Step 4: Configuring Gateway Group
10. After configuring Gateway monitoring, click on Groups to create a Gateway Group. Click + button right to add new GW group.
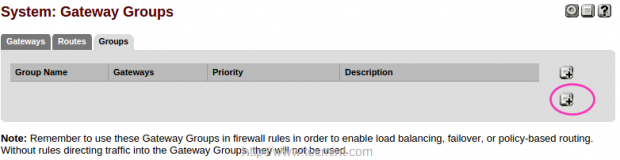
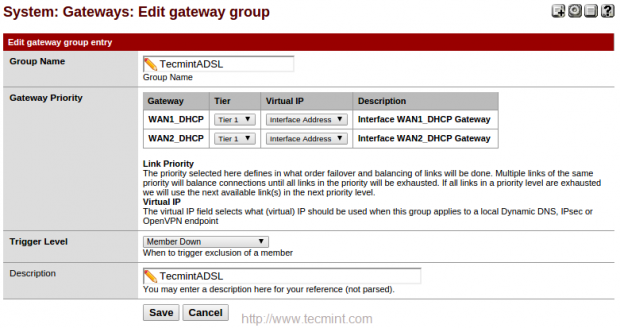
11. Give a Group Name and choose Tier for WAN1 and WAN2 and make changes by clicking on Save.
I have provided my group name as TecmintADSL and chosen tier1. To obtain a LoadBalancer we have to select more than one gateway in same tier.
Step 5: Configuring Firewall Rules
12. After creating a Group, now it’s time to create firewall rules for the created group, to assign the Rules, navigate to “FIREWALL” from top and choose “RULES“.
Choose the LAN interface and edit configuration.
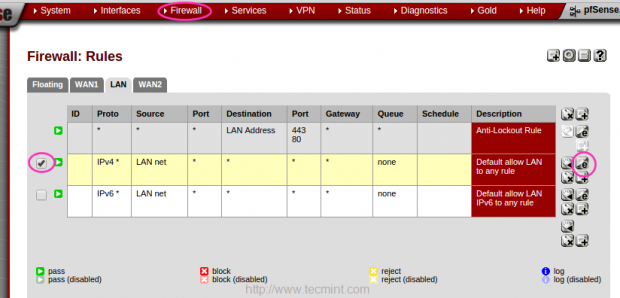
13. At the bottom of the page, choose the created Gateway Group “TecmintADSL” by clicking on Advanced under Gateway option and click on save to Apply changes to make the changes permanent.
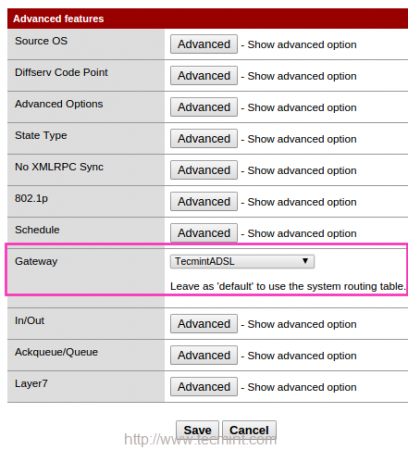
After applying modifications, you can see the gateway and advanced icon as show below.
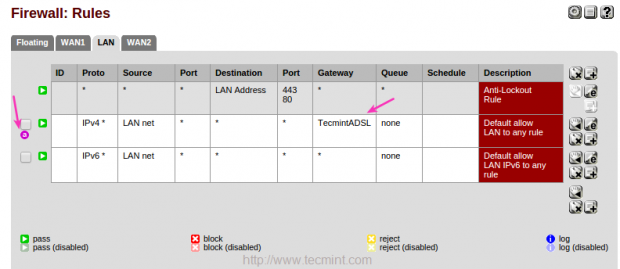
We have successfully setup-ed our LoadBalancer, Now let us verify how it work’s.
