L2TP (which stands for Layer 2 Tunneling Protocol) is a tunneling protocol designed to support virtual private networks (VPN connections) over the internet. It is implemented in most if not all modern operating systems including Linux and VPN-capable devices.
The L2TP does not provide any authentication or encryption mechanisms directly to traffic that passes through it, it is usually implemented with the IPsec authentication suite (L2TP/IPsec) to provide encryption within the L2TP tunnel.
In this article, we will show how to set up an L2TP/IPSec VPN connection in Ubuntu and its derivatives and Fedora Linux.
This guide assumes that the L2TP/IPsec VPN server has been set up and that you have received the following VPN connection details from your organization’s or company’s system administrator.
Gateway IP address or hostname Username and Password Pre-shared Key (Secret)
How to Setup L2TP VPN Connection in Linux
To add an L2TP/IPsec option to the NetworkManager, you need to install the NetworkManager-l2tp VPN plugin which supports NetworkManager 1.8 and later. It provides support for L2TP and L2TP/IPsec.
To install the L2TP module on Ubuntu and Ubuntu-based Linux distributions, use the following PPA.
$ sudo add-apt-repository ppa:nm-l2tp/network-manager-l2tp $ sudo apt-get update $ sudo apt-get install network-manager-l2tp network-manager-l2tp-gnome
On RHEL/CentOS and Fedora Linux, use the following dnf command to install L2TP module.
# dnf install xl2tpd # dnf install NetworkManager-l2tp # dnf install NetworkManager-l2tp-gnome OR # yum install xl2tpd # yum install NetworkManager-l2tp # yum install NetworkManager-l2tp-gnome
Once the package installation is complete, click on your Network Manager icon, then go to Network Settings.
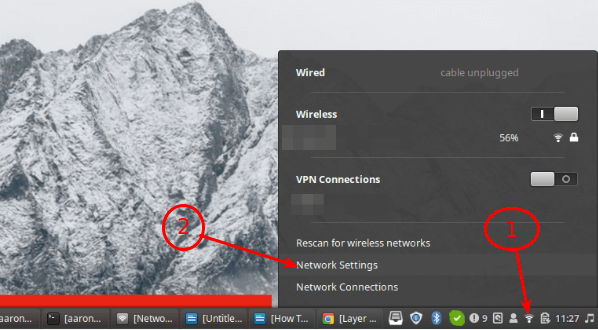
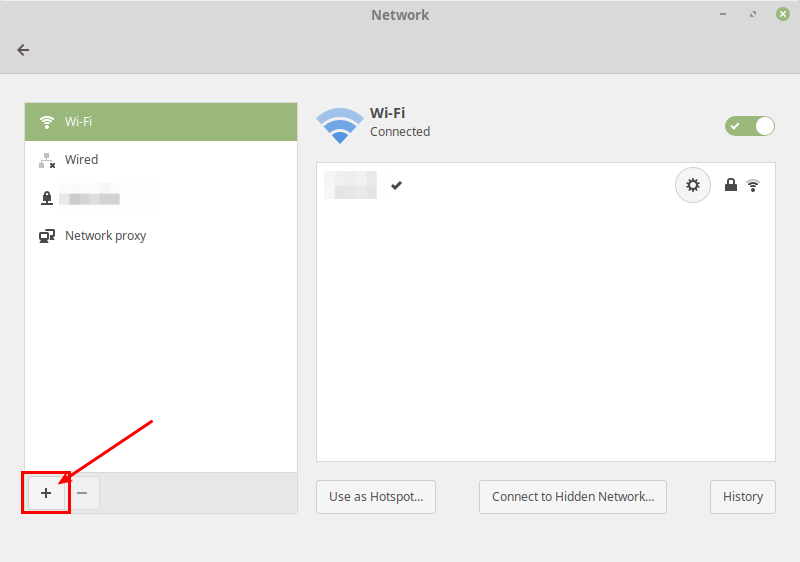
Next, add a new VPN connection by clicking on the (+) sign.
