Linux is generally more secure than many other operating systems. A key part of this security comes from user management and permissions, which control who can do what on the system. By default, normal users cannot perform system-level operations.
When a regular user needs to make changes that affect the entire system, they must use either the su or sudo command to gain temporary administrative privileges.
Understanding su and sudo?
The following explanation is based on Ubuntu-based distributions, but it applies to most popular Linux distributions.
su(substitute user) – This command lets you switch to another user account, usually the root account. To use it, you need the root password, which means sharing this password with others if they also need access, which is considered risky.sudo(superuser do) – This command allows a user to execute specific system commands with administrative privileges without sharing the root password. Instead, users enter their own password, which provides safer delegation of responsibilities.
Example:
# Using su to switch to root su - Password: [root password here] # Using sudo to update packages sudo apt update [sudo] password for user: [your password here]
As you can see, sudo provides a safer and more flexible way to perform administrative tasks compared to su.
What is sudo?
sudo is a special program (setuid binary) that allows authorized users to run commands as the root user or another user. It provides a safe way to perform administrative tasks without sharing the root password.
When you use sudo, you must enter your own password, not the root password, which ensures accountability for every command you run is tied to your account.
In the following example, the Apache web server restarts with root privileges, do notice that the user never types the root password; their own password is used instead.
sudo systemctl restart apache2
Who Can Use sudo?
The list of users who can run sudo is controlled in the /etc/sudoers file, which can be edited by the visudo command to avoid syntax errors that can break your system:
sudo visudo
A default entry looks like this, which means the root user can run any command on any host as any user.
root ALL=(ALL:ALL) ALL
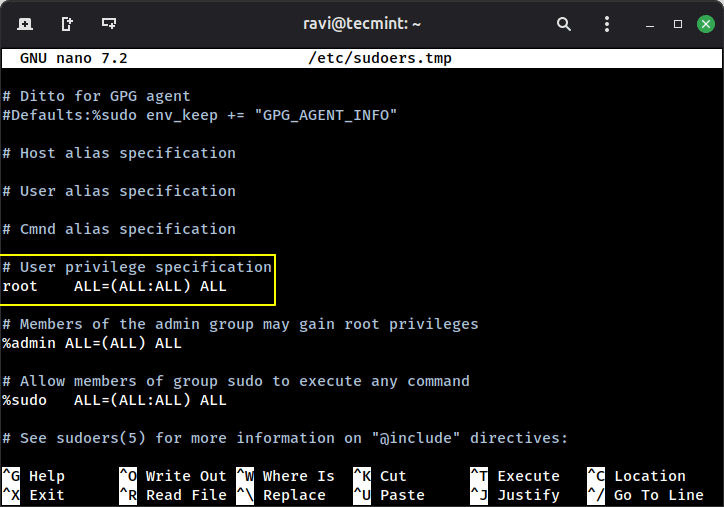
Granting sudo Access to Other Users
Giving unrestricted sudo access to multiple users can be risky. If every user can run any command as root, a simple mistake or a compromised account could break the system or expose sensitive data.
Dangerous example (don’t do this):
adam ALL=(ALL:ALL) ALL tom ALL=(ALL:ALL) ALL
Here, adam and tom can run any command as root on any machine, which effectively gives them full administrative power similar to root user.
Instead, grant only the specific privileges each user needs, as explained below.
Understanding sudo Syntax
A properly configured sudo is very flexible, and the number of commands a user can run may be precisely configured.
The syntax of a configured sudo line is:
User_name Machine_name=(Effective_user) command
This syntax can be divided into four parts:
- User_name → Name of the
sudouser. - Machine_name → Hostname where the
sudocommand is valid, which is useful when you have multiple hosts. - effective_user → The user as whom the command will run (for example, root or another account).
- command → The command or commands that this user is allowed to execute.
This structure allows administrators to give precise control over what each user can do, instead of giving full root access.
