LDAP (short for Lightweight Directory Access Protocol) is an industry standard, widely used set of protocols for accessing directory services.
A directory service in simple terms is a centralized, network-based database optimized for read access. It stores and provides access to information that must either be shared between applications or is highly distributed.
Directory services play an important role in developing intranet and Internet applications by helping you share information about users, systems, networks, applications, and services throughout the network.
A typical use case for LDAP is to offer a centralized storage of usernames and passwords. This allows various applications (or services) to connect to the LDAP server to validate users.
After setting up a working LDAP server, you will need to install libraries on the client for connecting to it. In this article, we will show how to configure an LDAP client to connect to an external authentication source.
I hope you already having a working LDAP server environment, if not setup Up LDAP Server for LDAP-based Authentication.
How to Install and Configure LDAP Client in Ubuntu and CentOS
On the client systems, you will needs to install a few necessary packages to make authentication mechanism function correctly with an LDAP server.
Configure LDAP Client in Ubuntu 16.04 and 18.04
First start by installing the necessary packages by running the following command.
$ sudo apt update && sudo apt install libnss-ldap libpam-ldap ldap-utils nscd
During the installation, you will be prompted for details of your LDAP server (provide the values according to your environment). Note that the ldap-auth-config package which is auto-installed does the most of the configurations based on the inputs you enter.
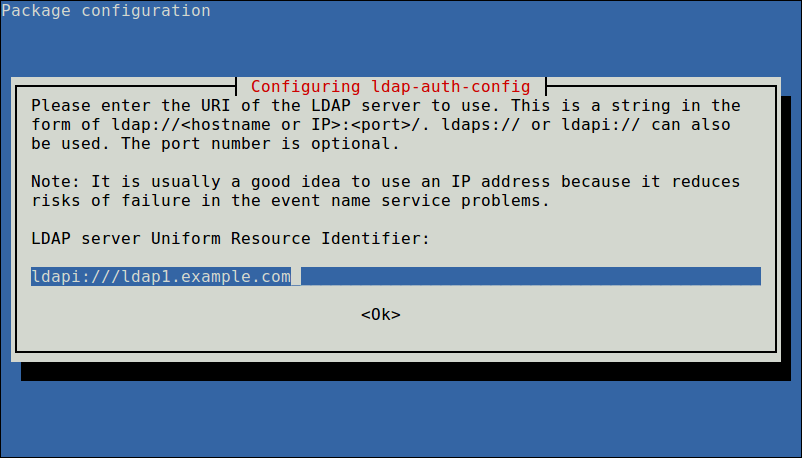
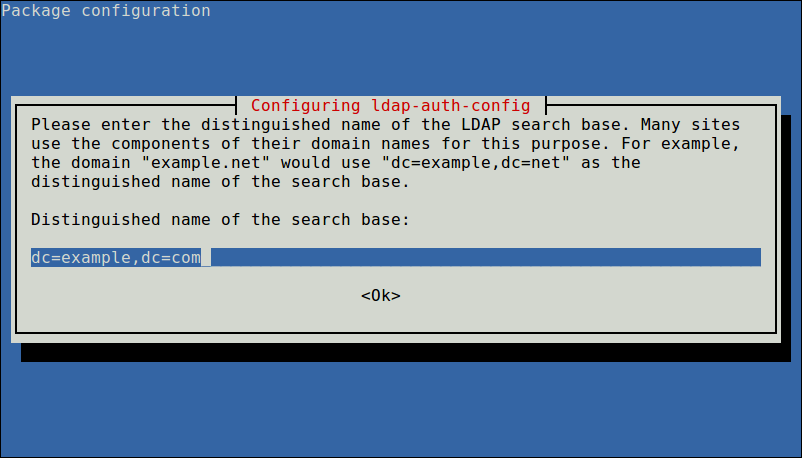
Next, enter the name of the LDAP search base, you can use the components of their domain names for this purpose as shown in the screenshot.