Step 6: Testing LoadBalancer
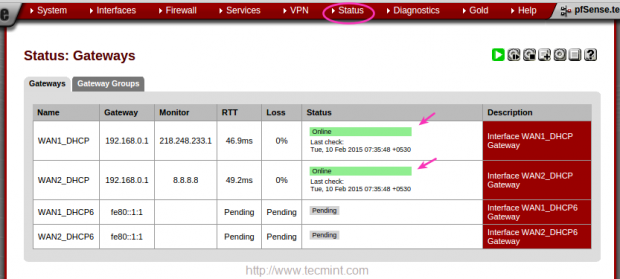
14. To verify the Load Balancer, go the ‘Status‘ from the top Menu and click on “Gateways” to verify that the both Gateways are online.
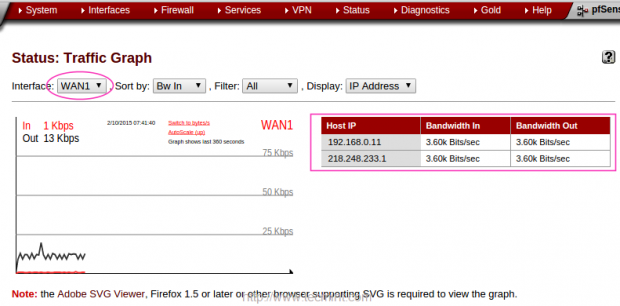
15. To get the real time Graph we can use “Traffic Graph” under “Status” menu.
Step 7: Setup Failover Using Pfsense
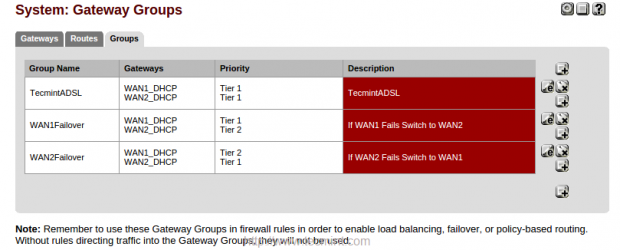
16. To setup a failover in Pfsense, we need to create different Tier, navigate to “System” menu and choose “Routing“. There we can see Gateways already assigned for LoadBalancer, so let’s create two groups for failover now.
Choose “Groups” under System: Gateway Groups. Here we will create two groups, the first group we will be creating for WAN1 and the second group for WAN2, if WAN1 fails it will automatically switch to WAN2 and vise-versa.
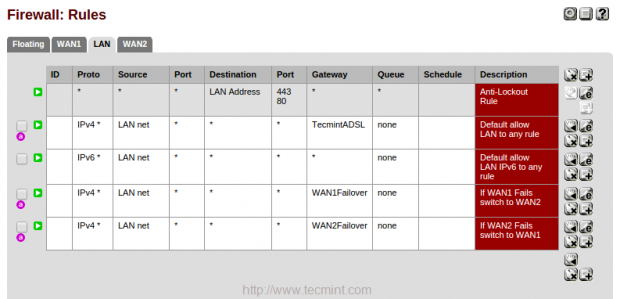
Create a Group in the name of WAN1Failover, Choose WAN1 with Tier1 and WAN2 with Tier2, if WAN1 fails it will switch to WAN2. Choose Packet Loss for Tigger Level, When ever ping reply to DNS packet Loss it will switch to WAN2.
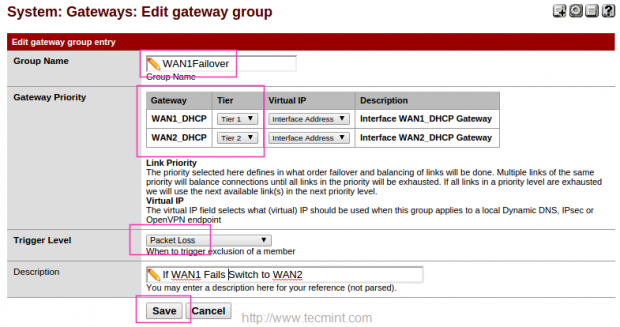
17. Follow the same above instructions for creating WAN2Failover group. Choose WAN2 with Tier2 and WAN2 with Tier1, If WAN2 fails it will Switch to WAN1. Choose Packet Loss for Trigger Level. Here to when ever ping fails to DNS it will Switch to WAN1.
