Network File System (NFS) also known as client/server file system is a popular, cross-platform and distributed file system protocol used to export local file systems over the network so that clients can share directories and files with others over a network and interact with them as though they are mounted locally.
In CentOS/RHEL 8, the supported NFS version are NFSv3 and NFSv4 and the default NFS version is 4.2 which features support for Access Control Lists (ACLs), server-side copy, sparse files, space reservation, labeled NFS, layout enhancements, and much more.
In this article, you will learn how to install and configure the NFS server and NFS client on CentOS/RHEL 8 Linux distributions.
Prerequisites:
- CentOS 8 Installation Guide
- RHEL 8 Minimal Installation
- Enable RHEL Subscription in RHEL 8
- Set a Static IP Address in CentOS/RHEL 8
Our Testing Environment:
NFS Server IP: 10.20.20.8 NFS Client IP: 10.20.20.9
Setting Up NFS Server on CentOS 8
1. First, start by installing the required packages on the NFS server. The packages are nfs-utils which provides a daemon for the kernel NFS server and related tools such as the contains the showmount program.
Run the following command to install the package on the NFS server (use sudo if you are administering the system as a non-root user).
# dnf install nfs-utils
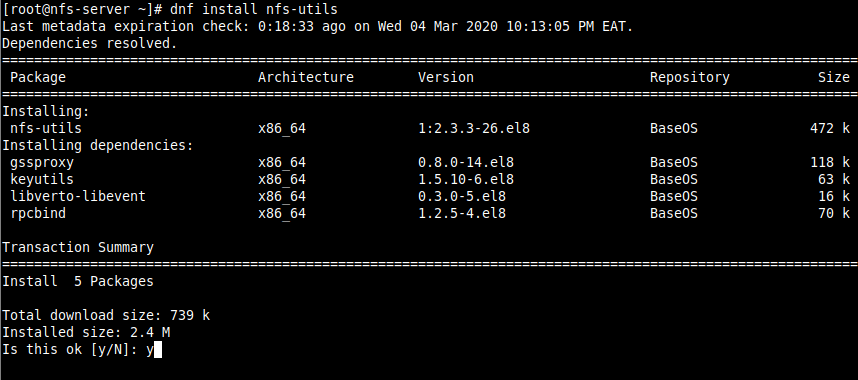
2. Once the installation is complete, start the nfs-server service, enable it to automatically start at system boot, and then verify its status using the systemctl commands.
# systemctl start nfs-server.service # systemctl enable nfs-server.service # systemctl status nfs-server.service
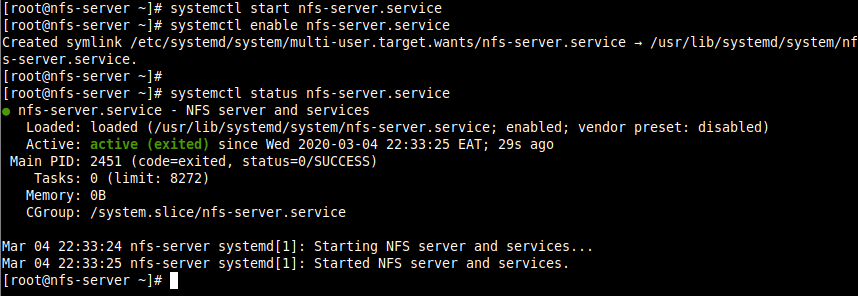
Note that the other services that are required for running an NFS server or mounting NFS shares such as nfsd, nfs-idmapd, rpcbind, rpc.mountd, lockd, rpc.statd, rpc.rquotad, and rpc.idmapd will be automatically started.
The configuration files for the NFS server are:
- /etc/nfs.conf – main configuration file for the NFS daemons and tools.
- /etc/nfsmount.conf – an NFS mount configuration file.
3. Next, create the file systems to export or share on the NFS server. For this guide, we will create four file systems, three of which are used by staff from three departments: human resource, finance and marketing to share files and one is for root user backups.
# mkdir -p /mnt/nfs_shares/{Human_Resource,Finance,Marketing}
# mkdir -p /mnt/backups
# ls -l /mnt/nfs_shares/
4. Then export the above file systems in the NFS server /etc/exports configuration file to determine local physical file systems that are accessible to NFS clients.
/mnt/nfs_shares/Human_Resource 10.20.20.0/24(rw,sync) /mnt/nfs_shares/Finance 10.20.10.0/24(rw,sync) /mnt/nfs_shares/Marketing 10.20.30.0/24(rw,sync) /mnt/backups 10.20.20.9/24(rw,sync,no_all_squash,root_squash)
Here are some of the exports options (read man exports for more information and export options):
- rw – allows both read and write access on the file system.
