In Part 10 of the LFCA series, we brushed over the classes of IP addresses and gave examples of the commonly used IP classes. However, that was just an overview and in this part, we will dive deeper and gain more understanding about IP addressing range and the number of hosts and networks each class of IP provides.
Classes of IP Addresses
There are 3 main classes of IP addresses which can be organized in the table below:
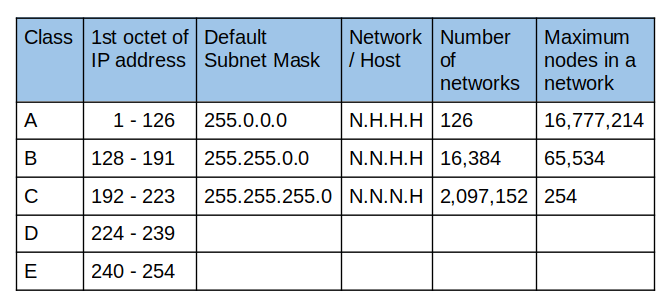
Let’s go through this row by row.
Class A Network
Class A has an address range from 0.0.0.0 to 127.255.255.255. The default subnet mask is 255.0.0.0. That implies that the first 8 bits are used for the network address while the remaining 24 bits are reserved for host addresses.
However, the leftmost bit is always 0. The remaining 7 bits are designated for the network portion. The remaining 24 bits are reserved for host addresses.
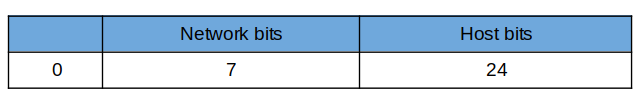
Therefore, to calculate the number of networks, we will use the formula:
2⁷ – 2 = 126 networks. We are subtracting 2 because 0 and 127 are reserved network IDs.
Similarly, to calculate the hosts we apply the formula shown. We are subtracting 2 because the network address 0.0.0.0 and broadcast address 127.255.255.255 are not valid host IP addresses.
2²⁴ - 2 = 16,777,214
Class B Network
Class B has an address range of 128.0.0.0 to 191.255.255.255. The default subnet mask is 255.255.0.0. Ideally, we would have 16 network bits from the first 2 octets.
However, the leftmost bits are 1 and 0 and that leaves us with only 14 network bits.
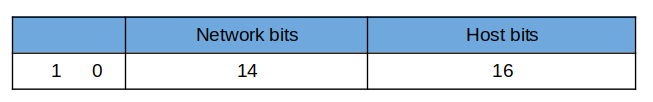
So, for the number of networks, we have:
2¹⁴ = 16384
For host addresses, we have:
2¹⁶ - 2 = 65,534
Class C Network
Class C has an IP range of 192.0.0.0 to 223.255.255.255 with a default subnet mask of 255.255.255.0. This implies we have 24 network bits and 8 host bits.
However, starting from the left, we have 3 bits which are 1 1 0. If we subtract the 3 bits from the 24 network bits, we end up with 21 bits.
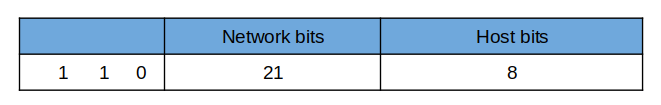
So, for networks, we have:
2²¹ = 2,097, 152
For host addresses, we have
2⁸ - 2 = 254
Private and Public IP Addresses
All IPv4 addresses can also be categorized as either Public or Private IP addresses. Let’s distinguish the two.
Private IP Addresses
Private IP addresses are addresses that are assigned to hosts with a Local Area Network (LAN). Hosts within the LAN use private IP addresses to communicate with each other. Each host acquires a unique IP address from the router
Below is a range of Private IP addresses:
10.0.0.0 – 10.255.255.255 172.16.0.0 – 172.31.255.255 192.168.0.0 – 192.168.255.255
Anything outside this range is a public IP address which we will look at shortly.
Public IP Addresses
Public IP addresses are assigned over the internet. Typically, your ISP (Internet Service Provider) assigns you a public IP address. The public IP is then mapped to private IP addresses in your LAN with the help of NAT, short for Network Address Translation. NAT helps multiple hosts in a Local Area Network to use a single Public IP address to access the internet
Since the public IP is assigned to you by your ISP, it attracts a monthly subscription, unlike private IP addresses which are freely assigned by your router. The scope of a public IP is global. Public IP addresses give access to online resources such as websites, FTP servers, web servers and so much more.
