Lightweight Directory Access Protocol (LDAP in short) is an industry standard, lightweight, widely used set of protocols for accessing directory services. A directory service is a shared information infrastructure for accessing, managing, organizing, and updating everyday items and network resources, such as users, groups, devices, emails addresses, telephone numbers, volumes and many other objects.
The LDAP information model is based on entries. An entry in a LDAP directory represents a single unit or information and is uniquely identified by what is called a Distinguished Name (DN). Each of the entry’s attributes has a type and one or more values.
An attribute is a piece of information associated with an entry. The types are typically mnemonic strings, such as “cn” for common name, or “mail” for email address. Each attribute is assigned one or more values consisting in a space-separated list.
The following is an illustration of how information is arranged in the LDAP directory.
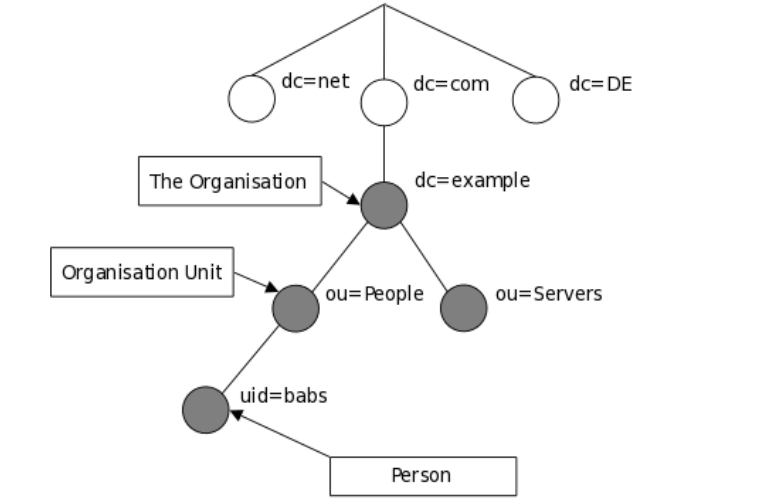
In this article, we will show how to install and configure OpenLDAP server for centralized authentication in Ubuntu 16.04/18.04 and CentOS 7.
Step 1: Installing LDAP Server
1. First start by installing OpenLDAP, an open source implementation of LDAP and some traditional LDAP management utilities using the following commands.
# yum install openldap openldap-servers #CentOS 7 $ sudo apt install slapd ldap-utils #Ubuntu 16.04/18.04
On Ubuntu, during the package installation, you will be prompted to enter the password for the admin entry in your LDAP directory, set a secure password and confirm it.
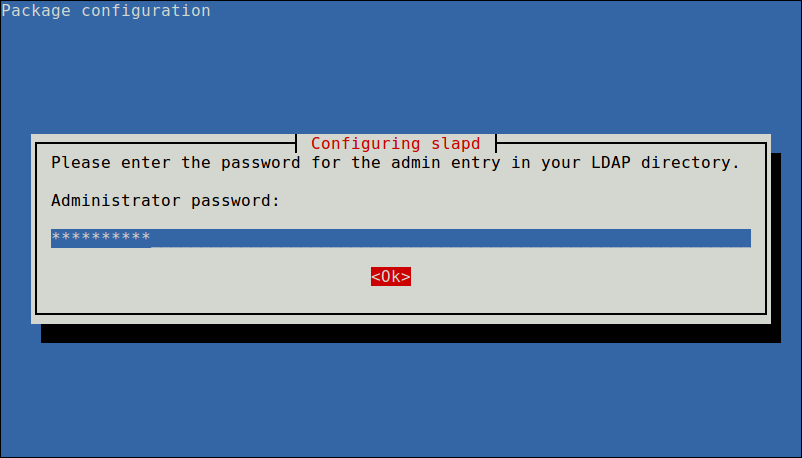
When the installation is complete, you can start the service as explained next.
2. On CentOS 7, run the following commands to start the openldap server daemon, enable it to auto-start at boot time and check if its up and running (on Ubuntu the service should be auto-started under systemd, you can simply check its status):
$ sudo systemctl start slapd $ sudo systemctl enable slapd $ sudo systemctl status slapd
3. Next, allow requests to the LDAP server daemon through the firewall as shown.
# firewall-cmd --add-service=ldap #CentOS 7 $ sudo ufw allow ldap #Ubuntu 16.04/18.04
Step 2: Configuring LDAP Server
Note: It is not recommended to manually edit the LDAP configuration, you need to add the configurations in a file and use the ldapadd or ldapmodify command to load them to the LDAP directory as shown below.
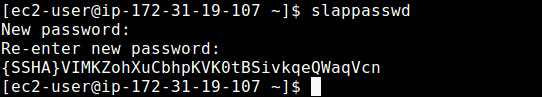
4. Now create a OpenLDAP administrative user and assign a password for that user. In the below command, a hashed value is created for the given password, take note of it, you will use it in the LDAP configuration file.
