If you are using Computers for while, you must be familiar with the word “Firewall”. We know that things do seem complex from the surface but through this tutorial, we are going to explain the basis of IPTable and the use of basic commands so that even if you are a networking student or want to deep dive into networks, you can benefit from this guide.
What is IPTables?
The way the Firewall works is quite simple. It creates a barrier between trustworthy and untrustworthy networks so your system can be safe from malicious packets.
But how we are going to decide what is safe and what not? By default, you do get some privilege to set up rules for your Firewall but for more detailed surveillance of incoming and outgoing packages, IPTables are what you require the most.
IPTables can be used for personal computing or can also be applied to the entire network. Using IPTables, we will be defining a set of rules by which we can monitor, allow or block incoming or outgoing network packets.
Rather than just focusing on the entire theory part, we are only going to discuss what matters in the practical world. So let’s start with understanding the core concepts of IPTables.
Understanding the Concept of IPTables
While discussing IPTables, we must understand 3 terms: Tables, Chains, and Rules. As these are the important parts, we are going to discuss each of them.
So let’s start with Tables.
Tables in IPTables
There are 5 types of tables in IPTables and each has different rules applied. So let’s start with the most common table “Filer”.
- Filter Table – This is the default and main table while using IPTables. It means whenever you won’t mention any specific table while applying rules, they will be applied to the filter table. As its name suggests, the role of the Filter table is to decide whether the packages should be allowed to reach their destination or deny their request.
- NAT (Network Address Translation) – As its name suggests, this table allows users to determine the translation of network addresses. The role of this table is to determine whether to modify and how to modify the source and destination of the packet address.
- Mangle Table – This table allows us to modify the IP headers of packets. For example, you can adjust TTL to either lengthening or shorting network hops that the packet can sustain. Similarly, other IP headers can also be modified according to your preference.
- RAW Table – The main use of this table is to track connections as it provides a mechanism for marking packets to view packets as a part of an ongoing session.
- Security Table – Using the Security table, users can apply internal SELinux security context marks on network packets.
For the most use cases, the last 2 types (RAW and Security) of the table don’t have much to do and only the first 3 options are counted as main tables.
Now, let’s talk about Chains.
Chains in IPTables
They behave at points in the route of the network where we can apply rules. In IPTables, we 5 types of chains and we will discuss each of them. Keep in mind that not each type of chain is available for each type of table.
- Pre-routing – This chain is applied to any incoming packet once it is entered the network stack and this chain is processed even before any routing decision has been made regarding the final destination of the packet.
- Input Chain – It is the point where a packet enters the network stack.
- Forward Chain – It is the point where the packet has been forwarded through your system.
- Output Chain – The output chain is applied to the packet when it originated through your system and goes out.
- Post-routing – This is the complete opposite of the pre-routing chain and is applied to forwarded or outgoing packets once the routing decision has been made.
Now, the only thing left to discuss is rules, and it’s the easiest one out of the 3 that we have discussed here. So let’s complete what’s left on the theoretical part.
Rules in IPTables
Rules are nothing but the set or individual commands by which users manipulate network traffic. Once each chain will come into action, the packet will be checked against defined rules.
If one rule does not satisfy the condition, it will be skipped to the next one and if it satisfies the condition, the next rule will be specified by the value of the target.
Each rule has two components: the matching component and the target component.
- Matching Component – They are different conditions to define rules which can be matched by protocol, IP address, port address, interfaces, and headers.
- Target Component – This is an action that will be triggered once the conditions are satisfied.
This was the explanation part and now we will be covering basic commands related to IPTables in Linux.
Installing IPTables Firewall in Linux
In modern Linux distributions such as Pop!_OS, IPTables comes pre-installed but if your system lacks the IPTables package, you can easily install it by given instructions:
To install IPTables on RHEL-based Linux distributions such as Rocky Linux, AlmaLinux, and CentOS Stream, use the following dnf command.
$ sudo dnf install iptables-services
Important: If you are using Firewalld, you’ll have to disable it before proceeding to installation. To stop the firewall completely, you’ll have to utilize the following commands:
$ sudo systemctl stop firewalld $ sudo systemctl disable firewalld $ sudo systemctl mask firewalld
To install IPTables on Debian-based Linux distributions, use the following apt command.
$ sudo apt install iptables
Once you install IPTables, you can enable the firewall by given commands:
$ sudo systemctl enable iptables $ sudo systemctl start iptables
To monitor the state of the IPTable service, you can use the given command:
$ sudo systemctl status iptables
Learn Basics of IPTables Command in Linux
Once we are done with the installation, we can proceed with the syntax of IPTables which will allow you to tweak defaults and allow you to configure as per your needs.