Example sudo Configurations
Here are some common situations and how you can configure sudo for each:
1. Granting Full Database Access to a Specific User
You have a user mark who is a Database Administrator, and you want him to have full access to the Database Server beta.database_server.com, but no access on other hosts, your sudo line should be:
mark beta.database_server.com=(ALL) ALL
2. Running Commands as a Specific Non-root User
You have a user tom who should execute system commands as a specific user (not root) on the same Database Server?
tom beta.database_server.com=(tom) ALL
3. Restricting a User to a Single Command
You have a sudo user cat who should only run the command dog.
cat beta.database_server.com=(cat) dog
4. Allowing a User to Run Multiple Commands
A user needs to execute several commands, but the list is short (fewer than 10 commands).
cat beta.database_server.com=(cat) /usr/bin/command1 /usr/sbin/command2 /usr/sbin/command3
For longer lists of commands, it is better to use aliases.
User_Alias ADMINS=tom,jerry,adam User_Alias WEBMASTERS=henry,mark WEBMASTERS WEBSERVERS=(www) APACHE Cmnd_Alias PROC=/bin/kill,/bin/killall,/usr/bin/top
You can also assign commands to an entire group by prefixing the group name with %:
%apacheadmin WEBSERVERS=(www) APACHE
5. Allowing sudo Without a Password
A user needs to run specific commands without entering a password.
adam ALL=(ALL) NOPASSWD: PROCS
Here, user adam can execute all commands aliased under PROCS without entering a password.
Summary
sudo provides a robust and safe environment with flexibility compared to su. Moreover, sudo configuration is easy. Some Linux distributions have sudo enabled by default, while most of the distros today require you to enable it as a security measure.
To add a user (bob) to sudo, just run the following command as root:
adduser bob sudo
That’s all for now. I’ll be back with another interesting article. Till then, stay tuned and connected to Tecmint. Don’t forget to provide us with your valuable feedback in the comment section.





Hi,
Really very nice tutorial, I would like to know if there is a way to exclude some admin to run any configuration in ssh?
Hi Ravi,
I am facing one problem with /etc/sudoers or visudo, Actually, While I am adding a user with adduser command and while I am not providing any sudo access but commands are working without password or without any permission error.
I am using e.g: Lucky ALL=(Lucky) NOPASSWD: /bin/*, !/bin/rm.
and also I am restricting for rm command but rm command is working.
Please help me brother and please clarify my doubts.
These comments are based on a multi user environment. In the case of shared computers of truly multi-user systems, sudo makes sense. However for single user systems and administrator use, su makes more sense for a variety of reasons including convenience and environment configuration.
I do understand the confusion in this regard, especially with younger users, as Ubuntu started this confusion by misusing sudo to give it a more Windows like admin configuration model for individual admin tasks as it utterly lacks any unified administration interface where you’d give the root password once to enter and configure the system.
So for example, as an administrator of my system, I keep a terminal shell open in which I’ve su’d to root and use that shell for all admin tasks.
If I wanted to allow other users of the system to have access to network configuration or printer setup, I’d use sudo to allow access to those tools.
Hi Ravi Saive,
Good evening.
I have a doubt in the below line.
mark beta.database_server.com=(tom) ALL
My understanding is ‘mark’ and ‘tom’ both are the sudo users, both users have same (ALL commands )access on beta.database_server.com machine.
Is this correct? or any difference is there in between ‘mark’ and ‘tom’ users in terms of privileges on beta.database_server.com machine?
Thanks in advance.
Thanks
Could you please explain more about Q2, i didn’t quite catch that. As per to the question, user tom which is supposed to execute system command as user other than root on the same database server.
mark beta.database_server.com=(tom) ALL
Mark — Sudo User
beta.database_server.com — machine name
tom — effective user
ALL — Any command can be executed
After login with Mark user, try executing commands it says permission denied. Would you please provide more clarification
try with pater# sudo -u tom any_sytem_command
you may find more examples from below link
http://www.linuxhomenetworking.com/wiki/index.php/Quick_HOWTO_:_Ch09_:_Linux_Users_and_Sudo#.V4H6__l97IV
How can I get sudo to use the root aliases in /etc/bashrc?