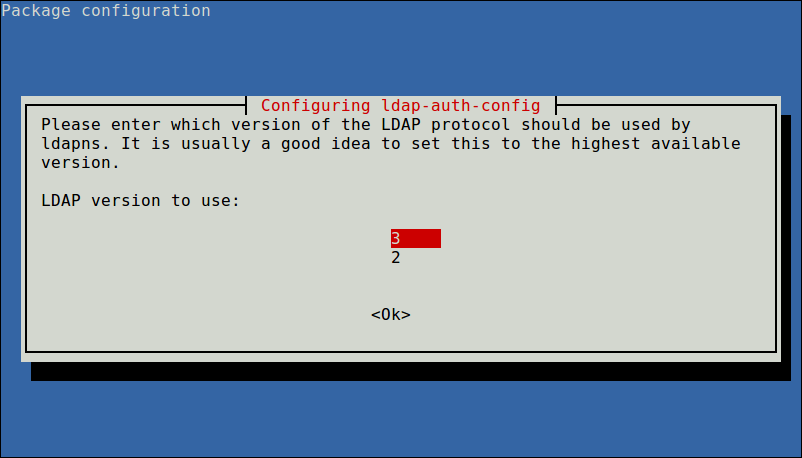
Also choose the LDAP version to use and click Ok.
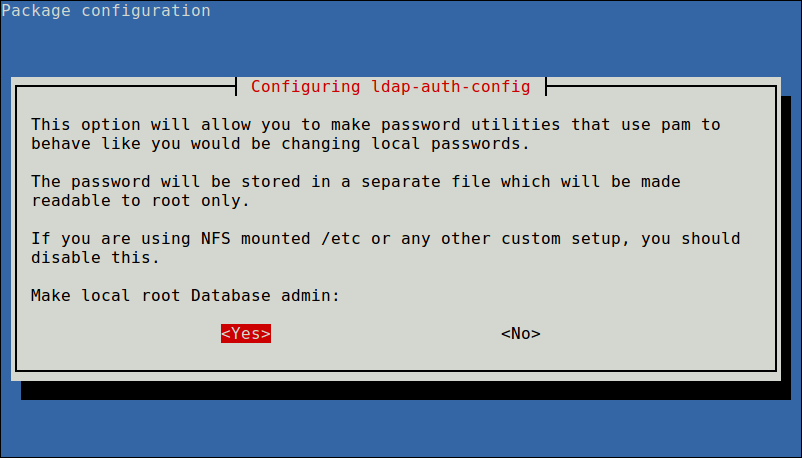
Now configure the option to allow you to make password utilities that use pam to behave like you would be changing local passwords and click Yes to continue..
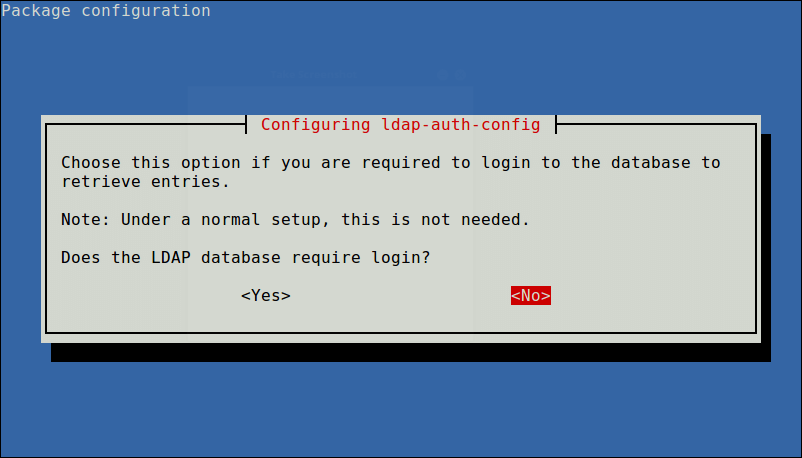
Next, disable login requirement to the LDAP database using the next option.
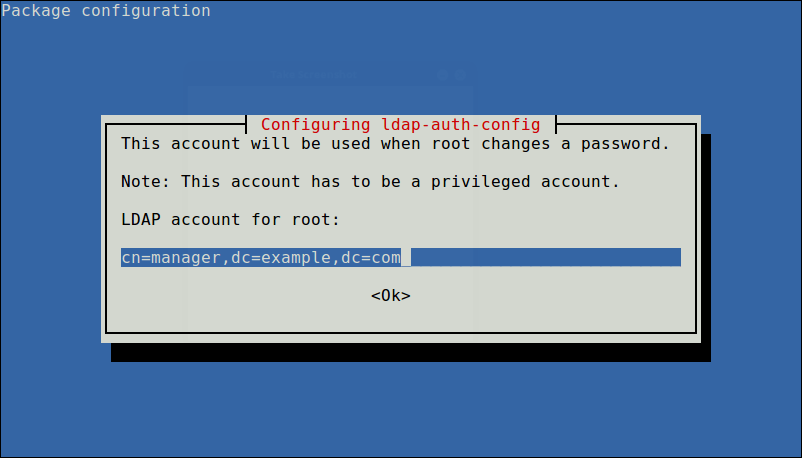
Also define LDAP account for root and click Ok.