The basic syntax of IPTables is as follows:
# iptables -t {type of table} -options {chain points} {condition or matching component} {action}
Let’s understand the explanation of the above command:
Table
The first part is -t where we can choose from any 5 available table options and if you remove the -t part from the command, it will use filter table as it is the default table type.
Chain Options
The second part is for the chain. Here you can choose from different chain point options and those options are given below:
-A– Adds a new rule to the chain at the end of the chain.-C– Checks for rule whether it satisfies the chain’s requirement.-D– Allows users to delete an existing rule from the chain.-F– This will remove each rule defined by the user.-I– Allows users to add a new rule at the specified position.-N– Creates an entirely new chain.-v– When used with the list option, brings detailed information.-X– Deletes chain.
Matching Component
Matching options are the condition for checking the chain’s requirement. You can choose from various options and some of them are given below:
Protocols -p Source IP -s Destination IP -d IN interface -i OUT interface -o
For TCP, they are as follows:
-sport -dport --tcp-flags
Action Component
Now, if we consider the action part, the available options depend on the type of table such as NAT, and the mangle table has more options compared to others. By using action, you can also target a specific table or chain.
The most used action is Jump (-j) which will give us several options such as:
- ACCEPT – It is used to accept packets and end traversing.
- DROP – It is used to drop packets and end traversing.
- REJECT – This is quite similar to DROP but it sends rejected packets to the source.
- RETURN – This will stop traversing of the packet in the sub chain and will send the specific packet to the superior chain with no effect.
Once we are done with syntax, we will show you how you can use IPTables including basic configuration.
Listing Current Set of IPTables Rules
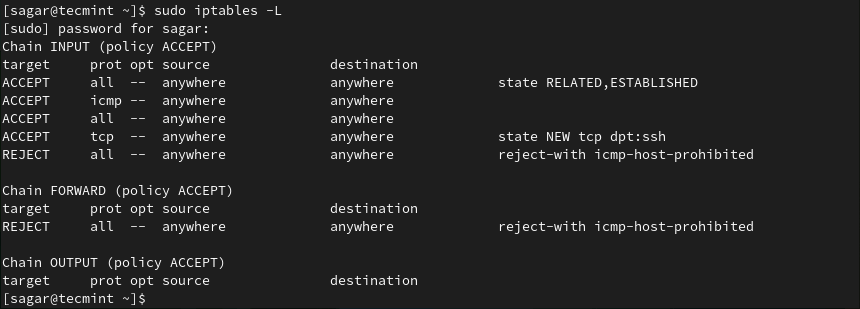
If you want to check what is passing through your Firewall by default, listing a current set of rules is a perfect way. To list applied rules, use the given command:
$ sudo iptables -L
Allow/Deny Network Traffic on Specific Ports
In this section, we will show you how you can allow or deny network traffic for specific ports. We will show you some well-known ports as we want to be as helpful as we can be.
If you want to allow HTTPS network traffic, we will have to allow port no 443 by utilizing the given command:
$ sudo iptables -A INPUT -p tcp --dport 443 -j ACCEPT
Similarly, you can also disable HTTP web traffic by given command:
$ sudo iptables -A INPUT -p tcp --dport 80 -j REJECT
Explanation of used command options:
-pis used for checking specified protocol and in our case it’s TCP.--dportis used for specifying the destination port.-jis used for taking action (accept or drop).
Control Traffic with IP Address
Yes, you can also control network traffic from an IP address. Not just one or two but also control the range of IP addresses and we will show you how.
To allow a specific IP address, utilize the given command structure:
$ sudo iptables -A INPUT -s 69.63.176.13 -j ACCEPT
Similarly, to drop packets from specific IP, you are required to use the given command structure:
$ sudo iptables -A INPUT -s 192.168.0.27 -j DROP
If you want, you can also control the range of IP addresses by utilizing the given command structure:
$ sudo iptables -A INPUT -m range --src-range 192.168.0.1-192.168.0.255 -j REJECT
Delete User Defined Rule
Sometimes we may end up making mistakes while creating rules and the best way to overcome those mistakes is to delete them. Deleting defined rules are the easiest process throughout this guide and to delete them, first, we will have to list them.