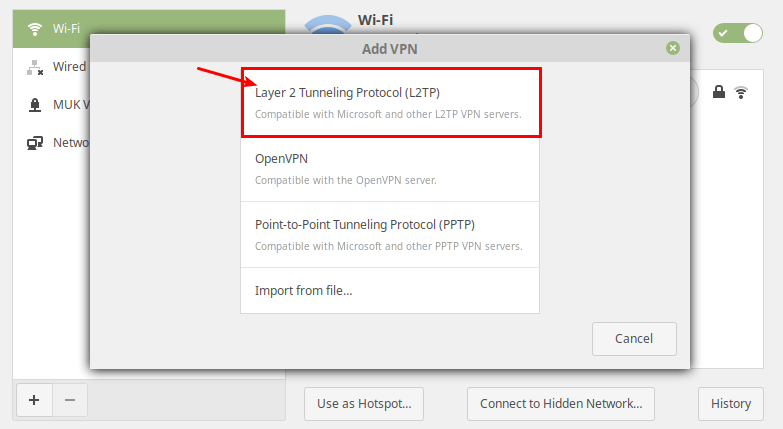
Then select Layer 2 Tunneling Protocol (L2TP) option from the pop-up window.
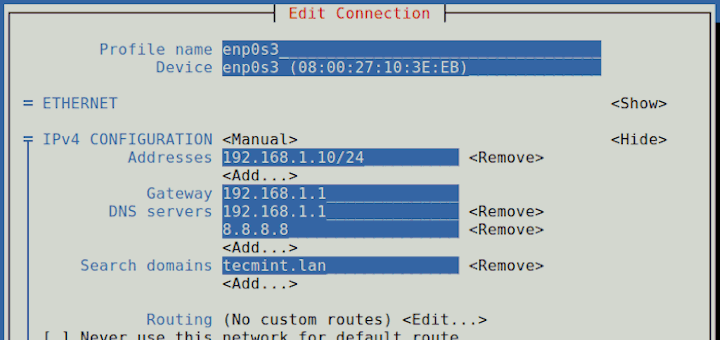
Next, enter the VPN connection details (gateway IP address or hostname, username and password) you received from the system administrator, in the following window.
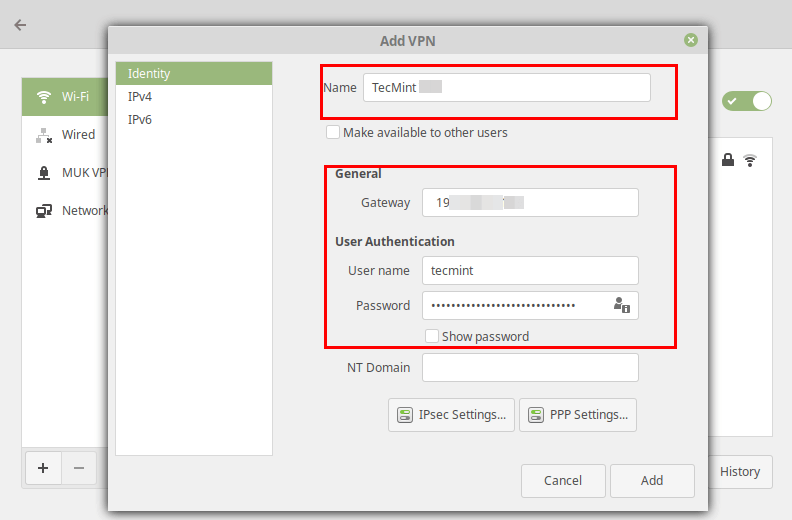
Next, click IPsec Settings to enter the pre-shared key for the connection. Then enable IPsec tunnel to L2TP host, enter (or copy and paste the) the Pre-shared key and click Ok.
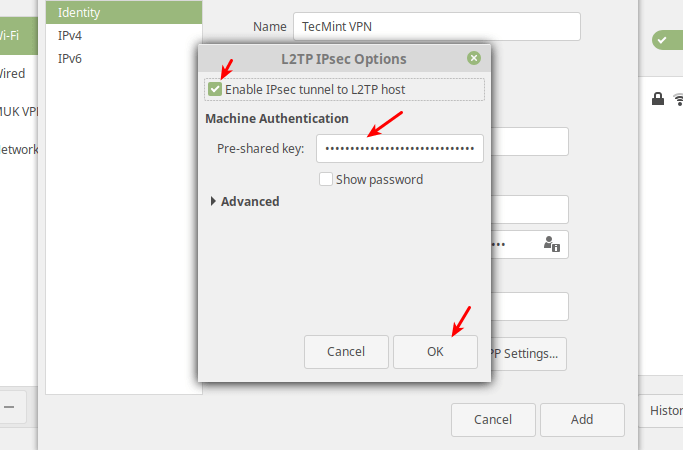
After that, click Add. Now your new VPN connection should be added.
