In our last article, we have explained how to audit RHEL or CentOS system using auditd utility. The audit system (auditd) is a comprehensive logging system and doesn’t use syslog for that matter. It also comes with a tool-set for managing the kernel audit system as well as searching and producing reports from information in the log files.
In this tutorial, we will explain how use ausearch tool to retrieve data from auditd log files on a RHEL and CentOS based Linux distributions.
Read Also: 4 Good Open Source Log Monitoring and Management Tools for Linux
As we mentioned earlier on, the auditing system has a user-space audit daemon (auditd) which gathers security-related information based on pre-configured rules, from the kernel and generates entries in a log file.
What is ausearch?
ausearch is a simple command line tool used to search the audit daemon log files based on events and different search criteria such as event identifier, key identifier, CPU architecture, command name, hostname, group name or group ID, syscall, messages and beyond. It also accepts raw data from stdin.
By default, ausearch queries the /var/log/audit/audit.log file, which you can view just like any other text file.
# cat /var/log/audit/audit.log OR # cat /var/log/audit/audit.log | less
From the screenshot above, you can see lots of data from the log file making it difficult to get specific information of interest.
Therefore you need ausearch, which enables searching of information in a more powerful and efficient way using the following syntax.
# ausearch [options]
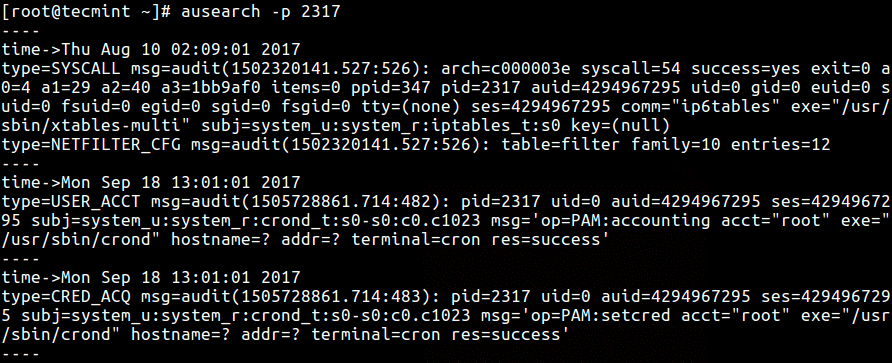
Check Running Process Logs in Auditd Log File
The -p flag is used to pass a process ID.
# ausearch -p 2317
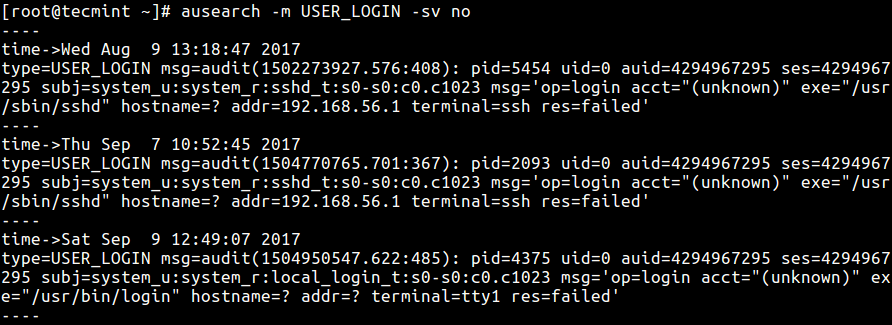
Check Failed Login Attempts in Auditd Log File
Here, you need to use the -m option to identify specific messages and -sv to define the success value.
# ausearch -m USER_LOGIN -sv no
Find User Activity in Auditd Log File
The -ua is used to pass a username.
# ausearch -ua tecmint OR # ausearch -ua tecmint -i # enable interpreting of numeric entities into text.
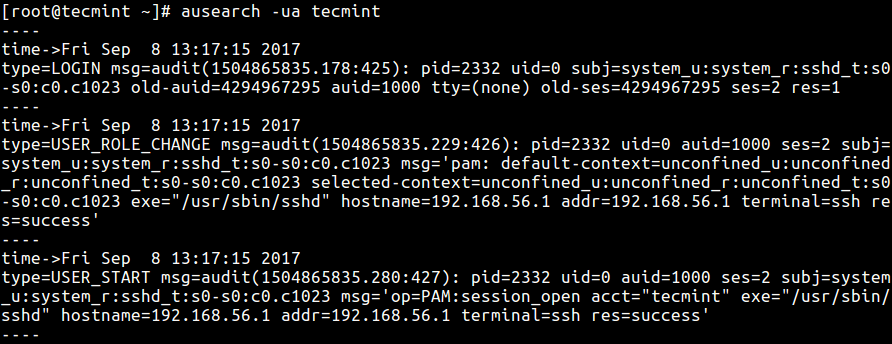
To query actions performed by a certain user from a given period of time, use the -ts for start date/time and -te for specifying end date/time as follows (note that you can use words such as now, recent, today, yesterday, this-week, week-ago, this-month, this-year as well as checkpoint instead of actual time formats).
