pam_tally2 module is used to lock user accounts after certain number of failed ssh login attempts made to the system. This module keeps the count of attempted accesses and too many failed attempts.
pam_tally2 module comes in two parts, one is pam_tally2.so and another is pam_tally2. It is based on PAM module and can be used to examine and manipulate the counter file. It can display user login attempts counts, set counts on individual basis, unlock all user counts.
The pam_faillock module replaces the pam_tally and pam_tally2 modules which have been deprecated in RHEL 7 and RHEL 8. It offers more flexibility and options than the two modules.
By default, pam_tally2 module is already installed on the most of the Linux distributions and it is controlled by PAM package itself. This article demonstrates on how to lock and unlock SSH accounts after reaching a certain failed number of login attempts.
How to Lock and Unlock User Accounts
Use ‘/etc/pam.d/password-auth‘ configuration file to configure login attempts accesses. Open this file and add the following AUTH configuration line to it at beginning of the ‘auth‘ section.
auth required pam_tally2.so file=/var/log/tallylog deny=3 even_deny_root unlock_time=1200
Next, add the following line to ‘account‘ section.
account required pam_tally2.so
Parameters
- file=/var/log/tallylog – Default log file is used to keep login counts.
- deny=3 – Deny access after 3 attempts and lock down user.
- even_deny_root – Policy is also apply to root user.
- unlock_time=1200 – Account will be locked till 20 Min. (remove this parameters if you want to lock down permanently till manually unlock.)
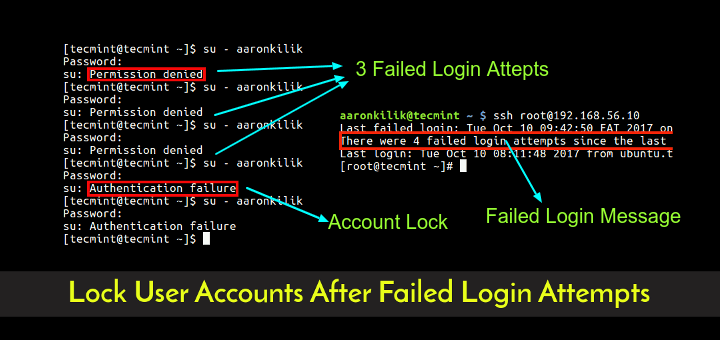
Once you’ve done with above configuration, now try to attempt 3 failed login attempts to server using any ‘username‘. After you made more than 3 attempts you will get the following message.
[root@tecmint ~]# ssh [email protected] [email protected]'s password: Permission denied, please try again. [email protected]'s password: Permission denied, please try again. [email protected]'s password: Account locked due to 4 failed logins Account locked due to 5 failed logins Last login: Mon Apr 22 21:21:06 2013 from 172.16.16.52
Now, verify or check the counter that user attempts with the following command.
[root@tecmint ~]# pam_tally2 --user=tecmint Login Failures Latest failure From tecmint 5 04/22/13 21:22:37 172.16.16.52
How to reset or unlock the user account to enable access again.
[root@tecmint pam.d]# pam_tally2 --user=tecmint --reset Login Failures Latest failure From tecmint 5 04/22/13 17:10:42 172.16.16.52
Verify login attempt is reset or unlocked
[root@tecmint pam.d]# pam_tally2 --user=tecmint Login Failures Latest failure From tecmint 0
The PAM module is part of all Linux distribution and configuration provided about should work on all Linux distribution. Do ‘man pam_tally2‘ from the command line to know more about it.
Read Also:



I have a requirement that I need to add 2 new users in a Rhel 7.x. On the first 60 days only they need Sudo/privileged access and after the standard user Access is enough. How to fulfill the same.
This worked like a charm to unlock a locked account due to excessive failed logons!
However in a RHEL 5.11 server pam_tally2 seems not working well as pam_tally does, which means I have to use pam_tally to unlock such an account.
This save me yesterday in a critical situation :)
Hey,
I dont have password-auth file in the box. Can I update system-auth?
@Garima,
How come that possible, every Linux distro must have password-auth file, may I know which Linux distributions you’re using? or else please check /etc/pam.d/ directory exits on the server with all PAM configuration files?
Hey,
I have system-auth file instead if password-auth. But the commands mentioned above are not working.
Any pointers to that. I am using RHEL 5.4.
Hi,
Any idea why the changes are not seen when I have updated the file.
@Garima,
Sorry no idea about system-auth file as you’re using older version of RHEL, I never worked on RHEL 5, so better you should follow this guide, might be helpful to you..
https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/5/html/Deployment_Guide/Configuration_Options-PAM_Configuration_Options.html
I thought I was going crazy! My password was not locked in /etc/shadow and I was sure I was entering the right password. Thanks!
Thanks, it works for me
Thanks, it works in 6.5.
I appreciate the information! It really helped with configuring the account lock. I’m curious on how you were able to configure the lockout message, however.
Account locked due to 4 failed logins
Unlike the above, I’m getting the standard “Access Denied” error.
very nice…
It helps my team a lot….
on our setup on RHEL6.4, though the account gets locked, however the message is not informative. It is just showing the error message “access denied”
I have the same problem. It will lock the account successfully, however it will not provide information on this to the user. Were you able to figure out how to set the access denied error to something more like:
Account locked due to 4 failed logins
thanks :) it worked ..
On RHEL 6.4 it is counting failes, but never locks.
I haven’t tried out in 6.4, will try and update you.
On my setup it works on RHEL 6.4. The count of failed log attemps is done OK, it resets itselfs if the user success before account lockdown, and the account locks itself if fail count reaches max deny count.
The only thing I can’t manage to do from now, is to have the reason of login deny printed (like it is shown in the article)
Can you post your setup? I have basically copy pasted what is written in the article and everything works as described accept locking the account.
Let me check again, why the locking not working on accounts. Will update the article.
Can you say “denial of service”. I am sure you can. Can you say automated denial of service meaning that the unlock provison is completely useless I am sure you can too.
If you are worried about brute force password cracking the way to go is
1) Long, hard to guess password
2) Setting alerts about failed logins and ensuring they are not lost in “noise”
3) Port knocking