- sync – tells the NFS server to write operations (writing information to the disk) when requested (applies by default).
- all_squash – maps all UIDs and GIDs from client requests to the anonymous user.
- no_all_squash – used to map all UIDs and GIDs from client requests to identical UIDs and GIDs on the NFS server.
- root_squash – maps requests from root user or UID/GID 0 from the client to the anonymous UID/GID.
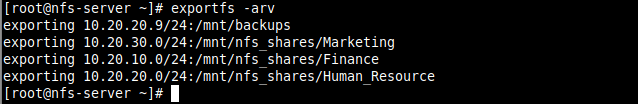
5. To export the above file system, run the exportfs command with the -a flag means export or unexport all directories, -r means reexport all directories, synchronizing /var/lib/nfs/etab with /etc/exports and files under /etc/exports.d, and -v enables verbose output.
# exportfs -arv
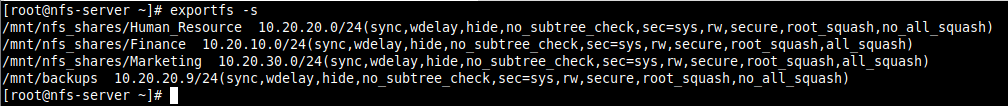
6. To display the current export list, run the following command. Note that the exports table also applies some of the default exports options that are not explicitly defined as shown in the following screenshot.
# exportfs -s
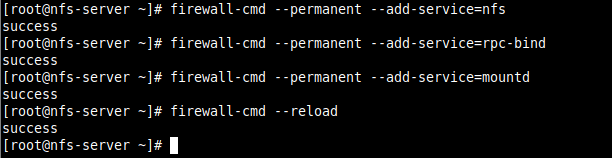
7. Next, if you have the firewalld service running, you need to allow traffic to the necessary NFS services (mountd, nfs, rpc-bind) via the firewall, then reload the firewall rules to apply the changes, as follows.
# firewall-cmd --permanent --add-service=nfs # firewall-cmd --permanent --add-service=rpc-bind # firewall-cmd --permanent --add-service=mountd # firewall-cmd --reload
Setting Up NFS Client on Client Systems
8. Now on the client node(s), install the necessary packages to access NFS shares on the client systems. Run the appropriate command for your distribution:
# dnf install nfs-utils nfs4-acl-tools [On CentOS/RHEL] $ sudo apt install nfs-common nfs4-acl-tools [On Debian/Ubuntu]
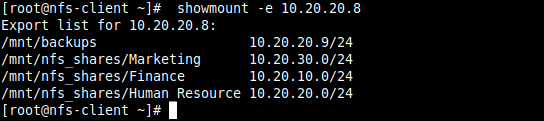
9. Then run the showmount command to show mount information for the NFS server. The command should output the exported file system on the client as shown in the screenshot.
# showmount -e 10.20.20.8
9. Next, create a local file system/directory for mounting the remote NFS file system and mount it as an ntf file system.
# mkdir -p /mnt/backups # mount -t nfs 10.20.20.8:/mnt/backups /mnt/backups
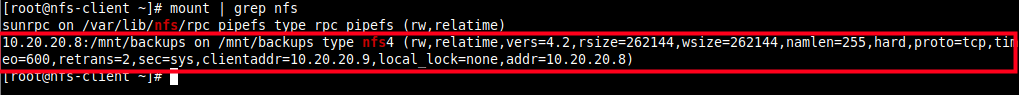
10. Then confirm that the remote file system has been mounted by running the mount command and filter nfs mounts.
# mount | grep nfs
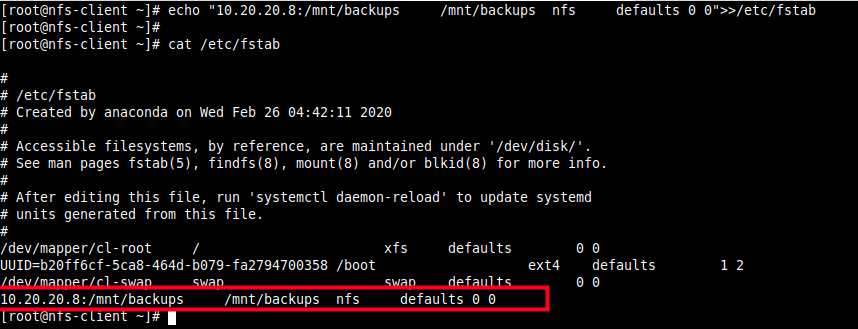
11. To enable the mount to persistent even after a system reboot, run the following command to enter the appropriate entry in the /etc/fstab.
