At any given time when using your PC which is connected to a router, you will be part of a network. Whether you are in an office environment or simply working from home, your computer will be in a network.
What is a Computer Network?
A computer network is defined as a group of 2 or more computers that are connected and can electronically communicate with each other. The computers are identified using their hostnames, IP, and mac addresses.
A simple home or office network is referred to as a LAN, short for Local Area Network. A LAN covers a small area such as a home, office, or restaurant network. In contrast, a WAN (Wide Area Network) spans a large geographical region. WAN is mostly used to connect various sites such as office buildings in different locations.
This article is Part 4 of the LFCA series, here in this part, you will acquaint yourself with general networking commands and how beneficial they can be in troubleshooting connectivity issues.
1. hostname Command
The hostname command displays the hostname of a Linux system. This is usually set or configured during the installation. To check the hostname, run the command:
$ hostname tecmint
2. ping Command
Short for packet internet groper, the ping command is used to check connectivity between 2 systems or servers. It sends out an ICMP echo request to a remote host and waits for a reply. If the host is up, the echo request bounces off the remote host and is sent back to the source informing the user that the host is up or available.
The ping command takes the syntax shown.
$ ping options IP address
For example to ping a host in my local area network with the IP of 192.168.2.103, I will run the command:
$ ping 192.168.2.103 PING 192.168.0.123 (192.168.0.123) 56(84) bytes of data. 64 bytes from 192.168.2.103: icmp_seq=1 ttl=64 time=0.043 ms 64 bytes from 192.168.2.103: icmp_seq=2 ttl=64 time=0.063 ms 64 bytes from 192.168.2.103: icmp_seq=3 ttl=64 time=0.063 ms 64 bytes from 192.168.2.103: icmp_seq=4 ttl=64 time=0.061 ms 64 bytes from 192.168.2.103: icmp_seq=5 ttl=64 time=0.062 ms
The ping command continues sending the ICMP ping packet until you interrupt it by pressing Ctrl + C on the keyboard. However, you can limit the packets sent using the -c option.
In the example below, we are sending 5 echo request packets, and once done, the ping command stops.
$ ping 192.168.2.103 -c 5 PING 192.168.0.123 (192.168.0.123) 56(84) bytes of data. 64 bytes from 192.168.2.103: icmp_seq=1 ttl=64 time=0.044 ms 64 bytes from 192.168.2.103: icmp_seq=2 ttl=64 time=0.052 ms 64 bytes from 192.168.2.103: icmp_seq=3 ttl=64 time=0.066 ms 64 bytes from 192.168.2.103: icmp_seq=4 ttl=64 time=0.056 ms 64 bytes from 192.168.2.103: icmp_seq=5 ttl=64 time=0.066 ms --- 192.168.2.103 ping statistics --- 5 packets transmitted, 5 received, 0% packet loss, time 4088ms rtt min/avg/max/mdev = 0.044/0.056/0.066/0.008 ms
In addition, you can also ping the domain name of a host or server. For example, you can ping Google as shown.
$ ping google.com PING google.com (142.250.183.78) 56(84) bytes of data. 64 bytes from bom12s12-in-f14.1e100.net (142.250.183.78): icmp_seq=1 ttl=117 time=2.86 ms 64 bytes from bom12s12-in-f14.1e100.net (142.250.183.78): icmp_seq=2 ttl=117 time=3.35 ms 64 bytes from bom12s12-in-f14.1e100.net (142.250.183.78): icmp_seq=3 ttl=117 time=2.70 ms 64 bytes from bom12s12-in-f14.1e100.net (142.250.183.78): icmp_seq=4 ttl=117 time=3.12 ms ...
Also, you can ping the DNS. For example, you can ping Google’s address which is 8.8.8.8.
$ ping 8.8.8.8 -c 5 PING 8.8.8.8 (8.8.8.8) 56(84) bytes of data. 64 bytes from 8.8.8.8: icmp_seq=1 ttl=118 time=3.24 ms 64 bytes from 8.8.8.8: icmp_seq=2 ttl=118 time=3.32 ms 64 bytes from 8.8.8.8: icmp_seq=3 ttl=118 time=3.40 ms 64 bytes from 8.8.8.8: icmp_seq=4 ttl=118 time=3.30 ms 64 bytes from 8.8.8.8: icmp_seq=5 ttl=118 time=2.92 ms --- 8.8.8.8 ping statistics --- 5 packets transmitted, 5 received, 0% packet loss, time 4005ms rtt min/avg/max/mdev = 2.924/3.237/3.401/0.164 ms
A failed ping test is pointed to one of the following:
- A host that is offline.
