In the last article (RHCSA series Part 6) we started explaining how to set up and configure local system storage using parted and ssm.

We also discussed how to create and mount encrypted volumes with a password during system boot. In addition, we warned you to avoid performing critical storage management operations on mounted filesystems. With that in mind we will now review the most used file system formats in Red Hat Enterprise Linux 7 and then proceed to cover the topics of mounting, using, and unmounting both manually and automatically network filesystems (CIFS and NFS), along with the implementation of access control lists for your system.
Prerequisites
Before proceeding further, please make sure you have a Samba server and a NFS server available (note that NFSv2 is no longer supported in RHEL 7).
During this guide we will use a machine with IP 192.168.0.10 with both services running in it as server, and a RHEL 7 box as client with IP address 192.168.0.18. Later in the article we will tell you which packages you need to install on the client.
File System Formats in RHEL 7
Beginning with RHEL 7, XFS has been introduced as the default file system for all architectures due to its high performance and scalability. It currently supports a maximum filesystem size of 500 TB as per the latest tests performed by Red Hat and its partners for mainstream hardware.
Also, XFS enables user_xattr (extended user attributes) and acl (POSIX access control lists) as default mount options, unlike ext3 or ext4 (ext2 is considered deprecated as of RHEL 7), which means that you don’t need to specify those options explicitly either on the command line or in /etc/fstab when mounting a XFS filesystem (if you want to disable such options in this last case, you have to explicitly use no_acl and no_user_xattr).
Keep in mind that the extended user attributes can be assigned to files and directories for storing arbitrary additional information such as the mime type, character set or encoding of a file, whereas the access permissions for user attributes are defined by the regular file permission bits.
Access Control Lists
As every system administrator, either beginner or expert, is well acquainted with regular access permissions on files and directories, which specify certain privileges (read, write, and execute) for the owner, the group, and “the world” (all others). However, feel free to refer to Part 3 of the RHCSA series if you need to refresh your memory a little bit.
However, since the standard ugo/rwx set does not allow to configure different permissions for different users, ACLs were introduced in order to define more detailed access rights for files and directories than those specified by regular permissions.
In fact, ACL-defined permissions are a superset of the permissions specified by the file permission bits. Let’s see how all of this translates is applied in the real world.
1. There are two types of ACLs: access ACLs, which can be applied to either a specific file or a directory), and default ACLs, which can only be applied to a directory. If files contained therein do not have a ACL set, they inherit the default ACL of their parent directory.
2. To begin, ACLs can be configured per user, per group, or per an user not in the owning group of a file.
3. ACLs are set (and removed) using setfacl, with either the -m or -x options, respectively.
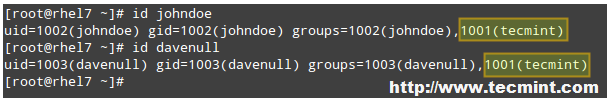
For example, let us create a group named tecmint and add users johndoe and davenull to it:
# groupadd tecmint # useradd johndoe # useradd davenull # usermod -a -G tecmint johndoe # usermod -a -G tecmint davenull
And let’s verify that both users belong to supplementary group tecmint:
# id johndoe # id davenull
Let’s now create a directory called playground within /mnt, and a file named testfile.txt inside. We will set the group owner to tecmint and change its default ugo/rwx permissions to 770 (read, write, and execute permissions granted to both the owner and the group owner of the file):
# mkdir /mnt/playground # touch /mnt/playground/testfile.txt # chmod 770 /mnt/playground/testfile.txt
Then switch user to johndoe and davenull, in that order, and write to the file:
echo "My name is John Doe" > /mnt/playground/testfile.txt echo "My name is Dave Null" >> /mnt/playground/testfile.txt
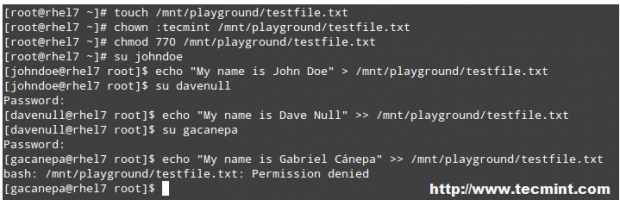
So far so good. Now let’s have user gacanepa write to the file – and the write operation will fail, which was to be expected.
But what if we actually need user gacanepa (who is not a member of group tecmint) to have write permissions on /mnt/playground/testfile.txt? The first thing that may come to your mind is adding that user account to group tecmint. But that will give him write permissions on ALL files were the write bit is set for the group, and we don’t want that. We only want him to be able to write to /mnt/playground/testfile.txt.
# touch /mnt/playground/testfile.txt # chown :tecmint /mnt/playground/testfile.txt # chmod 777 /mnt/playground/testfile.txt # su johndoe $ echo "My name is John Doe" > /mnt/playground/testfile.txt $ su davenull $ echo "My name is Dave Null" >> /mnt/playground/testfile.txt $ su gacanepa $ echo "My name is Gabriel Canepa" >> /mnt/playground/testfile.txt
Let’s give user gacanepa read and write access to /mnt/playground/testfile.txt.
Run as root,
# setfacl -R -m u:gacanepa:rwx /mnt/playground
and you’ll have successfully added an ACL that allows gacanepa to write to the test file. Then switch to user gacanepa and try to write to the file again:
$ echo "My name is Gabriel Canepa" >> /mnt/playground/testfile.txt
To view the ACLs for a specific file or directory, use getfacl:
# getfacl /mnt/playground/testfile.txt