@Roger,
That’s not possible, either add aliases to sudo user .bash_profile file, or for global use add in /etc/profile file.
Hi friends,
I have two user accounts. let test1 and test2. How can I switch to test2 from test1 without prompting password.
:$su test2
Any idea, please contact me at [email protected]
@Mushthaq,
That’s not possible, because both are different users with different home directories, you must enter password to login to user account..
What if the password is not set for neither of the users? It still prompting for password and what we have to give?
Is there a way to exclude a command for a sudo user?
Can u clear Q2 please, cause it is not clear . Thanks.
Here is the a link to the man page:
http://linuxcommand.org/lc3_man_pages/su1.html
I agree with Tomas,
su means Substitute User. So we can use su to switch user temporarily. In this way we can switch to root user. The sudo one gives temporarily root privileges, using the normal user password.
I really do not understand this article :(.
What a misleading article name that is.
You use “sudo” when you need to execute a command as a superuser. You use “su” when you want to switch to another user’s account, or, execute a command AS another user, not necessarily a superuser.
Saying that “su forces you to share your root password to other users whereas sudo makes it possible to execute system commands without root password” shows you having no idea what the real purpose (and the difference) is.
1. I read as far as the second mention of “editing the /usr/sbin/visudo file” .. The file you are editing is in fact /etc/sudoers. /usr/sbin/visudo is the binary you are running.
2. As has been pointed out, su is mainly used to switch to another user’s shell. sudo is mainly there for scripts, but it also allows you to centralize configuration and as you describe, no additional password requirements.
You can do with sudo exactly the same as you would with su ([sudo -u $newuser -i] for example is the same as [su – $newuser] – although you have to be weary of some environment variables).
3. sudo may or may not be SUID (as SELinux becomes more popular, the settings are actually going in there rather than SUID).
4. “Parameters of sudo” looks like it should actually be “Syntax of sudoers file” or “Syntax of sudo config”… Parameters are what you pass on the command line.
5. adduser instead of useradd? You must really only know specific linux’s as useradd is the traditional Unix command (and adduser is actually a symbolic link to the correct useradd command… no idea why)
6. It doesn’t look like you’ve stated you always need to use the full path name to the binary in the config file (dog will not do – it has to be /path/to/dog).
7. “Linux System is much secured than any of its counterpart.” – I’m pretty sure several BSD fanatics will disagree with you there. BSD (kernel) is built with security more in mind – Linux (kernel) is built with more compromises and different ideals.
@Tomas
In his context, Technically he is correct.
From su man page
su(1)
su – change user ID or become superuser
One comment about the article, you dont need root password to use su
su default is root but not only that
if I want to change my user id to become user test I run
su test
and I need test user password not root password
Best regards
Rodrigo Gonzalez
Dear Sir,
I have a query. It’s not related to this post.
How to assign hard quota to limited user in centos/Ubuntu ?
Kindly let us know about this.
Thanks,
Manoj Gupta
Plz provide video tutorial
Dear Gurdip,
we are working on Video Tutorials.
Please hold with us, till then.
Keep connected with us.
If a newbie ask me what different between su and sudo, i simply answer that su require root password where sudo require your cyrrent password. :D
Dear Quovadis,
we prepare our post after several hours of study, research, test before making it available to you. Our post is for Newbies as well as advanced users. Actually we write our contents from every possible user perspective.
Keep connected to Tecmint for such detailed posts.
Hello Sir,
Thanks for this article, because i thought that both are same but this article clear me différence between both.
Regards,
Manoj
Dear Manoj,
It was very pleasing to know our posts helped you.
Keep connected to Tecmint for more such posts.
Refer to your friends and colleagues.