# ausearch -ua tecmint -ts yesterday -te now -i
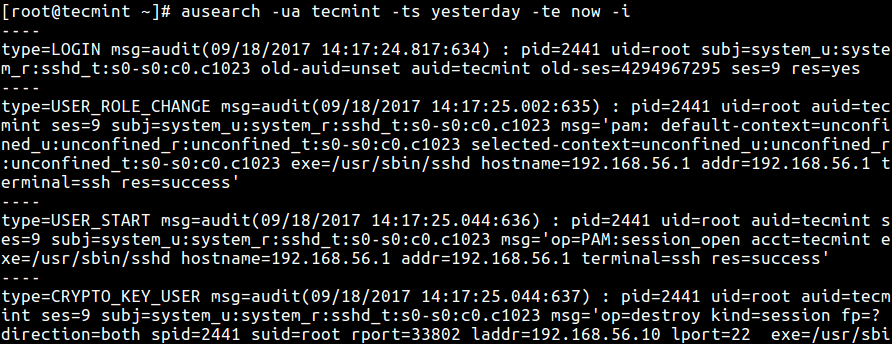
More examples on searching for actions by a given user on the system.
# ausearch -ua 1000 -ts this-week -i # ausearch -ua tecmint -m USER_LOGIN -sv no -i
Find Modifications to User Accounts, Groups and Roles in Auditd Logs
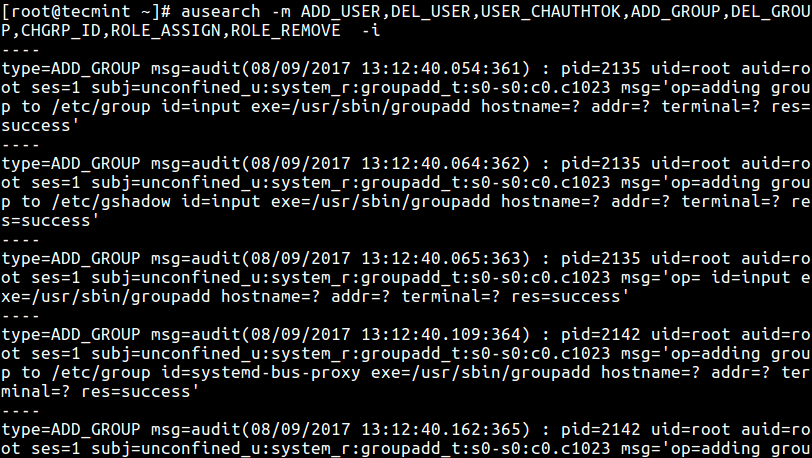
If you want to review all system changes to do with user accounts, groups and roles; specify various comma separated messages types as in the command below (take care of the comma separated list, leave no space between a comma and the next item):
# ausearch -m ADD_USER,DEL_USER,USER_CHAUTHTOK,ADD_GROUP,DEL_GROUP,CHGRP_ID,ROLE_ASSIGN,ROLE_REMOVE -i
Search Auditd Log File Using Key Value
Consider the audit rule below which will log any attempts to access or modify the /etc/passwd user accounts database.
# auditctl -w /etc/passwd -p rwa -k passwd_changes
Now, try to open the above file for editing and close it, as follows.
# vi /etc/passwd
Just because you know that a log entry has been recorded about this, you would possibly view the last parts of the log file with the tail command as follows:
# tail /var/log/audit/audit.log
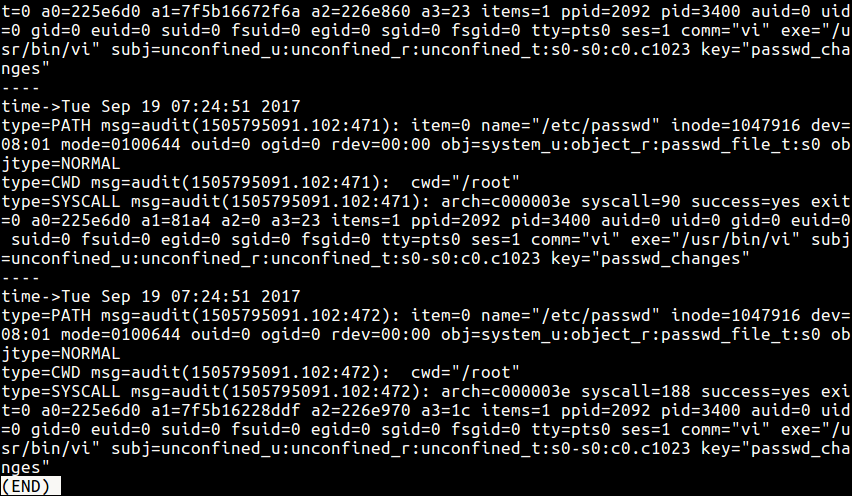
What if several other events have been recently recorded, finding the specific information would be so difficult, but using ausearch, you can pass the -k flag with the key value you specified in the audit rule to view all log messages concerning events to do with accessing or modifying /etc/passwd file.
This will also display the configuration changes made-defining of the audit rules.
# ausearch -k passwd_changes | less
For more information and usage options, read the ausearch man page:
# man ausearch
To know more about Linux system auditing and log management, read these following related articles.
- Petiti – An Open Source Log Analysis Tool for Linux SysAdmins
- Monitor Server Logs in Real-Time with “Log.io” Tool on RHEL/CentOS 7/6
- How to Setup and Manage Log Rotation Using Logrotate in Linux
- lnav – Watch and Analyze Apache Logs from a Linux Terminal
In this tutorial, we described how to use ausearch to retrieve data from an auditd log file on RHEL and CentOS. If you have any questions or thoughts to share, use the comment section to reach us.
In our next article, we’ll explain how to create reports from audit log files using aureport in RHEL/CentOS/Fedora.