- General network failure.
- Presence of a firewall that is blocking ICMP requests.
3. traceroute Command
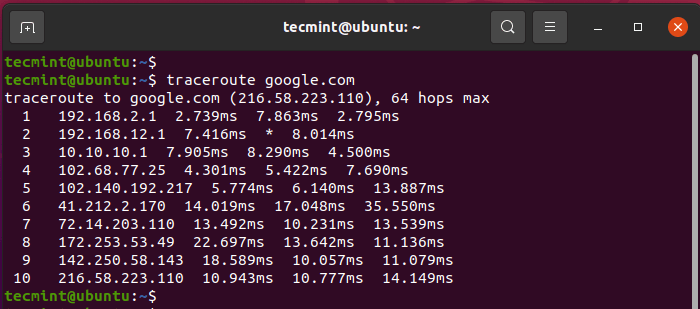
The traceroute command displays the route that an ICMP ping packet takes from your device to the destination host or server. It displays the IP addresses of devices that the packet hops through before getting to the remote destination.
In line 2 the output shows an asterisk sign * in the round trip. This is an indicator that the packet was dropped and no response was received. This shows that the ping packet was dropped by the router, and this could be for a variety of reasons such as network congestion.
Traceroute command is a cool diagnostic command that you can use to troubleshoot the network where the ping command gives you failed results. It shows the device at which the packets are being dropped.
$ traceroute google.com
4. mtr Command
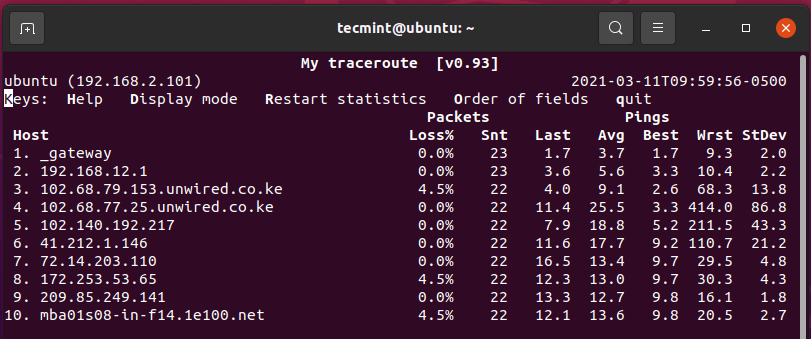
The mtr (my traceoute) command combines the functionalities of the ping and traceroute command. It displays a host of statistics including the host that each packet travels through, and response times for all the network hops.
$ mtr google.com
5. ifconfig Command
The ifconfig command lists the network interfaces attached to the PC along with other statistics such as the IP addresses associated with each interface, subnet mask, and MTU to mention just a few.
$ ifconfig
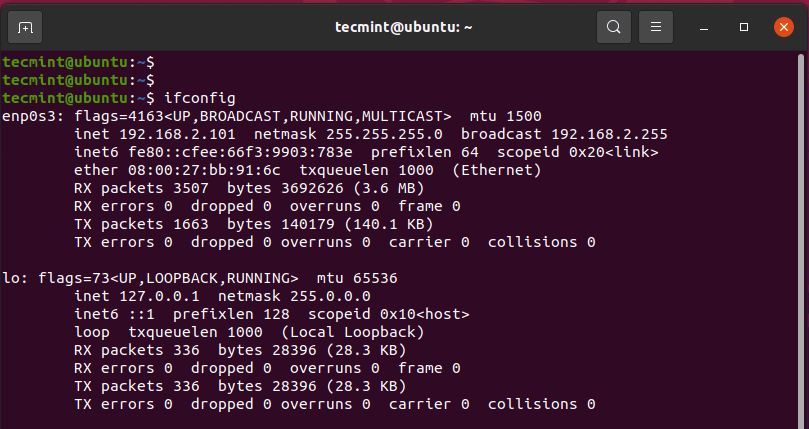
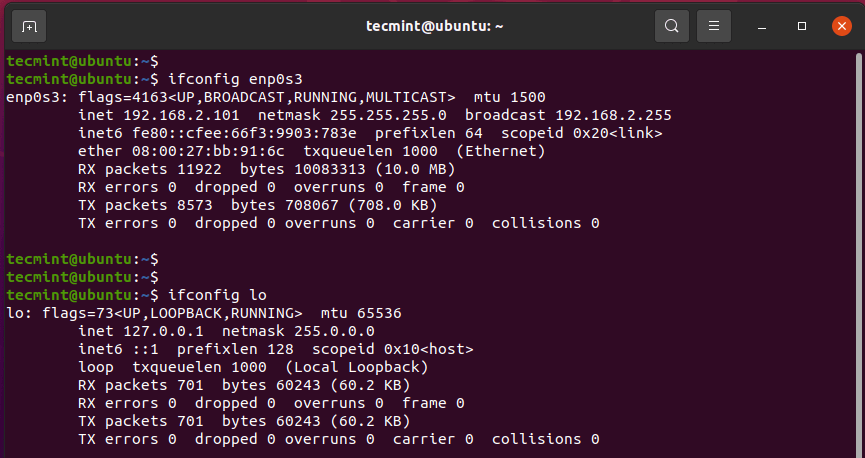
The inet parameter shows the IPv4 address of the network interface while inet6 points to the IPv6 address. You can view the details of a single interface by specifying the interface as shown:
$ ifconfig enp0s3
6. IP Command
Another way you can view interface statistics is using the ip address command as shown.
