ShellCheck is a static analysis tool that shows warnings and suggestions concerning bad code in bash/sh shell scripts. It can be used in several ways: from the web by pasting your shell script in an online editor (Ace – a standalone code editor written in JavaScript) in https://www.shellcheck.net (it is always synchronized to the latest git commit, and is the simplest way to give ShellCheck a go) for instant feedback.
Alternatively, you can install it on your machine and run it from the terminal, integrate it with your text editor as well as in your build or test suites.
There are three things ShellCheck does primarily:
- It points out and explains typical beginner’s syntax issues that cause a shell to give cryptic error messages.
- It points out and explains typical intermediate level semantic problems that cause a shell to behave strangely and counter-intuitively.
- It also points out subtle caveats, corner cases and pitfalls that may cause an advanced user’s otherwise working script to fail under future circumstances.
In this article, we will show how to install and use ShellCheck in the various ways to find bugs or bad code in your shell scripts in Linux.
How to Install and Use ShellCheck in Linux
ShellCheck can be easily installed locally through your package manager as shown.
On Debian/Ubuntu
# apt-get install shellcheck
On RHEL/CentOS
# yum -y install epel-release # yum install ShellCheck
On Fedora
# dnf install ShellCheck
Once ShellCheck installed, let’s take a look at how to use ShellCheck in the various methods we mentioned before.
Using ShellCheck From the Web
Go to https://www.shellcheck.net and paste your script in the Ace editor provided, you will view the output at the bottom of the editor as shown in the screen shot below.
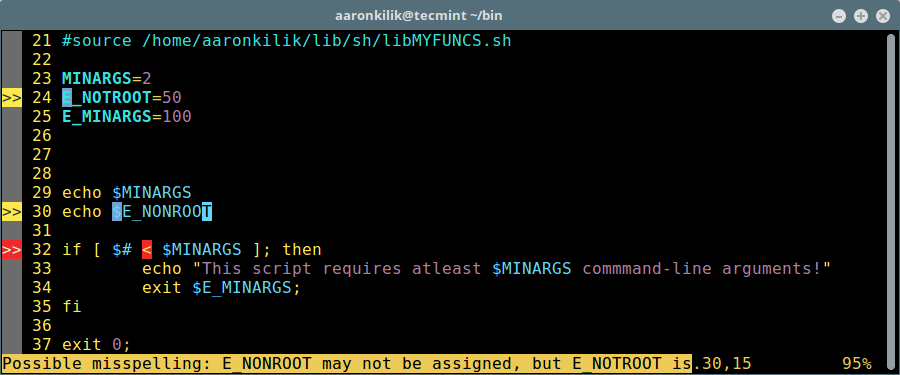
In the following example, the test shell script consists of the following lines:
#!/bin/bash #declare variables MINARGS=2 E_NOTROOT=50 E_MINARGS=100 #echo values of variables echo $MINARGS echo $E_NONROOT exit 0;
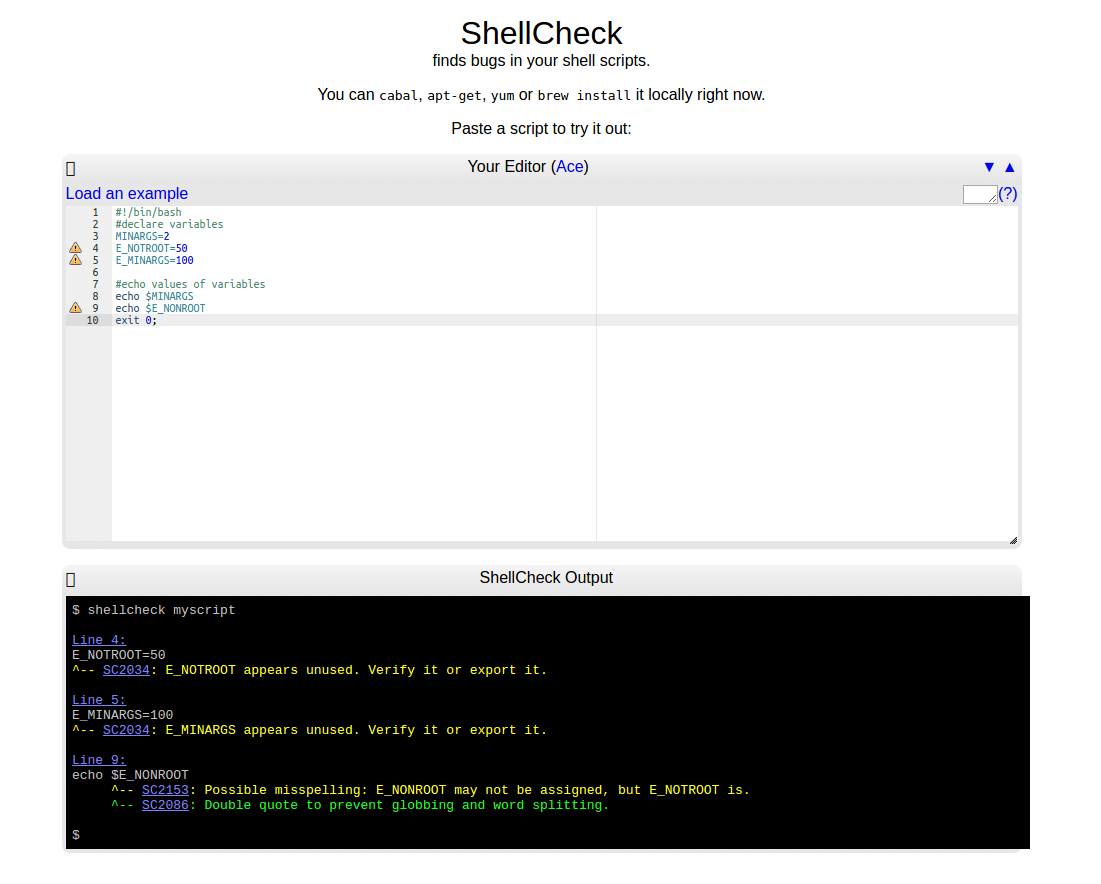
From the screenshot above, the first two variables E_NOTROOT and E_MINARGS have been declared but are unused, ShellCheck reports these as “suggestive errors”:
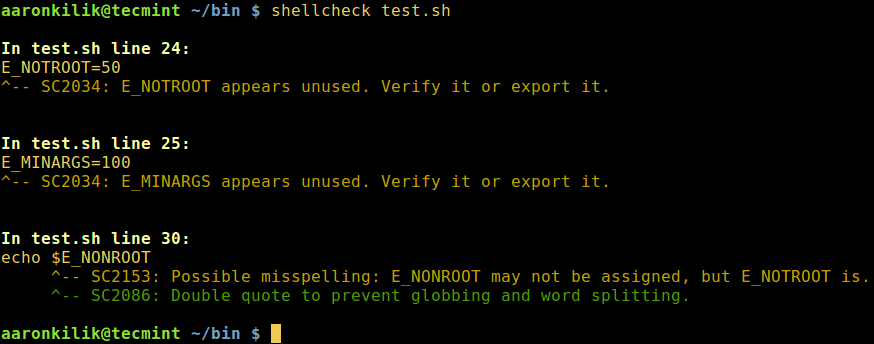
SC2034: E_NOTROOT appears unused. Verify it or export it. SC2034: E_MINARGS appears unused. Verify it or export it.
Then secondly, the wrong name (in the statement echo $E_NONROOT) was used to echo variable E_NOTROOT, that is why ShellCheck shows the error:
SC2153: Possible misspelling: E_NONROOT may not be assigned, but E_NOTROOT is
Again when you look at the echo commands, the variables have not been double quoted (helps to prevent globbing and word splitting), therefore Shell Check shows the warning:
SC2086: Double quote to prevent globbing and word splitting.
Using ShellCheck From the Terminal
You can also run ShellCheck from the command-line, we’ll use the same shell script above as follows:
$ shellcheck test.sh
Using ShellCheck From the Text Editor
You can also view ShellCheck suggestions and warnings directly in a variety of editors, this is probably a more efficient way of using ShellCheck, once you save a files, it shows you any errors in the code.
In Vim, use ALE or Syntastic (we will use this):
Start by installing Pathogen so that it’s easy to install syntastic. Run the commands below to get the pathogen.vim file and the directories it needs:
# mkdir -p ~/.vim/autoload ~/.vim/bundle && curl -LSso ~/.vim/autoload/pathogen.vim https://tpo.pe/pathogen.vim
Then add this to your ~/.vimrc file:
execute pathogen#infect()
Once you have installed pathogen, and you now can put syntastic into ~/.vim/bundle as follows:
# cd ~/.vim/bundle && git clone --depth=1 https://github.com/vim-syntastic/syntastic.git
Next, close vim and start it back up to reload it, then type the command below:
:Helptags
If all goes well, you should have ShellCheck integrated with Vim, the following screenshots show how it works using the same script above.
In case you get an error after following the steps above, then you possibly didn’t install Pathogen correctly. Redo the steps but this ensure that you did the following:
- Created both the ~/.vim/autoload and ~/.vim/bundle directories.
- Added the execute pathogen#infect() line to your ~/.vimrc file.
- Did the git clone of syntastic inside ~/.vim/bundle.
- Use appropriate permissions to access all of the above directories.
You can also use other editors to check bad code in shell scripts like:
- In Emacs, use Flycheck.
- In Sublime, employ SublimeLinter.
- In Atom, make use of Linter.
- In most other editors, use GCC error compatibility.
Note: Use the gallery of bad code to carry out more ShellChecking.
ShellCheck Github Repository: https://github.com/koalaman/shellcheck
That’s it! In this article, we showed how to install and use ShellCheck to finds bugs or bad code in your shell scripts in Linux. Share your thoughts with us via the comment section below.
Do you know of any other similar tools out there? If yes, then share info about them in the comments as well.