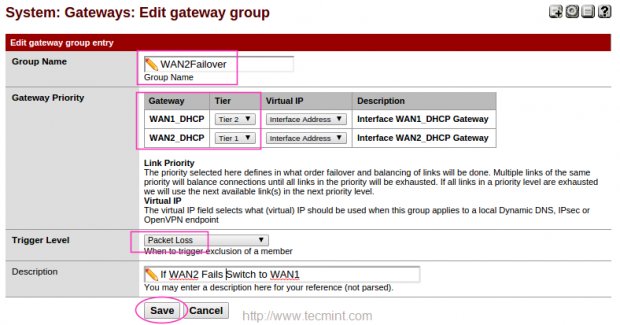
Now, we will get three groups, first for LoadBalancing, second and third for Failover.
Step 8: Configure Firewall Rules for Failover
18. Now, here we need to assign firewall rules for failover, To configure firewall rules navigate to “Firewall” and choose “Rules“. Under LAN we have to add new rules for failover.
Click on + Symbol in right side to add new rules.
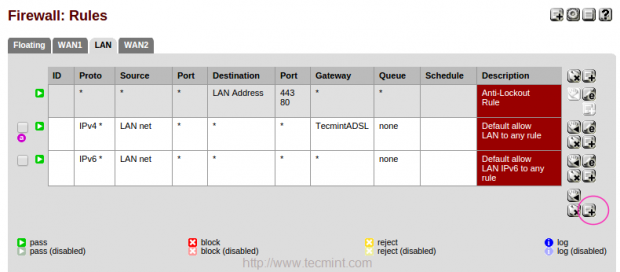
Make changes to below options.
- Interface = LAN
- Protocol = any
- Source = LAN net
- Description = What ever you wish for fail-over.
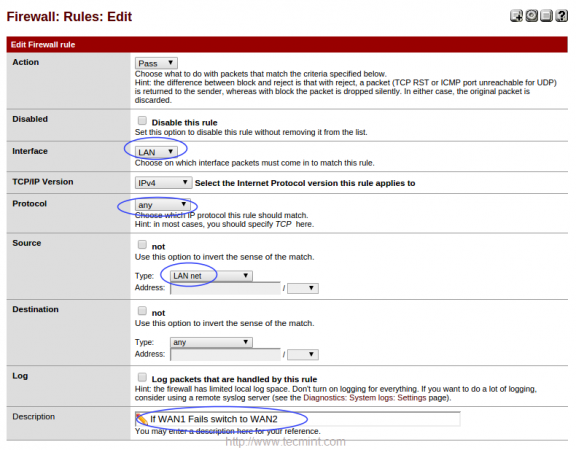
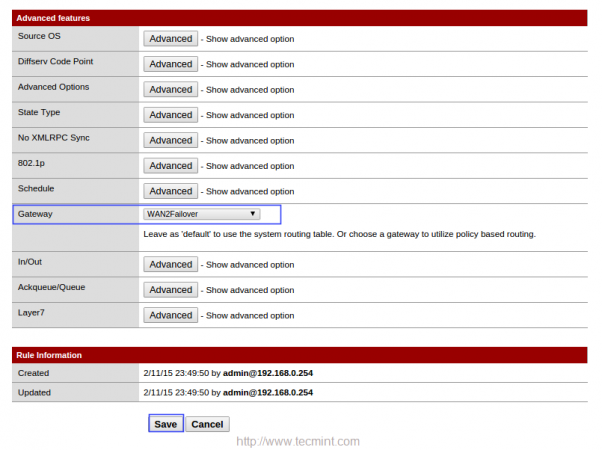
Under advance settings of Gateway choose WAN1Failover and save, repeat the same instructions to configure WAN2Failover.