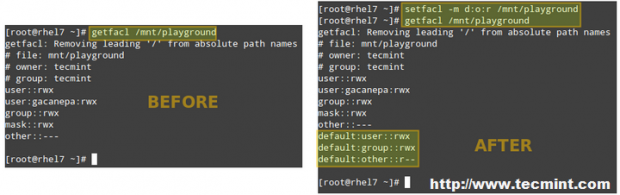
To set a default ACL to a directory (which its contents will inherit unless overwritten otherwise), add d: before the rule and specify a directory instead of a file name:
# setfacl -m d:o:r /mnt/playground
The ACL above will allow users not in the owner group to have read access to the future contents of the /mnt/playground directory. Note the difference in the output of getfacl /mnt/playground before and after the change:
Chapter 20 in the official RHEL 7 Storage Administration Guide provides more ACL examples, and I highly recommend you take a look at it and have it handy as reference.







And I am wondering why this has covered before editing /etc/exports & smb.conf. RHCE certification is not only for experienced people, many freshers do it as well. I need to recommend the series for newbies, please get it corrected.
@Neeraj,
The answer is simple. The RHCSA objective related to this article reads as follows: “Mount and unmount CIFS and NFS network file systems”. It does NOT require a candidate to SET UP a CIFS or NFS share. That objective is covered as part of the RHCE exam.
I was referring to:
Prerequisites
Before proceeding further, please make sure you have a Samba server and a NFS server available (note that NFSv2 is no longer supported in RHEL 7).
@Neeraj,
I see your point – but that’s the way it is. Maybe you should contact RH directly and ask for their feedback on the ordering on contents.
Anyway, I’ll tell you my experience with the Linux Foundation certifications. With the LFCS exam, one of the required competencies is that you know how to mount a NFS share. You are NOT required to know how to SET it up – just mount it.
I understand then, even LDAP authentication from the client side needs to be done in RHCE though I don’t know the configuration of Linux DC. Hopefully, would be done today or tomorrow.
Waiting for my 4 more training and certifications to be completed. Once I would be a certified architect then will contact them again. I didn’t get satisfactory answers in the past at one go, even when my tickets were escalated to the top most level.
Small mistake, in set permission for gacanepa user you probably committed.
I think should be full path to file testfile.txt not only directory.
PS.
Thanks for that another article.