To list defined rules with numbers, use the given command:
$ sudo iptables -L --line-numbers
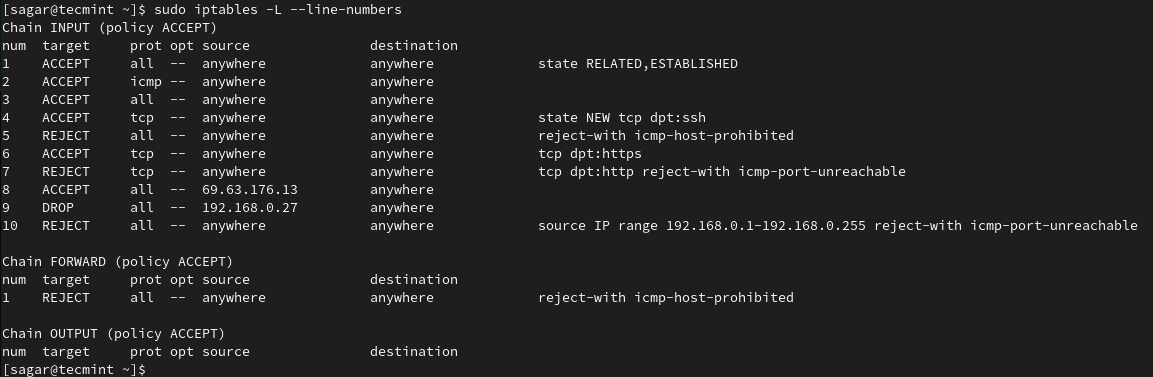
To delete rules, we will have to follow the given command structure:
$ sudo iptables -D <INPUT/FORWARD/OUTPUT> <Number>
Let’s suppose I want to delete the 10th rule from INPUT so I will be using the given command:
$ sudo iptables -D INPUT 10
To cross-check whether we have successfully removed rule, we have to list rules by given command:
$ sudo iptables -L –line-numbers
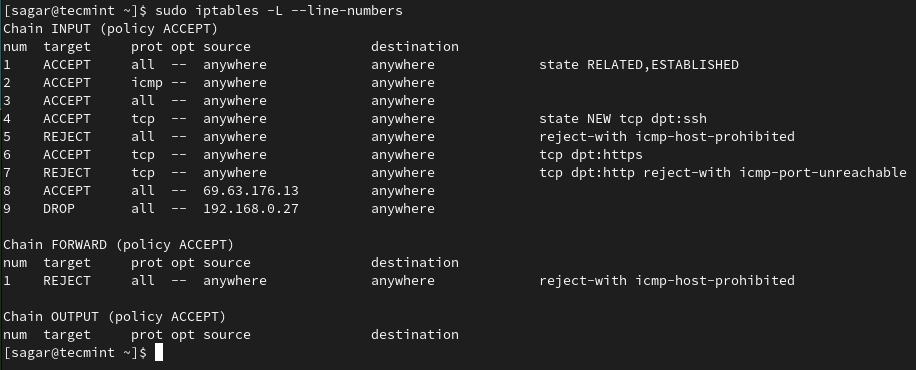
As you can see, we have successfully removed the 10th rule.
Save Defined IPTables Rules
You might be wondering why we have to save rules where they are working fine after applying them? The issue is once your system reboots, all the defined rules which are not saved will be deleted so it is crucial for us to them.
To save rules in RHEL-based distros:
$ sudo /sbin/service iptables save
To save rules in Debian derivatives:
$ sudo /sbin/iptables–save
To learn more about IPtable Firewall rules, check out our detailed guide at:
Throughout this guide, we have tried to make things simple so everyone can benefit from it. This was a basic explanation guide on IPTables and if you have any queries, feel free to ask in the comments.


How can I prevent any modification by Iptable on the site files if the site is built on Java or HTML5
A firewall is a system security framework, that controls the incoming and outgoing system traffic. It is very stable, protect our system from malware, system performance speed high.
Please some know how block HTTPS and HTTP sites with iptables please send my email id [email protected]
please support me
gts
hi,
i have rhce exam within one week .
pls, guide me…..
Hi there,
Subject: check the file integrity (File integrity monitoring for Linux servers)
I am aware of tools and packages that can do this job for me. But i am more keen on having a cron job and shell script to do that for me and alert me if Intrusion Detected.
my Linux version is RHEL5.9
Can you help please?
Thanks in advance for your help.
Hany
Also please include… tips for cracking 333 exam or LDAP or clustering n new stuff thanks a ton! … sent a broadcast mail to all my past frens and office colleagues luv u tecmint….