# echo "10.20.20.8:/mnt/backups /mnt/backups nfs defaults 0 0">>/etc/fstab # cat /etc/fstab
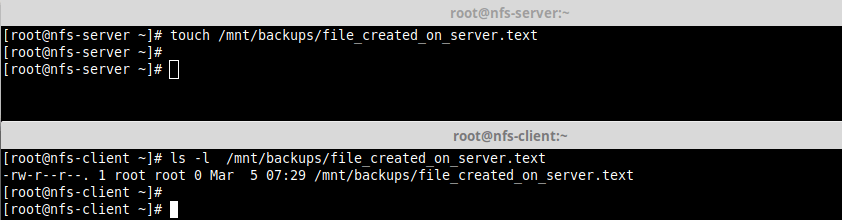
12. Lastly, test if NFS setup is working fine by creating a file on the server and check if the file can be seen in the client.
# touch /mnt/backups/file_created_on_server.text [On NFS Server] # ls -l /mnt/backups/file_created_on_server.text [On NFS client]
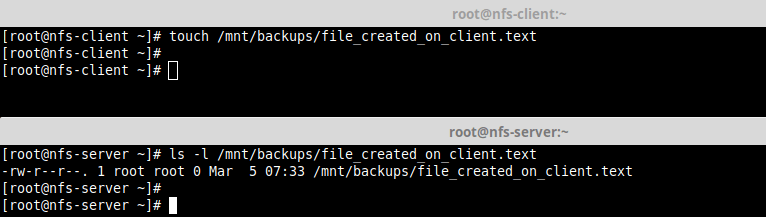
Then do the reverse.
# touch /mnt/backups/file_created_on_client.text [On NFS Client] # ls -l /mnt/backups/file_created_on_client.text [On NFS Server]
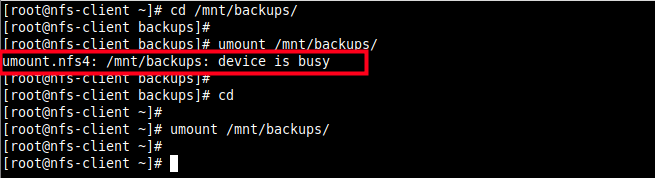
13. To unmount the remote file system on the client-side.
# umount /mnt/backups
Note that you can not unmount the remote file system if you are operating within it as shown in the following screenshot.
That’s it! In this guide, we showed how to install and configure an NFS server and client in CentOS/RHEL 8. If you have any thoughts to share or questions, use the comment form below to get back to us.








I find this site helpful and informative…
On CentOS 8 none of the steps above or in the comments seem to fix NFS permissions. I’ve tried root_squash, no_root_squash, all_squash, and made sure export is
rwfor my entire network. I still get access denied no matter what I do.I’m sure it is a filesystem issue on the server but this article does not cover anything related to that. It seems to be the one thing missing from all articles like this.
@C
Maybe the file permissions on the directory you are trying to access can cross-check to ensure that the NFS user has permissions to access/read/write in that directory.
Like I said – “I’m sure it is a filesystem issue on the server”.
What I mean is that none of the articles seem to specify what “sensible” permissions are. You can fix this by running “chmod -R 777” on the NFS share but that’s universally known to be bad practice.
Hi Aaron,
Thanks for quick documentation to set up NFS in no time.
I have one requirement, please suggest your thoughts.
Req:-
In AWS I want to use one of the ec2 Linux servers to be used as an NFS server. We will be using these two application VM’s as a shared drive.
I want to hear from you how can I achieve HA for this.
Regards,
Basu
@basavaraja
You can use tools such as Corosync and Pacemaker to configure HA, here is an example: https://www.tecmint.com/setup-high-availability-clustering-in-centos-ubuntu/
Hello, nice tutorial!
However I have a little issue. When I want to write into the backups folder with my user’s client, I can’t because I have no permission. How can I fix it?
@Quentin
What exports options have you set on the directory? That is where the issue is.
Hi Quentin,
I followed the steps and I had the same issue writing to the backup directory, upon further research I discovered that you have to use
no_root_squashinstead of theroot_squashthe author used in the/etc/fstabdirectory of the server. Do this and you’ll be able to write to the directory. Thanks to the author for this wonderful piece of article.@Ademola
We are glad that this guide helped you resolve the problem you were facing. Many thanks for the useful feedback.