$ ip address
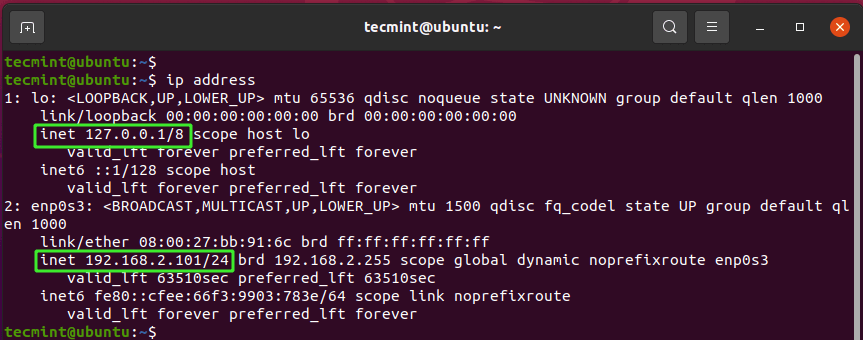
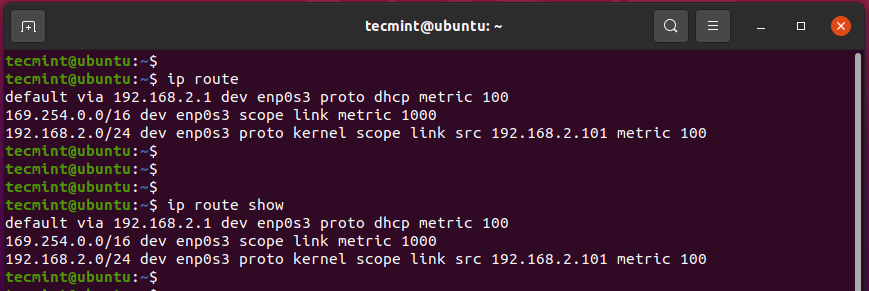
7. ip route Command
The ip route command prints out the routing table of your PC.
$ ip route OR $ ip route show
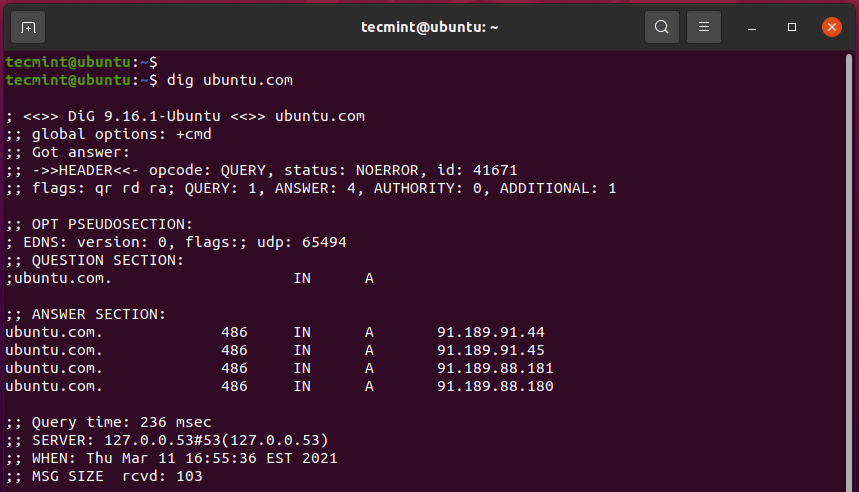
8. dig Command
The dig utility ( short for Domain Information Groper ) is a command-line tool for probing DNS nameservers. It takes a domain name as the argument and displays information such as the host address, A record, MX (mail exchanges) record, nameservers, etc.
