SSH is the most secure means of connecting to Linux servers remotely. And one of the common errors encountered while using SSH is the “ssh: connect to host port 22: No route to host”. In this short article, we will show how to troubleshoot and fix this error.
Here is a screenshot of the error we are talking about. Note that the port may not necessarily be port 22, depending on your configurations on the remote host. As a security measure, system administrators can configure SSH to be accessed via a different port.
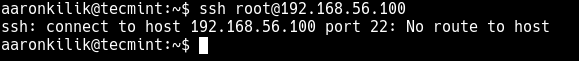
There are different reasons why this error appears. The first is normally that the remote server could be down, so you need to check whether it is up and running using the ping command.
# ping 192.168.56.100
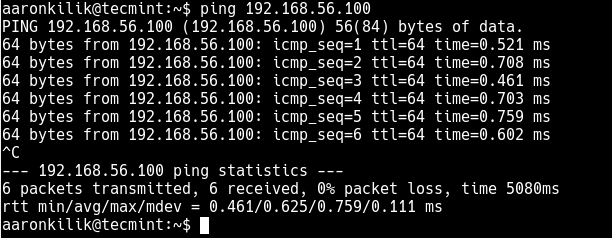
From the ping command results, the server is up and running, that’s why it is accepting the pings. In this case, the reason for the error is something else.
If you have a firewall service running on your remote server, it is possible that the firewall is blocking access via port 22.
Therefore you need to access the server console physically or if it is a VPS, you can use any other means such as VNC (that’s if it is already setup) or other custom remote server access applications provided by your VPS service provider. Login, and access a command prompt.
Then use the firewall-cmd (RHEL/CentOS/Fedora) or UFW (Debian/Ubuntu) to open port 22 (or the port you configured to be used for SSH) in the firewall as follows.
# firewall-cmd --permanent --add-port=22/tcp # firewall-cmd --reload OR $ sudo ufw allow 22/tcp $ sudo ufw reload
Now try to re-connect to the remote server once more via SSH.
$ ssh [email protected]
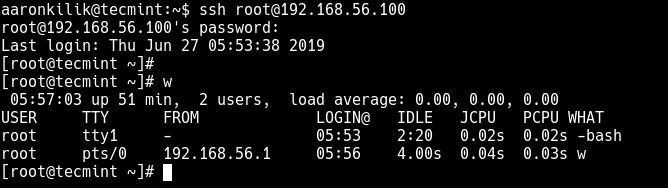
That’s it for now! You will also find the following SSH guides useful:
- How to Change SSH Port in Linux
- How to Create SSH Tunneling or Port Forwarding in Linux
- How to Disable SSH Root Login in Linux
- 4 Ways to Speed Up SSH Connections in Linux
- How to Find All Failed SSH login Attempts in Linux
Remember, you can share your thoughts with us or ask any questions concerning this topic via the comment form below.



Thank you. You are a live saver.
I was busy checking for iptables and ufw on the problematic server that had many hands managing it, having forgotten about firewalld. Your tutorial pointed me in the right direction.
Thank you so much, it worked for me on CentOS.
If the server is not pinging means what else I can do. Did I set my ip dynamic/automatic?
First things first – Thank you very much for publishing the various articles on Linux. I use them as a quick reference when needed.
I have noticed typo’s in several articles I have used recently. I used the setup vsftpd, vsftpd with a certificate, and samba articles. Each of them had a minor typo such as a missing
"/"on the path or an omitted letter such as a missing “f” in conf (con vice conf). These were very minor discrepancies. Overall, I was very pleased with the results as the outcome was spot-on after fixing the minor errors.Thank You, again!