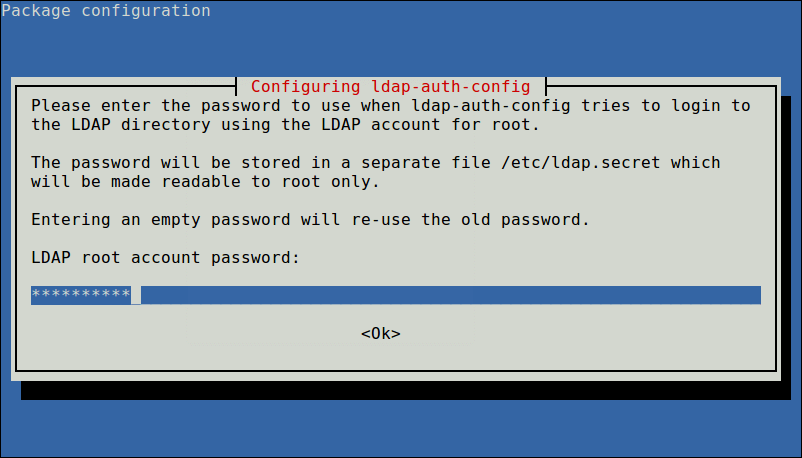
Next, enter the password to use when ldap-auth-config tries to login to the LDAP directory using the LDAP account for root.
The results of the dialog will be stored in the file /etc/ldap.conf. If you want to make any alterations, open and edit this file using your favorite command line editor.
Next, configure the LDAP profile for NSS by running.
$ sudo auth-client-config -t nss -p lac_ldap
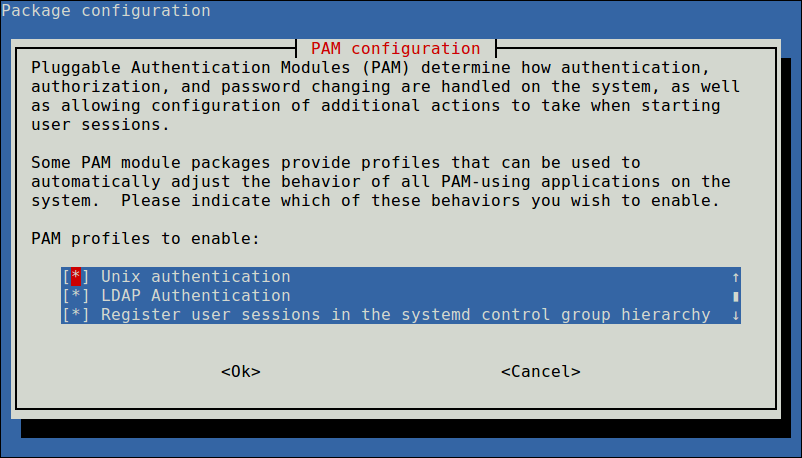
Then configure the system to use LDAP for authentication by updating PAM configurations. From the menu, choose LDAP and any other authentication mechanisms you need. You should now be able to log in using LDAP-based credentials.
$ sudo pam-auth-update
In case you want the home directory of the user to be created automatically, then you need to perform one more configuration in the common-session PAM file.
$ sudo vim /etc/pam.d/common-session
Add this line in it.
session required pam_mkhomedir.so skel=/etc/skel umask=077
Save the changes and close the file. Then restart the NCSD (Name Service Cache Daemon) service with the following command.
$ sudo systemctl restart nscd $ sudo systemctl enable nscd
Note: If you are using replication, LDAP clients will need to refer to multiple servers specified in /etc/ldap.conf. You can specify all the servers in this form:
uri ldap://ldap1.example.com ldap://ldap2.example.com
This implies that the request will time out and if the Provider (ldap1.example.com) becomes unresponsive, the Consumer (ldap2.example.com) will attempt to be reached to process it.
To check the LDAP entries for a particular user from the server, run the getent command, for example.
$ getent passwd tecmint
If the above command displays details of the specified user from the /etc/passwd file, your client machine is now configured to authenticate with the LDAP server, you should be able to log in using LDAP-based credentials.
Configure LDAP Client in CentOS 7
To install the necessary packages, run the following command. Note that in this section, if you are operating the system as a non-root administrative user, use the sudo command to run all commands.
# yum update && yum install openldap openldap-clients nss-pam-ldapd
Next, enable the client system to authenticate using LDAP. You can use the authconfig utility, which is an interface for configuring system authentication resources.