In a nutshell, the dig command is a DNS lookup utility and is mostly used by system administrators for DNS troubleshooting.
$ dig ubuntu.com
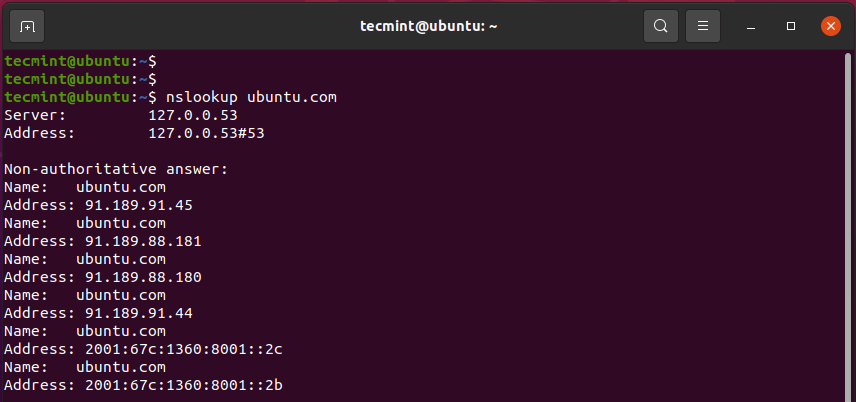
9. nslookup Command
The nslookup utility is yet another command-line tool that is used for making DNS lookups in a bid to retrieve domain names and A records.
$ nslookup ubuntu.com
10. netstat Command
The netstat command prints out the network interface statistics. It can display the routing table, ports that various services are listening on, TCP and UDP connections, PID, and UID.
To display network interfaces attached to your PC, execute:
$ netstat -i Kernel Interface table Iface MTU RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg enp1s0 1500 0 0 0 0 0 0 0 0 BMU lo 65536 4583 0 0 0 4583 0 0 0 LRU wlp2s0 1500 179907 0 0 0 137273 0 0 0 BMRU
To check out the routing table, use the -r option as shown.
$ netstat -r Kernel IP routing table Destination Gateway Genmask Flags MSS Window irtt Iface default _gateway 0.0.0.0 UG 0 0 0 wlp2s0 link-local 0.0.0.0 255.255.0.0 U 0 0 0 wlp2s0 192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 wlp2s0
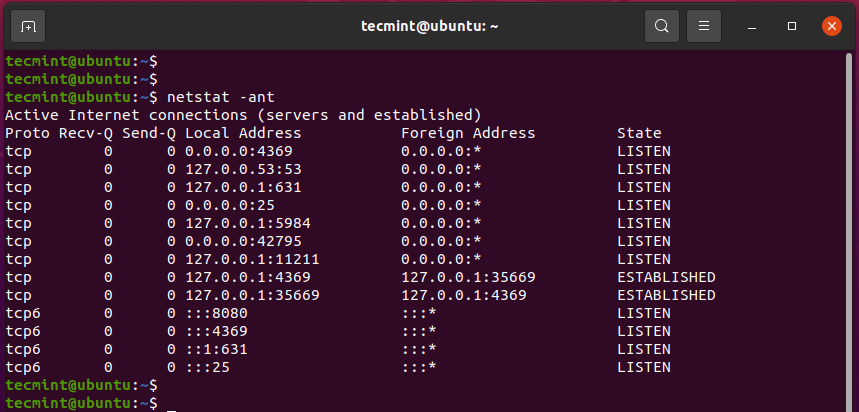
To examine active TCP connections invoke the command:
$ netstat -ant
11. ss Command
The ss command is a network tool which is used to dump socket statistics and shows system network metrics in similar fashion to netstat command. The ss command is faster than netstat and displays more information about TCP and network statistics than netstat.
$ ss #list al connections $ ss -l #display listening sockets $ ss -t #display all TCP connection
Summary
That was an overview of basic networking commands that will prove useful especially when troubleshooting minor network issues in your home or office environment. Give them a try from time to time to sharpen your network troubleshooting skills.








`netstat` has newer replacement `ss`- It is worth adding it too
@Levgen,
Added ss command to the article as suggested by you…