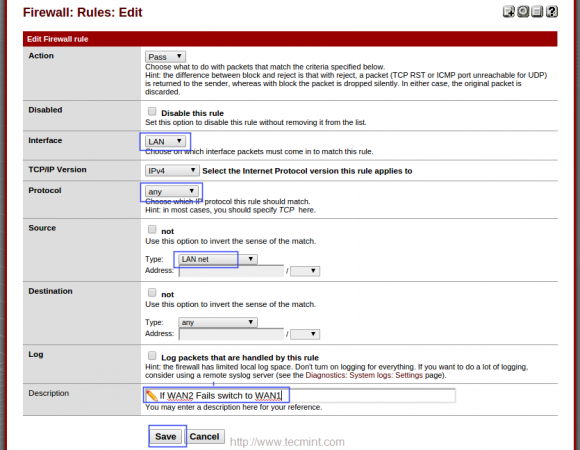
19. After adding the above rules, you can see the below listed rules for both LoadBalancer and Failover.
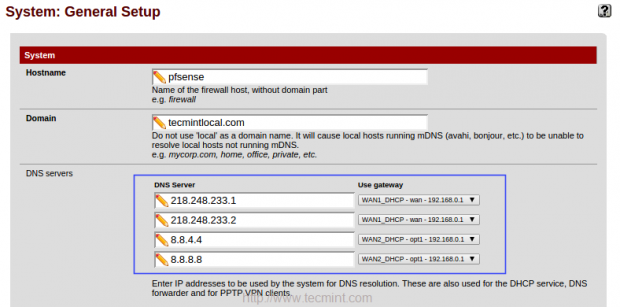
20. Now it’s time to assign at least one DNS server for our Gateway and apply changes and make sure to check the Status of our Gateway.
From “System” Menu choose “General Setup” and check for DNS respectively, which we have assigned under gateway.
Choose “Status” menu and click on “Gateways” to get the status.
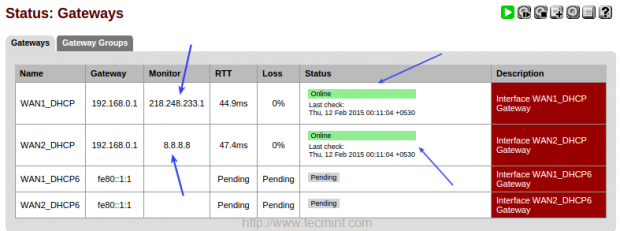
That’s it we have successfully deployed a Failover in pfsense.
Conclusion
The above pfsense LoadBalancer and Failover setup can be used in home or office environments only if you have Dual ISP connection’s. Instead of paying for a branded dedicated Router with LB options we can use this setup to build a LB with Failover.



I configured pfSense as described but found it does not work as documented (or at least as I interpreted it). In step 19 the rule with the TechmintADSL gateway will be valid for all IPv4 traffic and all IPv4 will be load balanced.
The 2 rules with WAN1Failover and WAN2Failover as gateways will never be used since all traffic match the rule higher in the list. This is exactly what my configuration was doing.
You would either have to limit the traffic for each rule so that they cover specific traffic that doesn’t overlap with another rule below it. In other words, you might have a rule with WAN1Failover that matches http/https traffic and another rule for TechmintADSL that matched anything to send everything else via load balancing.
Hello ! please i have a question how i can test the 2 WANs by putting one of them up or down
i don’t know how to test it
I did exactly as in guide, but performance is horrible. With dual WAN my overall speed is same as one WAN.
Tested with 5 clients connected to pfsense doing various different transfers over the internet.
Please write how to fix this.
