There are so many benefits of using a VPN (Virtual Private Network), some of which include keeping you safe on the internet by encrypting your traffic and helping you to access blocked content/sites/web applications from anywhere. Not to mention, VPN also helps you to browse the internet anonymously.
In this article, you will learn how to quickly and automatically set up your own IPsec/L2TP VPN server in CentOS/RHEL, Ubuntu, and Debian Linux distributions.
Prerequisites:
- A fresh CentOS/RHEL or Ubuntu/Debian VPS (Virtual Private Server) from any provider such as Linode.
Setting Up IPsec/L2TP VPN Server in Linux
To set up the VPN server, we will use a wonderful collection of shell scripts created by Lin Song, that installs Libreswan as the IPsec server, and xl2tpd as the L2TP provider. The offering also includes scripts to add or delete VPN users, upgrade the VPN installation and much more.
First, log into your VPS via SSH, then run the appropriate commands for your distribution to set up the VPN server. By default, the script will generate random VPN credentials (pre-shared key, VPN username, and password) for you and display them at the end of the installation.
However, if you want to use your own credentials, first you need to generate a strong password and PSK as shown.
# openssl rand -base64 10 # openssl rand -base64 16
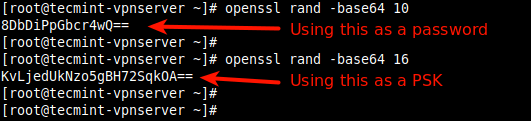
Next, set these generated values as described in the following command all values MUST be placed inside ‘single quotes‘ as shown.
- VPN_IPSEC_PSK – Your IPsec pre-shared key.
- VPN_USER – Your VPN username.
- VPN_PASSWORD – Your VPN password.
---------------- On CentOS/RHEL ---------------- # wget https://git.io/vpnsetup-centos -O vpnsetup.sh && VPN_IPSEC_PSK='KvLjedUkNzo5gBH72SqkOA==' VPN_USER='tecmint' VPN_PASSWORD='8DbDiPpGbcr4wQ==' sh vpnsetup.sh ---------------- On Debian and Ubuntu ---------------- # wget https://git.io/vpnsetup -O vpnsetup.sh && VPN_IPSEC_PSK='KvLjedUkNzo5gBH72SqkOA==' VPN_USER='tecmint' VPN_PASSWORD='8DbDiPpGbcr4wQ==' sudo sh vpnsetup.sh
The main packages that will be installed are bind-utils, net-tools, bison, flex, gcc, libcap-ng-devel, libcurl-devel, libselinux-devel, nspr-devel, nss-devel, pam-devel, xl2tpd, iptables-services, systemd-devel, fipscheck-devel, libevent-devel, and fail2ban(to protect SSH), and their respective dependencies. Then it downloads, compiles and installs Libreswan from source, enables and starts the necessary services.
Once the installation is complete, the VPN details will be displayed as shown in the following screenshot.
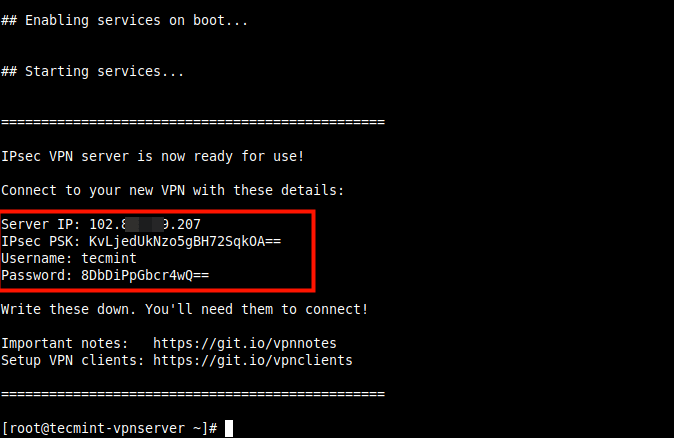
Next, you need to set up a VPN client, for desktops or laptops with a graphical user interface, refer to this guide: How To Setup an L2TP/Ipsec VPN Client on Linux.
To add the VPN connection in a mobile device such as an Android phone, go to Settings –> Network & Internet (or Wireless & Networks –> More) –> Advanced –> VPN. Select the option to add a new VPN. The VPN type should be set to IPSec Xauth PSK, then use the VPN gateway and credentials above.
How to Add or Remove a VPN User in Linux
To create a new VPN user or update an existing VPN user with a new password, download and use the add_vpn_user.sh script using the following wget command.
$ wget -O add_vpn_user.sh https://raw.githubusercontent.com/hwdsl2/setup-ipsec-vpn/master/extras/add_vpn_user.sh $ sudo sh add_vpn_user.sh 'username_to_add' 'user_password'
To delete a VPN user, download and use the del_vpn_user.sh script.
$ wget -O del_vpn_user.sh https://raw.githubusercontent.com/hwdsl2/setup-ipsec-vpn/master/extras/del_vpn_user.sh $ sudo sh del_vpn_user.sh 'username_to_delete'
How to Upgrade Libreswan Installation in Linux
You can upgrade the Libreswan installation using the vpnupgrade.sh or vpnupgrade_centos.sh script. Make sure to edit the SWAN_VER variable to the version you want to install, within the script.
---------------- On CentOS/RHEL ---------------- # wget https://git.io/vpnupgrade-centos -O vpnupgrade.sh && sh vpnupgrade.sh ---------------- On Debian and Ubuntu ---------------- # wget https://git.io/vpnupgrade -O vpnupgrade.sh && sudo sh vpnupgrade.sh
How to Uninstall the VPN Server in Linux
To uninstall the VPN installation, do the following.