Run the following command and replace example.com with your domain and dc=example,dc=com with your LDAP domain controller.
# authconfig --enableldap --enableldapauth --ldapserver=ldap.example.com --ldapbasedn="dc=example,dc=com" --enablemkhomedir --update
In the above command, the --enablemkhomedir option creates a local user home directory at the first connection if none exists.
Next, test if the LDAP entries for a particular user from the server, for example user tecmint.
$ getent passwd tecmint
The above command should display details of the specified user from the /etc/passwd file, which implies that the client machine is now configured to authenticate with the LDAP server.
Important: If SELinux is enabled on your system, you need to add a rule to allow creating home directories automatically by mkhomedir.
For more information, consult the appropriate documentation from OpenLDAP Software document catalog.
Summary
LDAP, is a widely used protocol for querying and modifying a directory service. In this guide, we have shown how to configure an LDAP client to connect to an external authentication source, in Ubuntu and CentOS client machines. You can leave any questions or comments you may have using the feedback form below.








Hi Everyone,
I need your help in this situation. I had open the authconfig-tui utility with sudo privileges on the ldap server to check its configuration. After I was done I closed the authconfig-tui tool with the OK button instead of CANCEL button, and now I am not able to login to the LDAP server with the LDAP id. Do you have any suggestions, what has changed here?
Each time user logs in from the client system, it asks for password change and logouts immediately.
next login same thing repeats.
@sreekantha
Have you checked the error logs for any relevant messages?
Even I am getting the same error.
Note: I have replaced tecmint with prabhu.
When I logged in with putty, directly entering the username, I get the following.
After entering the correct password, the putty window will disappear
Can you please help
https://bugs.launchpad.net/ubuntu/+source/libpam-ldap/+bug/329067
This has an answer
Hi,
Can anyone help me -:
How to configure the LDAP client to authenticate via the OpenLDAP server.
Hi, can anyone help?
I am not getting any error messages nor the Success message after the “getent passwd tecmint” command on client-side.
I’m using CentOS 7 btw.
Thanks
Enter LDAP Server URI is not right. I spend 3 days to fix this error.
ldapi:/// => ldap://All of the guides have the same error.
@DongMK
Thanks for the useful feedback. We will cross-check this.
Hi, Does this work with a Windows application that requires validating users by LDAP? Should something else be configured?
I followed the guide yet I am getting the following error
su pranavsu: user pranav does not exist
Below command is not working fine for me on the Client
authconfig --enableldap --enableldapauth --ldapserver=ldap.example.com --ldapbasedn="dc=example,dc=com" --enablemkhomedir --updateI am not getting any error messages nor the Success message
Hi All
Please update the IP address of the LDAP Server During the authentication process this would resolve the issue.
Regards,
Pranav
Hi Pranav, what do you mean to update the IP address? how & where to do? thanks btw.
Hello,
Why root password must be stored in client machine ( i can see it is for changing password) only? Without root password client user on external machine can not log via ssh using LDAP DB and into Gnome .
On ubuntu 19.04 following these steps I get the error:
lokaal@silver-linux:~$ auth-client-config
auth-client-config: command not found
Invalid user test from localhost port 60074
Jul 2 17:49:28 localhost sshd[3413]: input_userauth_request: invalid user test [preauth]
Jul 2 17:50:07 localhost sshd[3413]: pam_unix(sshd:auth): check pass; user unknown
Jul 2 17:50:07 localhost sshd[3413]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser=
Jul 2 17:50:09 localhost sshd[3413]: Failed password for invalid user test from localhost port 60074 ssh2
Jul 2 17:50:18 localhost sshd[3413]: pam_unix(sshd:auth): check pass; user unknown
Jul 2 17:50:21 localhost sshd[3413]: Failed password for invalid user test from localhost port 60074 ssh2
@Vinay
Do you have the test user created on your system? You should use an existing username.
getent passwd tecmint has no output can you help me?
user home directories are not getting created
Client side doesn’t work for me either.
If I run the command:
for the server side or the client side I can retrieve information about ldap and it seems to be working.
But when I run on the client:
No user is created and therefore the command: getent passwd tecmint have no output at all.
Does anyone knows how to solve this?
ldap_sasl_bind(SIMPLE): Can’t contact LDAP server (-1)
I also followed that guide but when I login from the user on client machine, it is showing authentication error.
@Akshay
What error authentication error message do you get, please share with us.
I followed the guide without any error but its not working on client side.
@Ashok
What error are you getting exactly?