$ slappasswd
5. Then create an LDIF file (ldaprootpasswd.ldif) which is used to add an entry to the LDAP directory.
$ sudo vim ldaprootpasswd.ldif
Add the following contents in it:
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}PASSWORD_CREATED
explaining the attribute-value pairs above:
- olcDatabase: indicates a specific database instance name and can be typically found inside /etc/openldap/slapd.d/cn=config.
- cn=config: indicates global config options.
- PASSWORD: is the hashed string obtained while creating the administrative user.
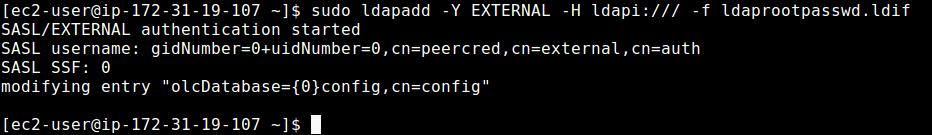
6. Next, add the corresponding LDAP entry by specifying the URI referring to the ldap server and the file above.
$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f ldaprootpasswd.ldif
Step 3: Configuring LDAP Database
7. Now copy the sample database configuration file for slapd into the /var/lib/ldap directory, and set the correct permissions on the file.
$ sudo cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG $ sudo chown -R ldap:ldap /var/lib/ldap/DB_CONFIG $ sudo systemctl restart slapd
8. Next, import some basic LDAP schemas from the /etc/openldap/schema directory as follows.
$ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif $ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif $ sudo ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
9. Now add your domain in the LDAP database and create a file called ldapdomain.ldif for your domain.
$ sudo vim ldapdomain.ldif
Add the following content in it (replace example with your domain and PASSWORD with the hashed value obtained before):
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth"
read by dn.base="cn=Manager,dc=example,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=example,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=example,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}PASSWORD
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by
dn="cn=Manager,dc=example,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=example,dc=com" write by * read
10. Then add the above configuration to the LDAP database with the following command.
$ sudo ldapmodify -Y EXTERNAL -H ldapi:/// -f ldapdomain.ldif
11. In this step, we need to add some entries to our LDAP directory. Create another file called baseldapdomain.ldif with the following content.
dn: dc=example,dc=com objectClass: top objectClass: dcObject objectclass: organization o: example com dc: example dn: cn=Manager,dc=example,dc=com objectClass: organizationalRole cn: Manager description: Directory Manager dn: ou=People,dc=example,dc=com objectClass: organizationalUnit ou: People dn: ou=Group,dc=example,dc=com objectClass: organizationalUnit ou: Group
Save the file and then add the entries to the LDAP directory.
$ sudo ldapadd -Y EXTERNAL -x -D cn=Manager,dc=example,dc=com -W -f baseldapdomain.ldif
12. The next step is to create a LDAP user for example, tecmint, and set a password for this user as follows.
$ sudo useradd tecmint $ sudo passwd tecmint
13. Then create the definitions for a LDAP group in a file called ldapgroup.ldif with the following content.
dn: cn=Manager,ou=Group,dc=example,dc=com objectClass: top objectClass: posixGroup gidNumber: 1005
In the above configuration, gidNumber is the GID in /etc/group for tecmint and add it to the OpenLDAP directory.
$ sudo ldapadd -Y EXTERNAL -x -W -D "cn=Manager,dc=example,dc=com" -f ldapgroup.ldif
14. Next, create another LDIF file called ldapuser.ldif and add the definitions for user tecmint.
dn: uid=tecmint,ou=People,dc=example,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: tecmint
uid: tecmint
uidNumber: 1005
gidNumber: 1005
homeDirectory: /home/tecmint
userPassword: {SSHA}PASSWORD_HERE
loginShell: /bin/bash
gecos: tecmint
shadowLastChange: 0
shadowMax: 0
shadowWarning: 0
then load fthe configuration to the LDAP directory.
$ ldapadd -Y EXTERNAL -x -D cn=Manager,dc=example,dc=com -W -f ldapuser.ldif
Once you have setup a central server for authentication, the final part is to enable the client to authenticate using LDAP as explained in this guide:
For more information, see the appropriate documentation from OpenLDAP Software document catalog and Ubuntu users can refer to the OpenLDAP server guide.
Summary
OpenLDAP is a open source implementation of LDAP in Linux. In this article, we have shown how to install and configure OpenLDAP server for centralized authentication, in Ubuntu 16.04/18.04 and CentOS 7. If you have a question or thoughts to share, do not hesitate to reach us via the comment form below.








It worked great.
Step 3 doesn’t work in Ubuntu 18.4.3. Error: No such file…
I had to solve the problem with:
and then followed instructions from another website. As this guide doesn’t seem to be updated.
@kante
Can you share the procedure you utilized to continue? I’m experiencing the same thing in Step 3.
Step 3.
Results in “no such file”
Tried to locate the file… there is no such file on the server.
Request to upload Documents for configuring the LDAP slave/replica server.
What if during the LFCE exam I get a request to spin up an open-ldap server? I will never remember by memory all of that text for the ldif files…
what are my options there? can’t access the internet to copy a template…?
