In this short quick article, you will learn how to find all clients (using their IP addressees) connected to an Apache or Nginx web server on HTTP or HTTPS ports on a Linux server.
In Linux, every service running on the server listening to the socket for a client to make a connection request. Upon a successful connection from a client, a socket (a combination of an IP address and a port (a number which identifies an application/service the client is connected to)) is created.
Recommended Read: How to Watch TCP and UDP Ports in Real-time
To get the detailed information of these sockets, we will use a ss command-line tool, which is used to display network socket related information on a Linux machine. You can also use the older netstat command, which displays active socket connections.
For example, you can use these tools to get the socket statistics information of all clients connected to a specific port or service.
# ss OR # netstat
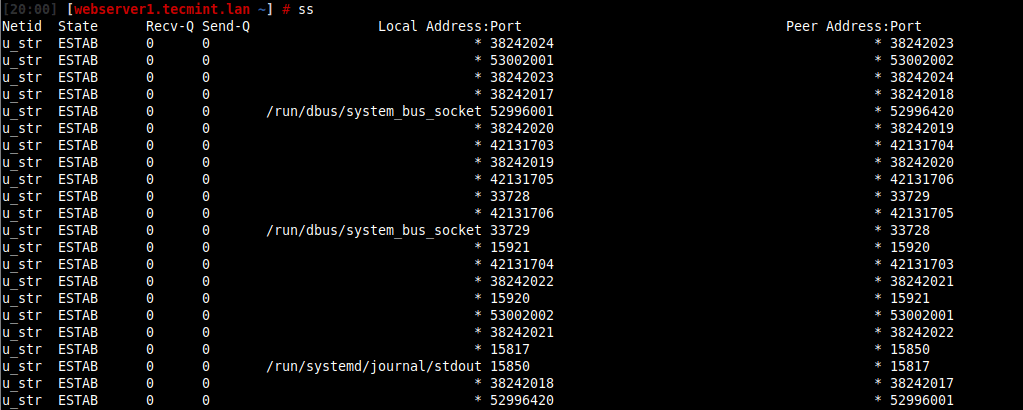
To get the list of all clients connected to HTTP (Port 80) or HTTPS (Port 443), you can use the ss command or netstat command, which will list all the connections (regardless of the state they are in) including UNIX sockets statistics.
# ss -o state established '( sport = :http or sport = :https )' OR # netstat -o state established '( sport = :http or sport = :https )'
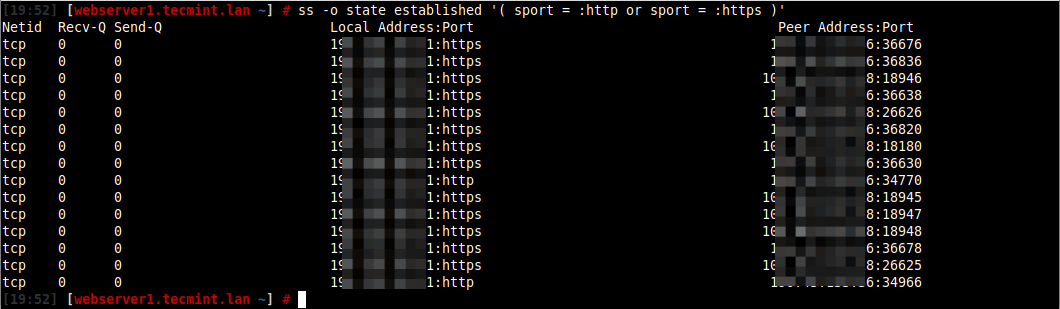
Alternatively, you can run the following command to list the numerical port numbers.
# ss -tn src :80 or src :443 OR # netstat -tn src :80 or src :443
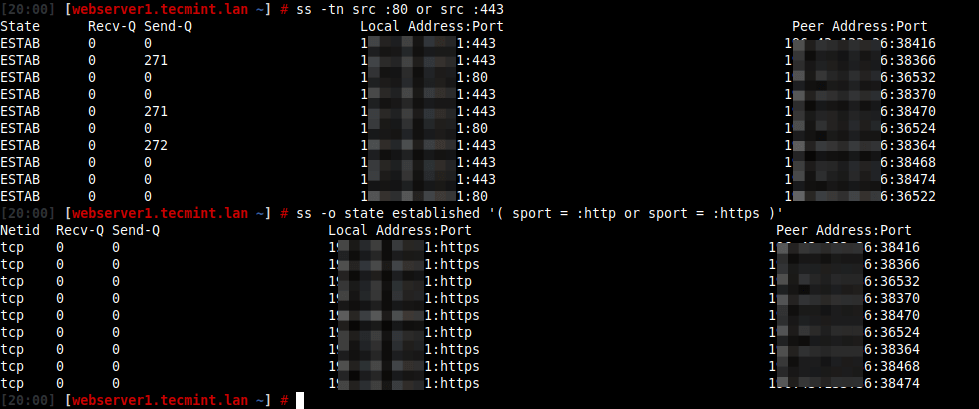
You might also find the following articles useful:
- 4 Ways to Find Out What Ports Are Listening in Linux
- How to Check Remote Ports are Reachable Using ‘nc’ Command
That’s all we have in this short article. For more information about the ss utility, read its man page (man ss). You can reach us for any questions, via the comment form below.




Hello great the day,
Every time I have used your “tecmint.com” site, always I got very easy and simple solutions from you, Thanks for your support…
Now I have been faced some issues with my server. I got more unwanted HTTP requests in my Nginx server when the time my server taking overload… at time domain was not working.
So I have stopped/restart my server then the domain is working properly so every time I have followed the same process.
Kindly suggest to me a feasible solution, to prevent this kind of situation.
Thanks
@Selvamohan,
You need to check the Nginx server logs to find out what IP address is requesting multiple numbers of requests and then block that IP.
@Ravi Saive
Thanks for your feedback, is there any other alternate/possible solution for it. Please suggest me.
May I know that How to configure for mail alert when the server received more/bulk requests?
Hello,
Is it possible to check a specific IP address if it’s connected or not?
For example, in the above example, it says you can check the connections toward a specific port. In this scenario, instead of port, we check the IP.