To know the public IP you are using, simply open your browser and Google search ‘what is my IP address‘. Click on the list of links suggested to reveal your public IP address.
Examples of Public IP address include:
13.25.8.5.63 3.8.45.96 102.65.48.133 193.150.65.156
The TCP/IP Model: Layers & Protocol
The TCP/IP model is a 4-layer conceptual model that provides a set of rules and communication protocols that are used in computer networks and over the internet. It offers a glimpse of how the transmission of data takes place in a computer
The four layers are as shown:
- Application Layer
- Transport Layer
- Internet Layer
- Network Layer
To get a better visual, below is the TCP/IP layer model.
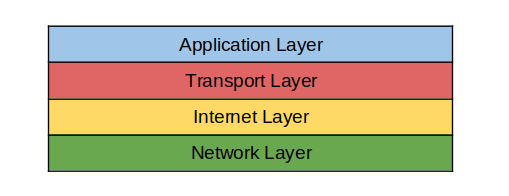
Let’s get a better understanding of what happens in every layer.
1. Network Layer
This is the most basic or rudimentary layer in the TCP/IP model. It determines how data is physically sent across the network. It defines how the transmission of data occurs between two network devices. This layer is dependent on the hardware used.
Here, you will find data transmission cables such as Ethernet / Twisted pair cables and Fiber.
2. Internet Layer
The second layer is the Internet Layer. It is responsible for the logical transmission of data packets over the network. Additionally, it determines how data is sent and received over the internet. In the internet layer, you find 3 main protocols:
- IP – As you might have guessed, this stands for Internet Protocol. It delivers data packets from the source to the destination host by leveraging the IP addresses. As we discussed earlier, IP has two versions – IPv4 and Ipv6.
- ICMP – This is an acronym for Internet Control Message Protocol. It is used to probe and diagnose network problems. A good example is when you ping a remote host to check whether it is reachable. When you run the ping command, you send an ICMP echo request to the host to check whether it is up.
- ARP – This is short for address resolution protocol. It probes for a hardware address of a host from a given ip address.
3. Transport Layer
This layer is responsible for end-to-end communication and delivery of error-free data packets from one host to another. The transport layer comprises two key protocols.
- TCP – Short for Transmission Control Protocol, TCP provides reliable and seamless communication between hosts. It segments and performs sequencing of data packets. It also performs error detection and subsequently retransforms damaged frames.
- UDP – This is the User Datagram Protocol. It is a connectionless protocol and doesn’t provide as much reliability and flawless connection as the TCP protocol. It is mainly used by applications that don’t need a reliable transmission.
4. Application Layer
Finally, we have the Application layer. This is the top-most layer that provides protocols that software applications use to interact with. There are a myriad of protocols on this layer, however, we have listed the most commonly used protocols and corresponding port numbers.
|
Protocols |
Ports |
Description |
|
FTP |
20/21 |
File Transfer Protocol. Allows transfer of files between computers |
|
SSH |
22 |
Secure Shell. Provides a secure or unencrypted connection between host systems |
|
TELNET |
23 |
Provides insecure connection to remote hosts |
|
SMTP |
25 |
Simple Mail Transfer Protocol. Facilitates delivery of mail |
|
DNS |
53 |
Domain Name System. Resolves domain names to IP addresses |
|
HTTP |
80 |
HyperText Transfer Protocol. Allows access to web servers |
|
POP3 |
110 |
Post Office Protocol. Allows the download of mail from mail servers |
|
IMAP |
143 |
Internet Message Access Protocol. It Allows access to mail stored on a mail server. |
|
SNMP |
161 |
Simple Network Management Protocol. Allows you to monitor network devices. |
|
HTTPS |
443 |
This is the secure or encrypted version of HTTP. Provides secure access to web servers. |
The TCP/IP model is mostly used for network troubleshooting and is sometimes compared to the OSI model which is a 7 layered model and which we shall cover in the troubleshooting section.
This wraps up the networking essentials series. It’s our hope that you have gained a basic understanding.







“However, starting from the left, we have 3 bits which are 1 1 0. If we subtract the 3 bits from the 24 network bits, we end up with 21 bits.”
Why are the 3 bits being subtracted?
We are subtracting the first three bits because these are the first leading bits of the Class C IP addressing and, therefore, do not constitute the Network ID.
Hi,
Thanks a lot for this great article with a clear explanation…