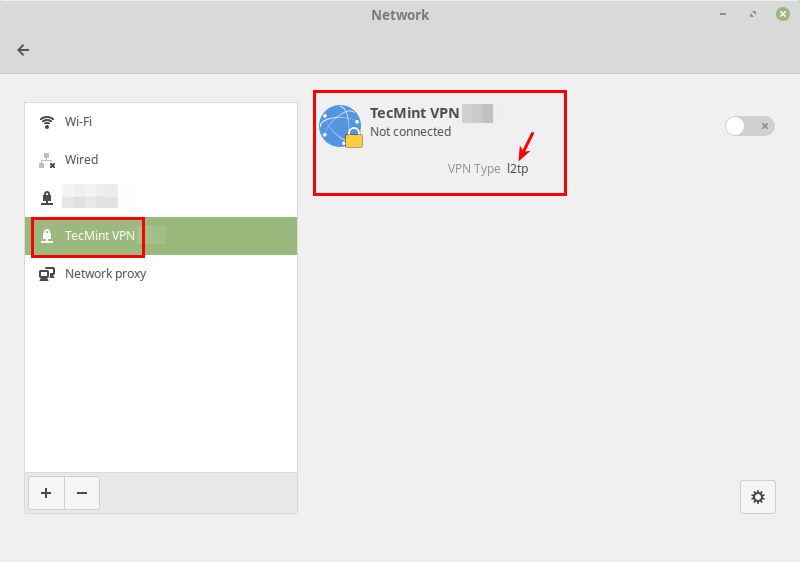
Next, turn on the VPN connection to start using it. If the connection details are correct, the connection should be established successfully.
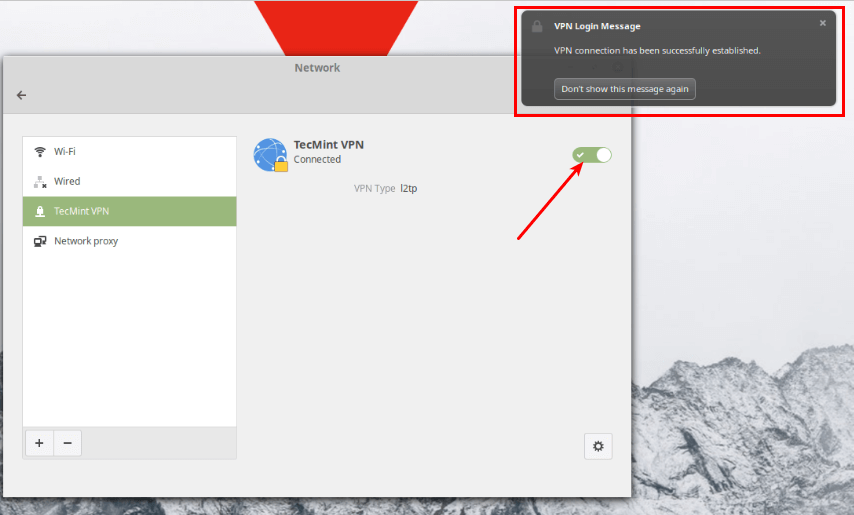
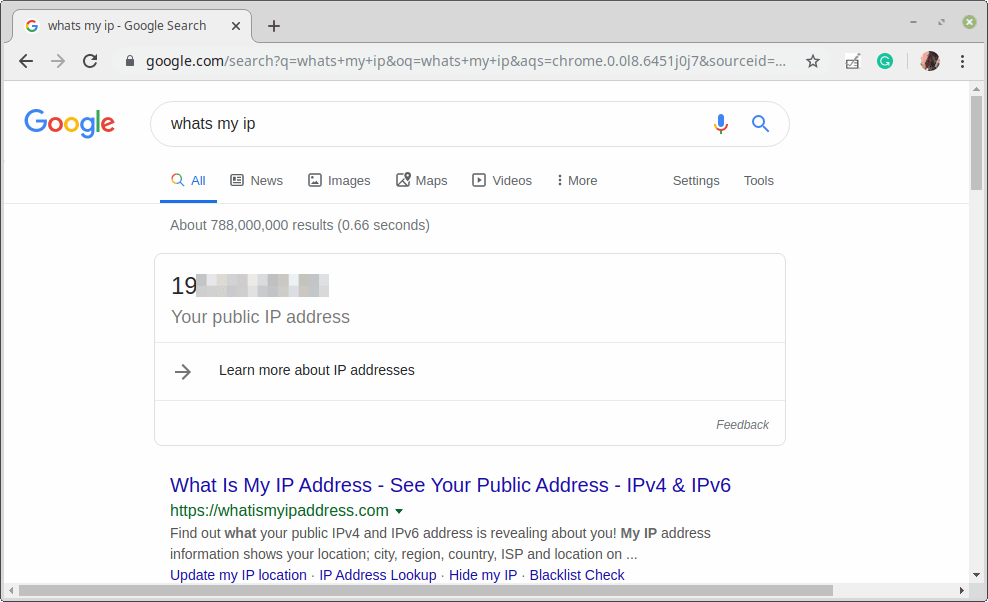
Last but not least, test if the VPN is working fine. You can check your computer’s public IP address to confirm this from a web browser: it should now point to the IP of the gateway.
