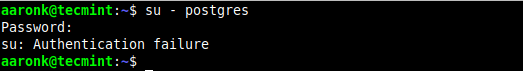
By default, only the root user can switch to another user account without entering a password. Any other user will be prompted to enter the password of the user account they are switching to (or if they are using the sudo command, they will be prompted to enter their password), if they don’t provide the correct password, they get an “authentication failed” error as shown in the following screenshot.
You can use any of the two solutions provided below to solve the above issue.
1. Using PAM Authentication Module
PAM (Pluggable authentication modules) are at the core of user authentication on modern Linux operating systems. To allow users in a specific group to switch to another user account without a password, we can modify the default PAM settings for the su command in the /etc/pam.d/su file.
# vim /etc/pam.d/su OR $ sudo vim /etc/pam.d/su
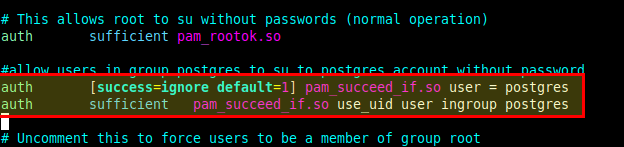
Add the following configurations after “auth sufficient pam_rootok.so” as shown in the following screenshot.
auth [success=ignore default=1] pam_succeed_if.so user = postgres auth sufficient pam_succeed_if.so use_uid user ingroup postgres
In the above configuration, the first line checks if the target user is postgres, if it is, the service checks the current user, otherwise, the default=1 line is skipped and the normal authentication steps are executed.
auth [success=ignore default=1] pam_succeed_if.so user = postgres
The line that follows checks if the current user is in the group postgres, if yes, the authentication process is considered successful and returns sufficient as a result. Otherwise, the normal authentication steps are executed.
auth sufficient pam_succeed_if.so use_uid user ingroup postgres
Save the file and close it.
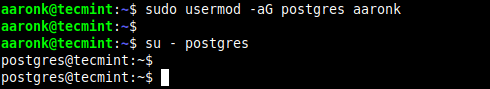
Next, add the user (for example aaronk) that you want to su to the account postgres without a password to the group postgres using usermod command.
$sudo usermod -aG postgres aaronk
Now try to su to the postgres account as the user aaronk, you should not be prompted for a password as shown in the following screenshot:
$ su - postgres
2. Using Sudoers File
You can also su to another user without requiring a password by making some changes in the sudoers file. In this case, the user (for example aaronk) who will switch to another user account (for example postgres) should be in the sudoers file or in the sudo group to be able to invoke the sudo command.
$ sudo visudo
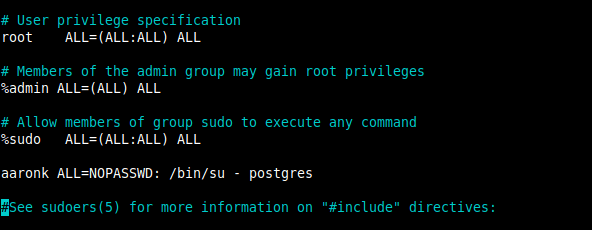
Then add the following configuration below the line “%sudo ALL=(ALL:ALL) ALL” as shown in the following screenshot.
aaronk ALL=NOPASSWD: /bin/su – postgres
Save and close the file.
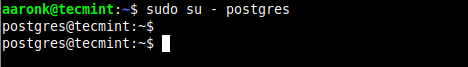
Now try to su to the account postgres as the user aaronk, the shell should not prompt you to enter a password:
$ sudo su - postgres
That’s all for now! For more information, see the PAM manual entry page (man pam.conf) and that of sudo command as well (man sudo).
$ man pam.conf $ man sudo




Note: when editing /etc/pam.d/su the place where you insert your rules is important! Do it right after ‘auth sufficient pam_rootok.so’ line at the top of the file, otherwise it will not work.
Wrong, sudo and su should never be used together…
Thank you so much for the great topic,
While passwordless login creates convenience, it also creates a security hole. Should a bad actor obtain your userid, (s)he can copy and/or destroy your entire database setup. As the database breaches at Equifax, Target, Yahoo, and hundreds of other companies show, hackers do not need any help, such as passwordless sign-ins, in breaking in.
From a security standpoint, things should be made more complicated, rather than more convenient. Each user should have his or her own strong password so that in case of a breach it can be known which userid was compromised.
The price of convenience is security.