Hello I did these instructions and it was successfully been worked with the process but the problem is the traffic shaper or limiter is not working properly I set up some 2 mpbs in and out but the result in speed test is now with the given speed. how should i fix this?
thank you in advance
Hello,
I would like to know if this one will work on the same ISP with the same gateway?
thanks
Hi,
In a corporate scenario, we have 2 link with 5 public IP each, resulting 10 public IP in total
Once load balancing on PFsense is enabled, is it possible to combine it together?
For example, the network is (Link 1/Link2) > PFsense > Microsoft TMG > Internal network
Possible to publish services on all ten public IP?
Hello Sir, I just want to know, we have configured multi wan, in this case i think if one interface goes down another will be automatically up then why we need to create wan1 fail over, and wan2 fail over rule. correct me if i am wrong .
@Sameer,
More failover setup, More uptime.
Tks. very nice!!! work!!
Hi, with this configuration, it makes NAT to LAN computers?
Thanks! Nice post
@Lucas Soares,
Pfsense = Router
No this regarding load balancing between two NIC which connected to Internet in pfsense.
Ravi I am having the same issue. Might be a bug!!!
@Mark,
Current updated version released 2.3.2
When WAN1 is down DNS is not resolving on WAN2
Same problem here.
i really would like to thank you for your Great Discription .
thank you Very Much
Thank you
Nice Article!
Although the last two rules doesn’t make much sense cause with Load Balancing there is also Fail Over implicit. When one GW goes down it’s removed and the other continues to operate normally (doing fail over), this is explained on pfSense doc https://doc.pfsense.org/index.php/Multi-WAN
thanks, i was like.. why is he doing that??
The fail-over rules would be useful for traffic that you want to go through A SINGLE GATEWAY. For example, I have a setup where all HTTPS traffic goes through one gateway and is not balanced. But if that gateway is down I need it to failover to the next available gateway.
You should only to create a single fail-over Gateway Group and set the gateway priority through the Tiers options. I did setup multiple fail-over groups though so I can have all SIP traffic on WAN1 with fail-over and all FTP traffic is on WAN2 with fail-over and so on and all 2082 traffic on WAN3, etc… This way I can keep my total traffic balanced between my 3 gateways.
Hi Babin Lonston,
i already try your tutorial, i have problem , where connection switch wan1 to wan2 , able to ping google.com , but if i try browsing, google.com cant connect. please your advice. thanks
Waiting for the pfSense+Squid Proxy+LoadBalancer/Failover … article !
@Naveen,
Your requested article is approved, give us some time to prepare and publish..
Hello Babin,
We have a small hotel with 50 rooms, so 150 to 180 customers total.
We give free wifi internet access to our customers through 5 wifi outdoor routers with different SSID like Hotel01, Hotel 02, etc.
The main problem of our Local area is that the ISP companies can’t give us ADSL lines Up To 2Mbps, So we have 5 Lines of 2Mbps. :o
This days we use them like 1 ADSL line to 1 Wifi Router and so on.
I Read a lot topics here and I see some videos over You tube That explain how we can have Load Balancing – Multi Wan and Fail Over, but I see that anyone explains how you can do it with 3 or 4 or 5 connection.
So the question is: Can we have Load Balancing – Multi Wan and Fail Over over 5 wan connections? Is it possible? Is it possible if we have different ISP companies? Like 3 Lines over ISP 1 And 2 Lines over ISP 2 and all them Load Balancing together? 8)
Just for test I install Pfsense in old PC with 3 interface and with 2 wan connections (some ISP) and all work good. Load Balancing, Fail Over!! We get 3.8Mbps Download and 512 Up ( 2 X 256).
So now I know that I can work with 2 lines, but before buy a server for that, so I thought why not post to your great and helpful Forum to ask!!
The server that I have in mind will be Pfsense C2758 1U Rack Mountable with 2 or 4x Intel 1GbE. (When you start a job, start it with the right tools) :D
I’m not a network expert or network administrator or IT manager, but I love Networks and Computers and i want to give to my hotel customers best facilities
Thanks a lot. Great guide!!!
