For SSH to work well, it requires correct permissions on the ~/.ssh or /home/username/.ssh directory: the default location for all user-specific ssh configuration and authentication files. The recommended permissions are read/write/execute for the user, and must not be accessible by group and others.
Besides, ssh also requires that the files within the directory should have read/write permissions for the user, and not be accessible by others. Otherwise, a user might encounter the following error:
Authentication refused: bad ownership or modes for directory
This guide explains how to set correct permissions on the .ssh directory and the files stored in it, on Linux systems.
Set Correct SSH Directory Permissions in Linux
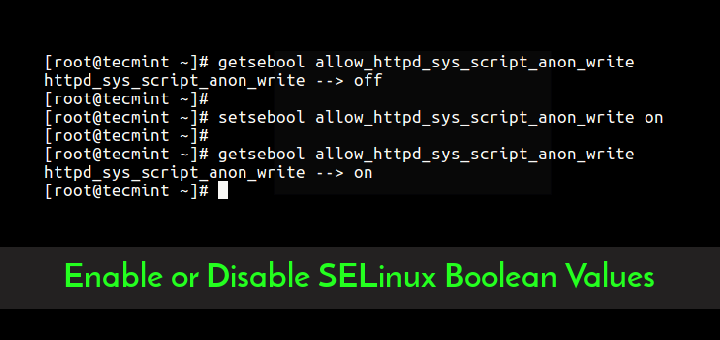
If you ever encounter the above error, you can set correct ssh directory permissions on the .ssh directory using the chmod command.
# chmod u+rwx,go-rwx ~/.ssh OR # chmod 0700 ~/.ssh
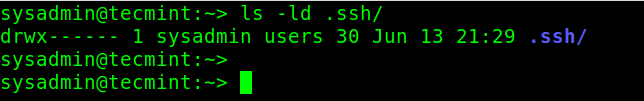
To check the permissions on the ~/.ssh directory, use the ls command with the -l and -d flags, like so:
# ls -ld .ssh/
The following are some of the files you will find in the ~/.ssh directory:
- private key file (e.g id_rsa) – the private key for authentication, which contains highly sensitive information, therefore, it must have read and write permissions for the owner and not be accessible by group and others, otherwise, ssh will refuse to connect.
- public key (e.g .pub file) – the public key for authentication, which also contains sensitive information therefore it should have read and write permissions for the owner, read-only permission by group, and others.
- authorized_keys – contains the list of the public keys that can be used for logging in as this user. It is not highly sensitive but should have read and write permissions for the owner and not be accessible by group and others.
- known_hosts – stores a list of host keys for all hosts the ssh user has logged into. It should have read and write permissions for the owner and not be accessible by groups and others.
- config – a per-user configuration file and should have read and write permissions for the owner and should not be accessible by group and others.
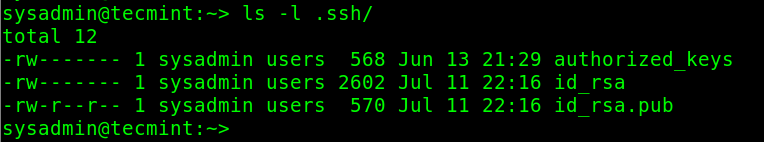
By default, the files under the ~/.ssh directory are created with the correct permissions set. To check their permissions, run the following command within your home directory:
# ls -l .ssh/
If ssh complains of wrong permissions on any of the above files, you can set the correct permissions for any of the files like this:
# chmod u+rw,go-rwx .ssh/id_rsa # chmod u+rw,go-rwx .ssh/id_rsa.pub # chmod u+rw,go-rwx .ssh/authorized_keys # chmod u+rw,go-rwx .ssh/known_hosts # chmod u+rw,go-rwx .ssh/config OR # chmod 600 .ssh/id_rsa # chmod 600 .ssh/id_rsa.pub # chmod 600 .ssh/authorized_keys # chmod 600 .ssh/known_hosts # chmod 600 .ssh/config
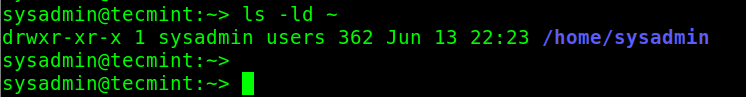
In addition, a user’s home directory should not be writeable by the group or others, as shown in the following screenshot.
# ls -ld ~
To remove write permissions for group and others on the home directory, run this command:
# chmod go-w ~ OR # chmod 755 ~
You might also like to read the following SSH-related articles:
- How to Secure and Harden OpenSSH Server
- 5 Best OpenSSH Server Best Security Practices
- How to Setup SSH Passwordless Login in Linux [3 Easy Steps]
- How to Block SSH Brute Force Attacks Using SSHGUARD
- How to Use Port Knocking To Secure SSH Service in Linux
- How to Change SSH Port in Linux
That’s it for now! Use the comment section below to ask questions or add your thoughts to this topic.





If permissions are right and you’re still getting errors, make sure the private key files end with a new line.