Can I put my own template on Github and curl during the exam? Why for ubuntu is that easy with a “graphical” guided way? is there a package for centos that can do the same thing?
@unmerged
You can upload a template on Github, but curling it into the exam interface is a different thing altogether. It depends on the examination rules and regulations. If doing such a thing is allowed then it is actually possible. Thanks.
Try ldapscripts package: https://ubuntu.com/server/docs/service-ldap-usage
No wonder people Use Microsoft ADDS. OpenLDAP setup is not easy to understand steps. Even Powershell Installation of ADDS is easier.
The easy way is to use RedHat IPA.
You just type
ipa-server-install:)In step 11 I received “ldapadd incompatible with previous authentication choice” error. Removed
-Y EXTERNALand all was well. Step should read “sudo ldapadd -x -D cn=Manager,dc=example,dc=com -W -f baseldapdomain.ldif“@Randy
Many thanks for the useful feedback.
The openldap-clients package is missing from the installation instruction in step 1. Install openldap-clients (CentOS 7, RHEL 7) and the command “
sudo ldapmodify -Y EXTERNAL -H ldapi:/// -f ldapdomain.ldif” works just fine.I didn’t like the font used as an
land a1appear to be the same. In the ldaprootpasswd.ldif make sure to use a lower caseLvice a1for line1and 4 (olc) not (o1c).“ldap_bind: Invalid credentials (49)” if “-Y EXTERNAL” not used or else “ldapadd: incompatible with previous authentication choice”
The “example” from the LDAP command should be changed to the one with the one you have
"dc="on STEP 9.The password should the one generated with “slappasswd“.
Also in the baseldapdomain.ldif file, all “example” must be replaced with the one you set
"dc="in STEP 9.And yes remove
"-Y EXTERNAL"to avoid connection error.I think you should state that “example” should be replaced also in STEP 11 as you have mentioned in STEP 11.
In step 5. which folder will you create ldaprootpasswd.ldif in? I guess in /etc/ldap (I am a little bit confused since You mentioned /etc/openldap but it is not created, instead I have /etc/ldap.
I get the error:
ldappadd: wrong attributeType at line 4, entry "dn: olcDatabase={0}config,cn=config" when running the command sudo ldapadd -Y EXTERNAL -H ldapi:/// -f ldaprootpasswd.ldifTHERE IS NO SUCH USERS AS ‘ldap‘ IN STEP7!!! Nor is there any directories named /etc/openldap/.
The user and group for that command are both “openldap” (e.g.,
sudo chown -R openldap:openldap /var/lib/ldap/DB_CONFIG) Also, the directory should be “etc/ldap“.In step 3 I just get:
cp: cannot stat '/usr/share/openldap-servers/DB_CONFIG.example': No such file or directorywhat should I do?
@Anoobiz
Which distribution are you using, the file is normally provided with the package. Check if you have copied the correct command with the correct file path.
I’m getting “
ldapadd: incompatible with previous authentication choice“ error when typing “sudo ldapadd -Y EXTERNAL -x -D cn=Manager,dc=example,dc=com -W -f baseldapdomain.ldif“ in step 11, any help please?Remove the “-Y EXTERNAL” part and it’ll work.
I am doing it on RHEL 7 and getting following error:
# ldapadd -x -D cn=Manager,dc=vxindia.veritas,dc=com -W -f baseldapdomain.ldif Enter LDAP Password: adding new entry "dc=vxindia.veritas.com,dc=com" ldap_add: Server is unwilling to perform (53) additional info: no global superior knowledgeInstall openldap-clients for CentOS
openLDAP vs freeIPA
openLDAP
freeIPA
OpenLDAP vs Apache DS
OpenLDAP:
ApacheDS:
So many missing parts…
I’ve trusted you and you failed me.
ldapadd command not found
ldapadd: incompatible with previous authentication choice
In step 11 I had to remove
-Y EXTERNALto not get this error:This did work:
Thank you for the many times you helped me out already!
In step 10, when I run the command
ldapmodify -Y EXTERNAL -H ldapi:/// -f ldapdomain.ldif, I had this error : (ldap_modify : Invalid DN syntax(34) additional info: invalid DN).Help me please..
When i remove –
Y EXTERNALand run with correct password, I still get this error.In step 11.
sudo ldapadd -Y EXTERNAL -x -D cn=Manager,dc=example,dc=com -W -f baseldapdomain.ldifEnter LDAP Password: corret_password
ldap_bind: Invalid credentials (49)But : I got invalid credentials (49).
Anyone, please update on this query, I am also facing the same issue.
Enter LDAP Password:ldap_bind: Invalid credentials (49)
The same issue with CentOS Linux release 7.4 and openldap-servers 2.4.41.
No way to leap that step or to make it work.
When removing
-Y EXTERNALand with the correct password, I get: ldap_bind: Invalid credentials (49).When using
-Y EXTERNALonly I get: ldap_add: Server is unwilling to perform (53).additional info: no global superior knowledge
CentOS 7.6
OpenLDAP 2.4.44