This is our ongoing series on Linux Auditing, in this fourth part of this article, we will explain how to configure PAM for auditing of Linux TTY input (Logging Shell User Activity) for specific users using pam_tty_audit tool.
Linux PAM (Pluggable Authentication Modules) is a highly flexible method for implementing authentication services in applications and various system services; it emerged from the original Unix PAM.
It divides authentication functions into four major management modules, namely: account modules, authentication modules, password modules and session modules. The detailed explanation of theses management groups is beyond the scope of this tutorial.
The auditd tool uses the pam_tty_audit PAM module to enable or disable auditing of TTY input for specified users. Once a user is configured to be audited, pam_tty_audit works in conjunction with the auditd to track a users actions on the terminal and if configured, capture the exact keystrokes the user makes, then records them in the /var/log/audit/audit.log file.
Configuring PAM for Auditing User TTY Input in Linux
You can configure PAM for auditing a particular users TTY input in the /etc/pam.d/system-auth and /etc/pam.d/password-auth files, using the enable option. On the other hand, as expected, the disable turns it off for the specified users, in the format below:
session required pam_tty_audit.so disable=username,username2... enable=username,username2..
To turn on logging of actual user keystrokes (including spaces, backspaces, return keys, the control key, delete key and others), add the log_passwd option together with the other options, using this form:
session required pam_tty_audit.so disable=username,username2... enable=username log_passwd
But before you perform any configurations, note that:
- As seen in the syntax above, you can pass many usernames to the enable or disable option.
- Any disable or enable option overrides the previous opposite option that matches the same username.
- After enabling TTY auditing, it is inherited by all processes initiated by the defined user.
- If recording of keystrokes is activated, the input is not logged instantly, since TTY auditing first stores the keystrokes in a buffer and writes the buffer content at given intervals, or after the audited user logs out, into the /var/log/audit/audit.log file.
Let’s look at an example below, where we’ll configure pam_tty_audit to record the actions of the user tecmint including keystrokes, across all terminals, while we disable TTY auditing for all other system users.
Open these two following configuration files.
# vi /etc/pam.d/system-auth # vi /etc/pam.d/password-auth
Add following line to the configuration files.
session required pam_tty_audit.so disable=* enable=tecmint
And to capture all keystrokes entered by the user tecmint, we can add the log_passwd option a shown.
session required pam_tty_audit.so disable=* enable=tecmint log_passwd
Now save and close the files. Afterwards, view the auditd log file for any TTY input recorded, using the aureport utility.
# aureport --tty
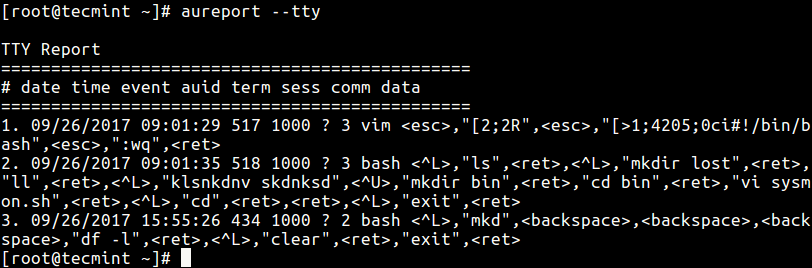
From the output above, you can see the user tecmint whose UID is 1000 used the vi/vim editor, created a directory called bin and moved into it, cleared the terminal and so on.
To search for TTY input logs recored with time stamps equal to or after a specific time, use the -ts to specify the start date/time and -te to set the end date/time.
The following are some example:
# aureport --tty -ts 09/25/2017 00:00:00 -te 09/26/2017 23:00:00 # aureport --tty -ts this-week
You can find more information, in the pam_tty_audit man page.
# man pam_tty_audit
Check out following useful articles.
- Configure “No Password SSH Keys Authentication” with PuTTY on Linux Servers
- Setting Up LDAP-based Authentication in RHEL/CentOS 7
- How to Setup Two-Factor Authentication (Google Authenticator) for SSH Logins
- SSH Passwordless Login Using SSH Keygen in 5 Easy Steps
- How to Run ‘sudo’ Command Without Entering a Password in Linux
In this article, we described how to configure PAM for auditing of input for specific users on CentOS/RHEL. If you have any questions or additional ideas to share, use the comment from below.