Hi Bora550,
You can do Load Balancing with the three connections, bare in mind that you also get fail over when using load balancing, but you should assign different weights to the connection (pfSense uses a scale from 1 to 5). In your case you can assign 4 to the 80M links and 1 to the 20M, in this way the load balancing algorithm will route more traffic through the 80M links.
I hope it helps! :)
Quick query – I have 3 WAN connections.
2 are at 80Mbps
1 is at 20Mbps
One person has suggested to not load balance all 3 but to balance with the 2x80s, and failover to the 3rd one.
What do you think?
@Rob
Awesome go-head to implement as your suggestion, good idea.
Say I have 5 WAN connections (yes, I really will… 1 cable connection and 4 4G LTE modems). That’s a lot of failover rules! What would you suggest in this situation? I was thinking about creating failover rules that account for 1 failure each out of the 5 connections (set remaining 4 on same tier) and then a sixth one where I have 2 tier 1, and 3 tier 2 connections. I figure I have to edit the config for the last failover rule on the fly (set the 2 tier 1 connections to the failed WANs) and I should have ample warning time to do that. Let me know your thoughts on this!
Also, have you experienced any issues relating to websites making sure a user keeps connecting from the same IP (sticky connections)? Or at least problems with Google, Facebook, Twitter (or any big all HTTPS site)? Thanks for any suggestions you’re able to provide and this is the best write-up I’ve seen so far on thsi topic!
Hi – really nice post, thanks. Will this work with 3 x PPPoE, 2 set as load balancing and one set as failover?
If yes as I suspect, can the failover connection still accept incoming packets and forward to one of our servers?
//Hi – really nice post, thanks.//
Thanks for your valuable feedback
//Will this work with 3 x PPPoE//
Yes this will work with 3 PPPOE connections without any issue.
//2 set as load balancing//
Only one Loadbalacing will be good idea, Cos combining three connections to get 1, If your three connections each with 24 MB connections your LB will get 72 MB connection.
//one set as failover?//
Can have 2 set of failover.
Dont work here… pfsense 2.2… :( all WAn’s are pppoe!
//Dont work here… pfsense 2.2… :( all WAn’s are pppoe!//
Sure it will work seems there is some of mis-configuration
What modifications needs to be done in this tutorial if I have only one WAN interface? Also, can you please explain load balancing further (as I am not an expert, my basics not clear!), my specific question is if I combine 2+2 Mbps WAN connections, will I get 4 Mbps effective download speed?
Thank you very much for this great article, Tecmint is helping us a lot!!
//What modifications needs to be done in this tutorial if I have only one WAN interface? //
If you have only one interface you can’t do Loadbalancing, Failover.
//Also, can you please explain load balancing further (as I am not an expert, my basics not clear!), my specific question is if I combine 2+2 Mbps WAN connections//
Yes you will get 4 MB speed try to download anyone of file and check. Only if you have configured Loadbalancer this will work.
Thanks for your comment… Let me know how went through for you.
Thanks for your valuable reply! I will surely setup and test this great feature. Any same future article/same tutorial for combining pfSense+Squid Proxy+LoadBalancer/Failover will be welcome! Till now I am using just IPtables firewall+Squid Proxy, but now I am looking for more advanced configurations like these, can you point me to any tutorial which combines pfSense Firewall+Squid Proxy+Load Balancer & Failover?
Thanks again, Tecmint & its experts are really empowering us!!
\\combining pfSense+Squid Proxy+LoadBalancer/Failover will be welcome\\ Already Prepared have to publish shortly..
Thanks my friend… I have been looking for it by long time. But I have over 15% of loss on wan1 with google gateway and i dont know why… one hour later.. i have 0% in wan1 but 16% on wan2 of loss.
Check your gateway with continuous ping and make sure whether it have any packet loss.
Thnks. I Will do it and I will comment to you.
Great post, Thanks for the sharing detailed info.
Thanks for you positive feedback :)