On RHEL/CentOS
# yum remove xl2tpd
Then open /etc/sysconfig/iptables configuration file and remove the unneeded rules and edit /etc/sysctl.conf and /etc/rc.local file, and remove the lines after the comment # Added by hwdsl2 VPN script, in both files.
On Debian/Ubuntu
$ sudo apt-get purge xl2tpd
Next, edit /etc/iptables.rules configuration file and remove any unneeded rules. Additionally, edit /etc/iptables/rules.v4 if it exists.
Then edit /etc/sysctl.conf and /etc/rc.local files, remove the lines after the comment # Added by hwdsl2 VPN script, in both files. Do not remove exit 0 if it exists.
Optionally, you can remove certain files and directories that were created during the VPN set up.
# rm -f /etc/ipsec.conf* /etc/ipsec.secrets* /etc/ppp/chap-secrets* /etc/ppp/options.xl2tpd* /etc/pam.d/pluto /etc/sysconfig/pluto /etc/default/pluto # rm -rf /etc/ipsec.d /etc/xl2tpd
To set up a site-to-site IPSec-based VPN with Strongswan, check out our guides:
- How to Setup IPSec-based VPN with Strongswan on Debian and Ubuntu
- How to Setup IPSec-based VPN with Strongswan on CentOS/RHEL 8
Reference: https://github.com/hwdsl2/setup-ipsec-vpn
At this point, your own VPN server is up and running. You can share any queries or give us feedback using the comment form below.








Would this option allow us to support more than 1 connection at a time? Is there any other solution that would allow us to connect to two separate instances hidden behind a VPN simultaneously?
Hi, why only allows 1 connection? when i try to connect a second or third device it just not connect.
Thanks for your awesome work!
have you already solved this? I also need multiple connections.
I tried this tutorial so many times on a Ubuntu server 16 VM on Azure but it does not work. The VPN does not work on any device.
Can someone help, please?
Is it recommended to do this on an isolated server? After running I noticed it masks firewalld which broke some things, in particular Docker, though I was able to connect before reverting. I see hwdsl2 also has a docker image which I will probably try instead. Thanks for the article.
@Mark
Many thanks for this useful tip! You are right, this should be set up on a separate/fresh Linux server.
Hi, How can I put a limit to each account I make, in which for every one account there will be only one user who can use it at a time.
I created a VPN server but I was not able to connect it to my router because in LT2P protocol in my router I can’t find a place to inter PSKEY, is there any guide for to create an LT2P server without IPsec?
For what it’s worth, on an RHEL instance at least, the all-in-one command DOES NOT correctly set the variables for VPN_IPSEC_PSK, VPN_USER and VPN_PASSWORD.
When you run the script, you get the following output:
..and eventually randomized settings at the end.
Hi,
Your post above impressed me so much. I successfully built my VPN server.
And, how to list the current dial-in VPN users?
Good days,
This is all pretty cool but why go through all of this if you get a cheap premium VPN. I considered making my own VPN but got lazy and went for the PureVPN 7-day trial instead.
@betsy
Isn’t it nicer to run a VPN service that you fully have control over? Actually, this setup is fully automated, simply download and run the installation script, and after a few minutes, your VPN server will be up and running. But thanks for sharing your thoughts with us.
As for me, AlgoVPN is much more simple, secure, powerful and you can easily deploy it on any server and use wireGuard client.
@Oleh
Thanks for sharing, we didn’t know about AlgoVPN. We will check it out and write a guide about it.
“There are so many benefits of using a VPN (Virtual Private Network), some of which include keeping you safe on the internet by encrypting your traffic and helping you to access blocked content/sites/web applications from anywhere. Not to mention, VPN also helps you to browse the internet anonymously.”
The benefits only exist if the VPN server and the VPN clients are in different physical locations. Everything in the same location (ie home), grants no advantage. However, a VPN server at home will allow mobile equipment, like smartphones or portable computers, to access the internet at distance, at locations that otherwise would be insecure.
@Martins
Of course, the VPN server and client have to be in different locations, that is why we mentioned as a prerequisite: “A fresh CentOS/RHEL or Ubuntu/Debian VPS (Virtual Private Server) from any provider such as Linode.” Thanks for sharing your thoughts with us.
I want to learn about Linux because I think this will help me find a way of blocking Simcard in my country. VPN is going to down in my country by blocking the data if you exceed 1gb/day when you are using a VPN.
@Micheal
Learning Linux has many benefits, it will help you better understand how computers, networks work and also how the internet works. You can start right from here: https://www.tecmint.com/free-online-linux-learning-guide-for-beginners/
Does this restriction only apply to VPN use? That seems oddly specific. Perhaps it’s more a restriction on the Internet or tethering use?
Hi! Very useful article. Thanks!
I think: what about intensive traffic or how many users connected (on a standard VPS like Linode u$s30/mo plan?
@Kike
You can create many users as you like. Thanks for the useful feedback.
If I were going through the trouble of setting up my own VPN, it would be much better to avoid this out modded technology and choose something simple and much more likely to be secure like WireGuard.
@Henfre
True, we are actually actively using Wireguard: https://www.tecmint.com/wireguard-secure-vpn-tunnel-for-linux/, though it is still work in progress. Some users always prefer tested and proven options. But I believe Wiregaurd is a modern VPN solution for the future. Many thanks for your feedback.
I have to tell my problem here and is not related to the post above. I run in the latest version of Mint and I was somehow introduced to UKUU. After updating the kernel to the latest version, I lost the wifi driver am6d can’t work further on it. Please help.
@1501
Use UKUU to remove the mainline kernel. I believe it provides this option. If the source where you learned it from didn’t explain this, then we have to create a detailed guide about using UKUU. Thanks.