That’s the end of this article. If you have any queries or thoughts to share, reach us via the feedback form below.


Hello
Is there the same instruction but for a linux server without GUI?
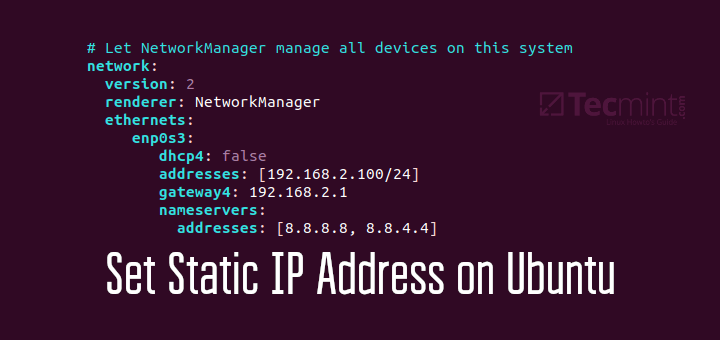
How can I set a static IP in Linux?
@Alexander,
Read this guide – How to Set Static IP Address and Configure Network in Linux
When configuring IPSEC, I have to set Phase1 algorithms to 3des-sha1-modp1024 and Phase1 algorithms to 3des-sha1 y Phase1 algorithms
Linux Mint Mate 19.3.
It doesn’t work for me, I’m trying to do it from Debian since Windows the VPN works.
Could You please help me? I’m new to Debian.
Its works for my Ubuntu 20.04 LTS.
God bless you,
Thank you so much,
I followed your steps but I have this error.
The L2TP connection attempt failed because the security layer encountered a processing error during initial negotiations with the remote computer.
@Grace
What error did you encounter? And is the VPN server running fine?
Hello, I set up the client from Ubuntu 20.04, and when I want to connect to Cisco Meraki, it never connects it, I made many setups trying this one work but it doesn’t work, what information do you need to solve this problem?
Can you write a post about how to do it only using terminal and without GUI?
@Moein,
You can use nmtui graphical command-line utility that allows you to easily configure your network interfaces in Linux distributions.
Can this be an alternative to Fortinet VPN client? Is it compatible with Fortinet IPSec?
@Derek
It should be, but we have never tried it out with Fortinet IPSec. You can give it a try.
Hello,
I have a problem with l2tp in Ubuntu 20.04. I connect to the VPN successfully. but within it, there are two networks and I can only access one of them.
From Windows 10 everything works correctly.
would you know what the problem is?
@Rodolfo
I can’t tell what the problem is now, we need to investigate this to find out the possible causes. You can also contact the developer/maintainers of NetworkManager-l2tp: https://github.com/nm-l2tp/NetworkManager-l2tp for more information. You probably want to raise an issue about this.
Do you know how to set up IPsec/XAuth VPN client in Fedora 31?
Hi, connect to L2TP/IPsec from GUI is simple. But how can I connect to L2TP/IPsec from server without GUI?
@m
We have to make a guide about this. Thanks for the feedback.
Hi Aaron,
same with me, I also need to connect to L2TP VPN from one of my Ubuntu Server
@M
Check out our new guides to setup a site-site VPN: https://www.tecmint.com/setup-ipsec-vpn-with-strongswan-on-debian-ubuntu/ and https://www.tecmint.com/setup-ipsec-vpn-with-strongswan-on-centos-rhel-8/
No, not in LINUX but in Ubuntu and Fedora-related distros only. Ubuntu and Fedora are not the alpha and omega of Linux. There are hundreds of other Linux distros that these instructions CANNOT be used for.
I am not asking for you to provide setup instructions for all other distros. All I am asking for is ‘truth in advertising’. If the article is specific to Ubuntu and Fedora, say so in the title. Otherwise, you are wasting the time of the millions of people who use distros other than those in Ubuntu/Fedora families.
I know that Tecmint would not intentionally give its articles click-bait titles.